“At least he’s consistent?”: Timothée Chalamet has actually dissed the opera before—twice
"I just KNOW a ballerina rejected him in 8th grade."
The Latest
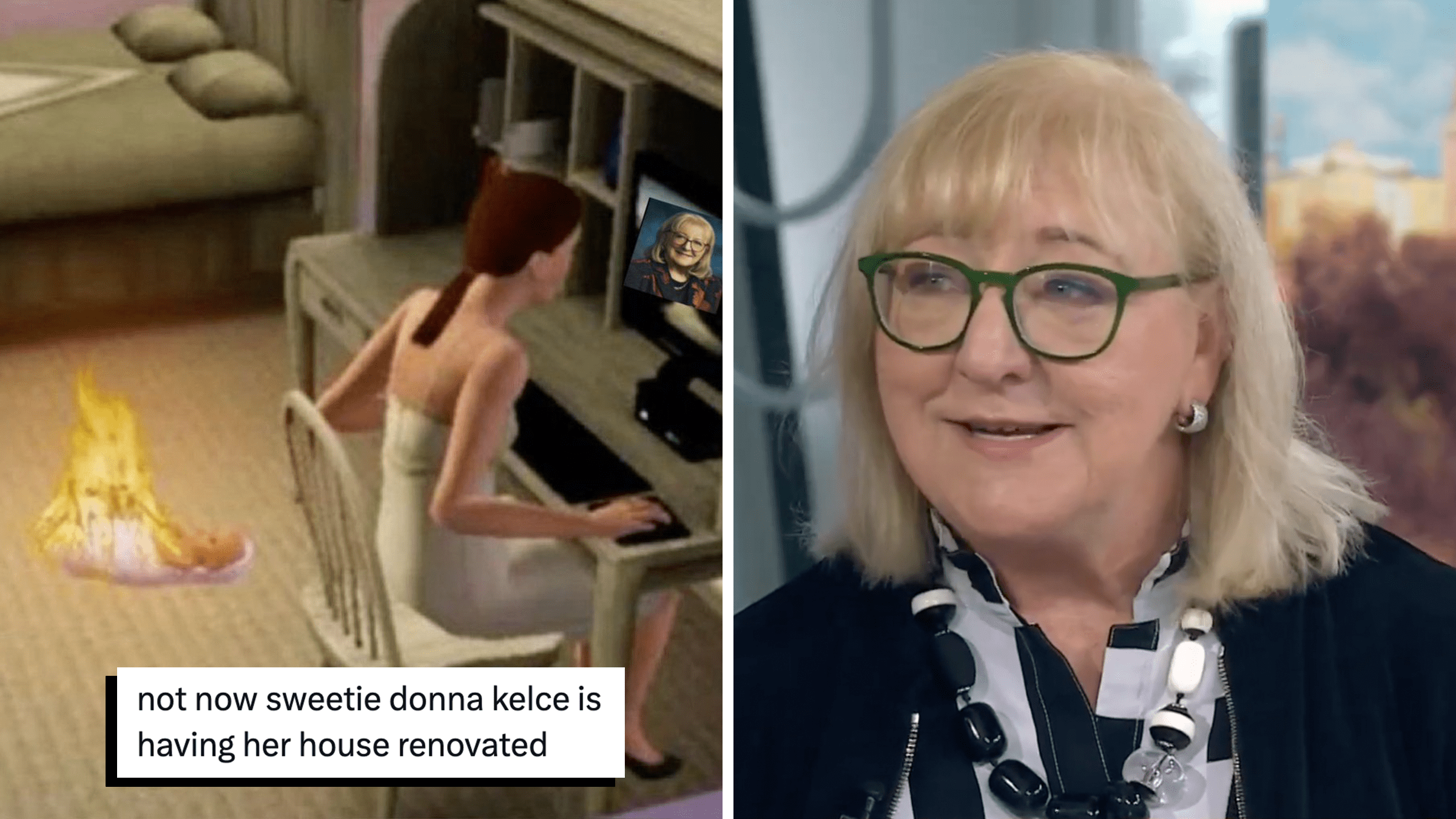
See all postsDonna Kelce’s home renovation becomes the meme we needed to face the horrors
"Does anyone have an update on Donna Kelce’s house situation, I’ve been worried about her doors and windows all weekend."
