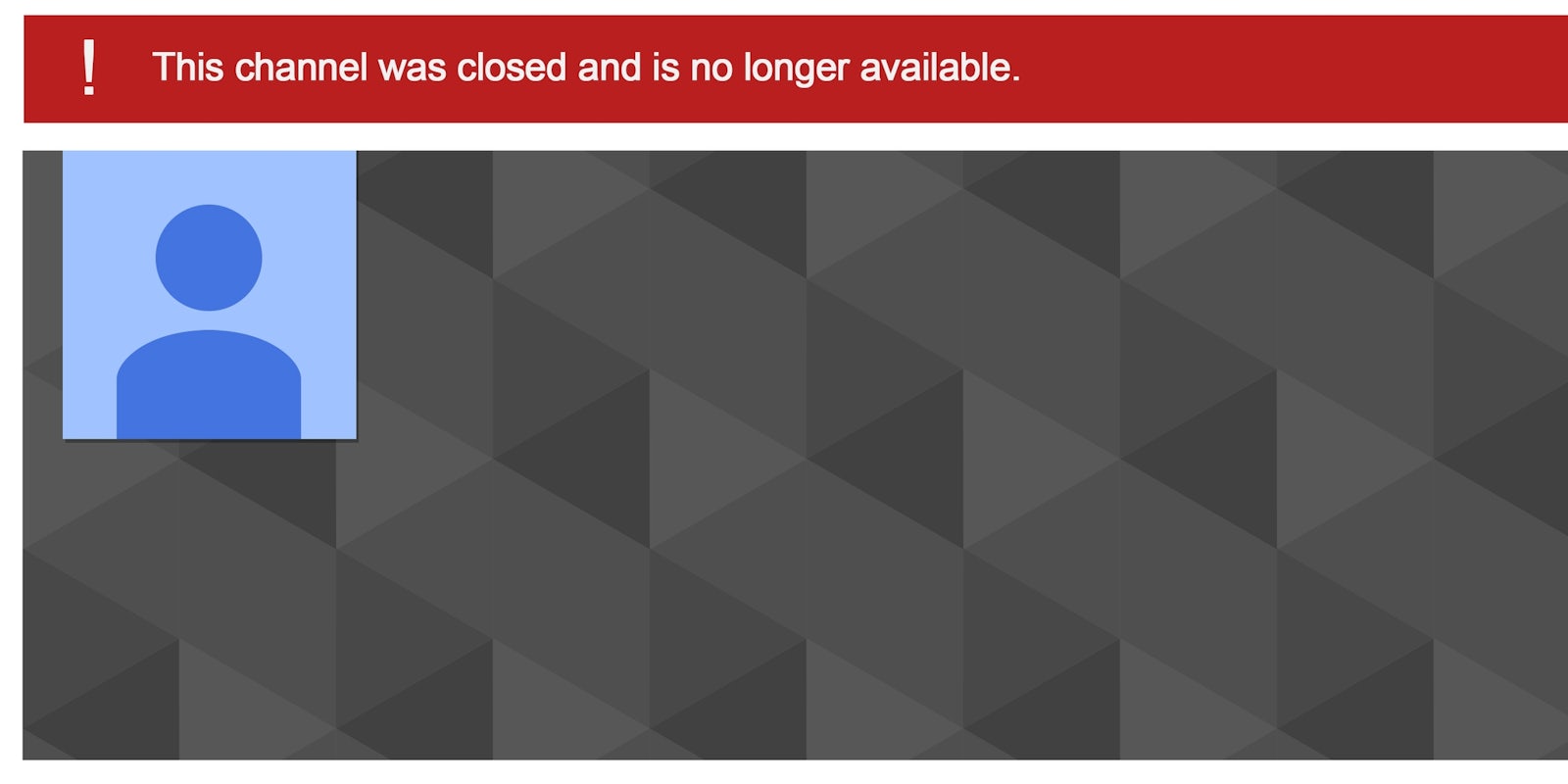
Late one night I woke up and checked my phone to discover one of my worst nightmares had come true. My email address had been taken over, as had all of my other social media. My YouTube channel with 3.5 million subscribers had been deleted. My PayPal account had been raided. I was locked out of everything. To make matters worse, my phone simply no longer worked, telling me the handset was not connected to a phone number.
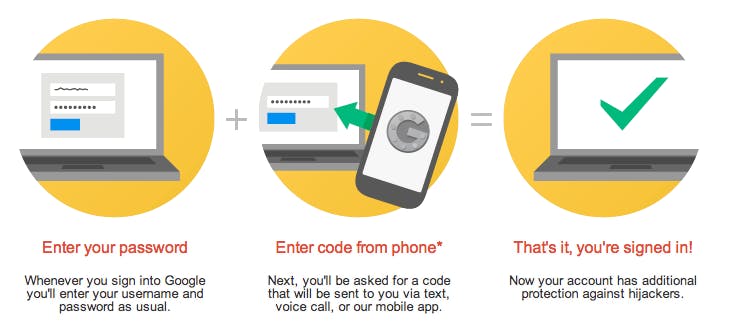
Up until that point, I thought I was entirely secure. I changed my passwords frequently and they were always 16–20 letters and numbers with special characters. I never used a password a second time. I even used two-step authentication to basically turn my cell phone into an authentication key. Not only did these steps fail to prevent me from being hacked, but using two-step authentication turned out to be my biggest weakness.
The hacker used what is known as “social engineering” to convince my phone provider, Verizon, to give him all of my information. While he did not have my social security number or my special passcode that I had set up as additional security with Verizon, they let him in anyway.