“Not even close”: New York’s JFK Jr. lookalike contest drew crowds—and some brutal commentary
"This just looks like every finance bro in Manhattan."
Kai Cenat shares footage of his “hate wall” filled with printed out comments from trolls
"I want to show you guys the power to embrace hate," he said.
“Called in all the favors”: Nicole Kidman reveals her iconic AMC spot was filmed for free
Bring back the longer version.
“Everyone loves this silly lil lizard”: The “Hoppers” collab in Fortnite is so popular, players are calling it an “industry plant”
Tom Lizard, you will always be famous.
“This is the traffic coming home from Disney”: Video shows miles of gridlock
The real Disney wait might be the drive back to your Airbnb.
Entertainment
How are fans reacting to the end of “Smiling Friends”? Not well.
"Check on your neurodivergent friends."
Fans want Caleb McLaughlin to play Miles Morales after “Stranger Things”
It's definitely a hot topic.
“Everything just looked terrifying”: No, that’s not Bill Clinton in “Ted”— why Seth MacFarlane’s AI-infused impression is sparking controversy
There were better alternatives.
“This one’s for you”: The Met responds after Timothée Chalamet claims “no one cares” about ballet and opera
Timothée Chalamet didn't know what kind of pot he was stirring.
Viral Politics
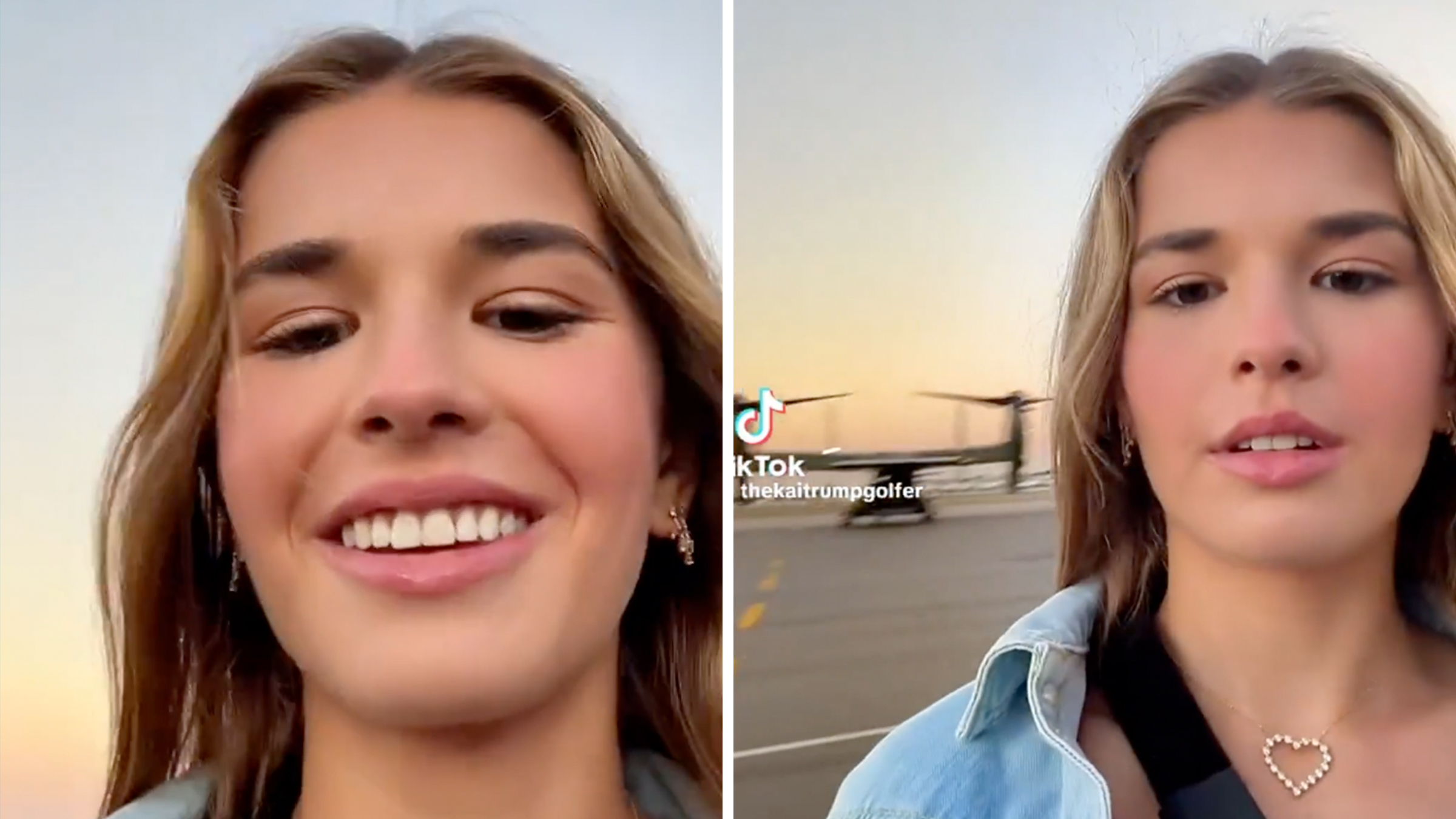
No, that video of Kai Trump on a runway isn’t a “war selfie” from the Iran conflict
"It's just a reminder that she's of legal age to sign up and serve her country."
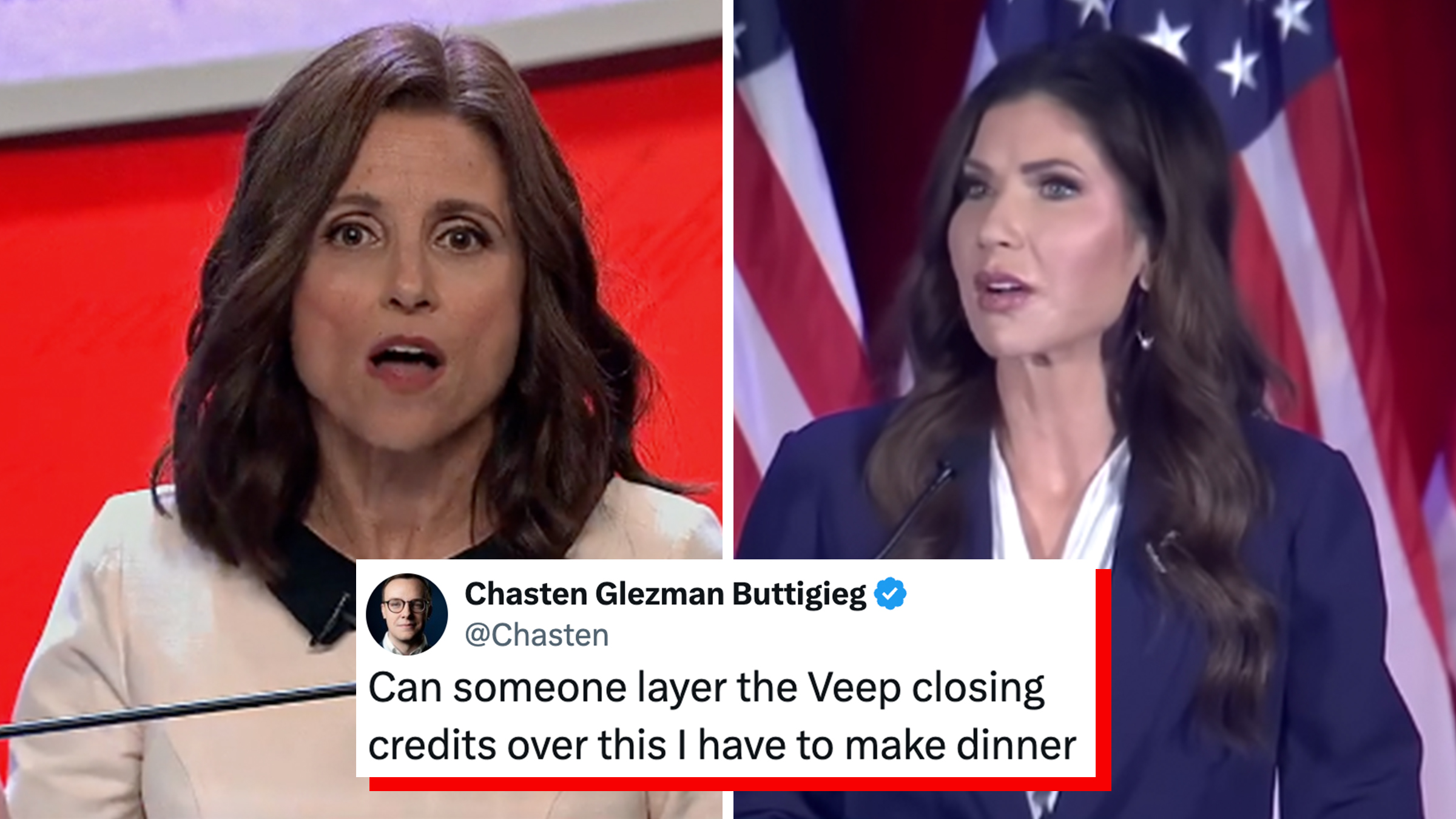
Kristi Noem’s final DHS speech gets the “Veep” end-credits treatment after Trump fires her
"I just spit out my Coke."