The hacker instructed the Verizon representative to change my phone number from my Samsung to his old burner phone. Once the rep had done this, the hacker basically had my cellphone in his hand and the cellphone next to me had become a worthless brick. He used that device to recover and change the password to my email address and once he had that,… he had everything. I had used the same email as the recovery address for my YouTube channel and my PayPal. That was enough for him to do irrevocable damage to everything I had built.
First, he changed the passwords to everything. He then began to put his “calling card” and hacker name onto everything. He found my secondary and tertiary emails that I used to keep things a little safer and changed passwords on those. He changed the recovery email addresses. He locked me out of all of my social media and began tweeting links to video game gambling websites to earn money.
In less than an hour, this young hacker managed to destroy what took me over a decade to build.
At some point, his goals became more nefarious. Perhaps it’s because I had woken up and caught on to what was happening and began trying to recover my accounts. He responded by doing what many hackers would consider unthinkable; he began deleting everything. My YouTube account… gone. My Gmail address… deleted. He began to dismantle my career piece by piece.
In less than an hour, this young hacker managed to destroy what took me over a decade to build. Every follower, every subscriber, every video: all of it destroyed in matters of minutes. My wife was frantically attempting to get ahold of someone from Verizon to get my phone number back while I desperately attempted to stave off the damage but it was too late.
The damage was already done.
To make matters worse, I was away from home. I was actually at the online video convention VidCon when all of this went down. In less than six hours I was supposed to speak in front of 500 people and moderate a panel called “Trolls in the Dungeon” about what it was like to deal with hate on the internet. My first thought was, “Why did this have to happen at VidCon?” But then I realized that I was at the safest and best place for this to happen. Everyone who was anyone at YouTube or Google was at the convention. Finding a real-life person to help would be quite easy. Plus, I had just been given the best story possible for my panel about trolls.
Every YouTuber that heard about my plight reached out to me; they contacted their reps at their networks and before long most of VidCon knew what had happened and were either offering their condolences or their help. After my panel, another YouTuber told me that he’d managed to find a member of the Google engineering team on my behalf. His name was Jeff and after a few hours of hard work we were on the right track.
Jeff taught me quite a lot about what I had done wrong to allow the hacker to have this kind of power over me. He pointed out some big mistakes I had made: using the same email address as the recovery email for everything and having this be a public email address. He taught me how to make a “chain” of recovery email addresses that used emails that would never be published anywhere.
Jeff and the Google team spent their last day at VidCon putting my channel back online, and within the week, I had access to my YouTube channel again. I was able to upload and monetize again and, fortunately, my business was back on track.
However, there was a lot of stuff the Google team could not help me do.
PayPal had been raided but luckily they managed to freeze the assets when they realized something was wrong. I had been locked out of my own account, though, and it took hours on the phone to regain access.
Just being notable on the internet can make you a target.
My Twitter, Instagram, Facebook, and other social media had been taken over, and on that day I learned how difficult it was to actually regain access to these things after an attack. Reaching an actual human at these companies is next to impossible. Fortunately, I “knew a guy who knew a guy” who was able to get me these accounts back after a few weeks and calling in a few favors.
Of course, not everyone has these connections available to them. And a few months later there are still some accounts and services that I’ll never be able to regain. I have considered them abandoned, and they have the name of my hacker floating on them as a badge of his success.
After all of this, I found the hacker who claimed to do all of this and saw his screenshots proving the legitimacy of his claim. I followed him on Twitter and, to my surprise, he followed me back and we had a conversation.
The hacker explained to me that he chose me simply because I was “famous” and that doing these things to me would either net him monetary gain or fame. He might be able to sell my accounts or at the very least, attach the attack to his hacker call sign and gain credit, giving him influence within his community. He actually apologized for any inconvenience he had caused me.
The hacker explained to me that he chose me simply because I was “famous.”
One day after the attack, we checked our email and found personal information about our hacker provided by a fan who also happened to be in private security. We knew exactly who had dismantled our lives in only a matter of minutes: a 17-year-old kid who had done all of this from his high school computer lab. I thought I was secure but my entire business had been dismantled by someone who was still wet behind the ears.
It turns out that just being notable on the internet can make you a target. The more successful you are, the more likely you are to be targeted. As you gain notoriety on the web as a content creator, you must take your security very, very seriously. If you’re visible to your fans, you’re valuable to a hacker.
I learned from this experience is that no one is truly secure. What we consider to be secure can actually be dismantled within minutes by hackers using the latest techniques and software. There exists a hidden website on the deep web that every hacker dumps information as it’s discovered, and it is shared by thousands of hackers who will nip at your security looking for a weak spot.
You most certainly should continue to do the basics, however.
- Use long complicated passwords that you change frequently.
- Use a different password for everything.
- Choose smart security questions with smart answers and be careful about with your private information.
- Avoid fishy emails.
- Do not use your public email address as a recovery email.
- Use two-step authentication, but use a phone number that you give to no one, or use an app that is only on your phone, such as Google Authenticator. For this purpose, I got a prepaid phone with a low monthly cost that does not need my name to be attached to it.
As a content creator, you must be vigilant against these hackers. They could target you for money, fame, or both. Include security in the routine maintenance of your business. It’s the only way to keep the nightmare of losing everything from becoming your reality.
Steven “Boogie2988” Williams is a gamer and popular vlogger. You can follow him on Twitter and YouTube.
The Internet Creators Guild is gathering stories from creators to understand their perspectives working professionally online. If you’re a creator who has been hacked, share your story with us on Twitter@ICGuild or at info@internetcreatorsguild.com, so we can continue to raise awareness of vulnerabilities, research ways for creators to increase security, and work with platforms to streamline the process of recovering accounts.
ICG Members have access to a growing knowledge base of resources, answered questions from an active community of creators, and a weekly podcast featuring interviews with creators big, small, and in between.
If you would like to become a member of the ICG, explore this topic in-depth, and support our cause, membership is $60 per year.