“Some people will die”: Trump says “I guess” when asked if Americans should fear Iranian attacks
"I’ve killed all their leaders," Trump said. "That room is gone."
“Lunatic behavior”: Marine vet protesting Iran war appears to snap a bone during struggle with GOP senator
"I'm here in D.C. trying to speak out against the Senate and ask them why they're going to send our men and women into harm's way."
Trending
“We bought this one for under $40K”: Woman who lives in a church teaches others how they can do the same
"I’d have to sage the hell out of it… But the stained glass could be nice."
“I thought I was going insane…”: Shopper compares Costco Babybel to Kroger version—and pulls out a scale
"There's a HUGE difference."
“Whole missing puzzle piece”: Woman hears one comment from a stranger. Then everything about her symptoms starts to make sense
"I just, randomly, like, twitch and I thought it was just an anxious habit."
“Nintendo’s lawyers will love this”: The Pokémon Company responds to White House Pokopia meme
The timeline could hardly get weirder.
Culture
“On-Together” coworking game turns remote work into a pastel, cozy experience with friends
"To those who love to have a space to work together virtually, certainly check this game out!"
“Let’s just make more jokes”: Zara Larsson doubles down after abortion joke backlash in viral TikTok
"It doesn’t have to be taboo."
Tucker Carlson’s anti-war merch is going viral among the very people who hate him
"He’s going to accidentally have a best seller on his hands."
Raw milk Redditors keep accidentally rediscovering pasteurization
"Just buy milk from the grocery store then."
Memes
“I thought I was tripping”: Fortnite players spotted a “terrifying” Kim Kardashian skin glitch
Kim K is bugging out.
New “Pokémon Winds and Waves” characters inspire memes and a “Republican” backstory
"Where was Boca Raton Pikachu on January 6th?"
Tyra Banks forcing models to pose with their trauma on “ANTM” inspires the “traumatic photo shoot” meme
"Reality Check: Inside America’s Next Top Model" is the newest meme-maker.
“Now I’m stressmaxxing”: Who is Androgenic? The viral wig snatch that’s dividing social media
"Now this looksmaxxing gymcel gets wig snatched?"
Tech
The next “Stardew Valley” update lets Clint get married, and the fandom is split over the “worst” character’s new upgrade
"I know he's a fixer-upper, but he has a job. And a beard. Which is more than I can say for a lot of these losers."
“Twitch really humbled her”: Doja Cat can’t figure out how to turn off livestream ads after new update
"You can win a Grammy, but you still can't skip the 30-second unskippable ad for insurance. Humbling for the ego!"
This startup says its $1,199 gadget can block listening devices. Skeptics are raising questions
"This would be extraordinary and would require equally extraordinary proof if true."
A new prank targeting Meta glasses wearers claims they’ll be banned if they look at a flag. It’s wrong.
"I just tried it, nothing happened."
TikTok
“That’s not 3 cups”: Woman measures boxed mac and cheese. The numbers on the package don’t add up
"I'm so tired of being ripped off."
What is the “Adam Driver bar?” How the actor set a new standard in voiceovers
That's one way to set the bar...
“Didn’t even last 12 minute”: RFK Jr. went to a Gold’s Gym in Austin and people on both sides of him roasted him
"Yes he was wearing jeans."
Influencer buys wedding dress while single. Now men are flooding her DMs
"Do I feel a little crazy being as single as I am? Yeah. But it was a great deal."