The Daily Dot strives to be considered in the same breath as NPR, the Guardian, and the Associated Press. Getting hacked by the Syrian Electronic Army was not exactly what we had in mind.
Last night, the SEA gained access to our content management system and a couple of email addresses, after posing as one of our contributors. The group deleted an article it had taken issue with (it’s since been restored) and left its mark on a scheduled story that had not yet been published. The changes were quickly reverted, and all accounts were reset.
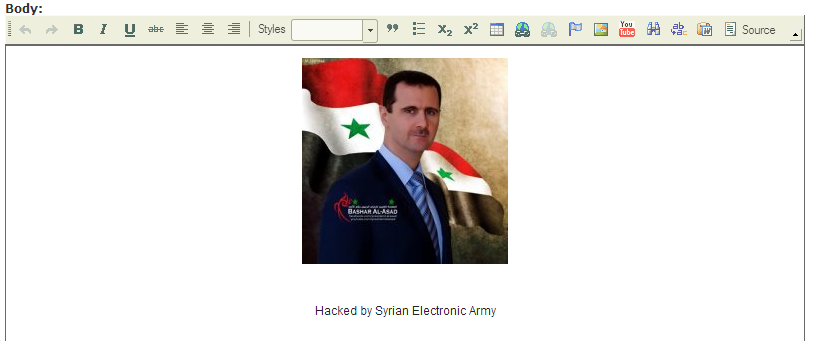
The SEA took offense to the portrayal of Syrian President Bashar al-Assad in a report on the group’s hacking of Tango.me, a messaging app with over 120 million users globally. The original illustration portrayed al-Assad in the mold of Adolf Hitler.
Dear @dailydot, please remove the attached picture in this article: https://t.co/mnuTVumSTD or we will do something you will not like it.
— SyrianElectronicArmy (@Official_SEA12) July 22, 2013
Upon review, the editorial staff concluded that it was a little much and updated the story with a new image, a caricature of al-Assad by Flickr cartoonist DonkeyHotey. Regardless, SEA started sending phishing emails at 1pm ET, posing as various members of the Daily Dot.
We should have known better than to fall for the group’s sleight-of-email tricks. The Daily Dot has extensively covered the SEA’s portfolio of attacks on news organizations, most notably NPR, the Guardian, and the AP—a hack that many agree caused a dip in the stock market. The SEA almost invariably strikes after seeing something that depicts al-Assad in a negative light.
“We are just Syrian youths who want to defend their country against the media campaign that is full of lies and fabricated news reports,” a representative told us in May.
As we learned from the Onion’s own admission, the SEA operates on a “weakest link” mentality. First, they start sending emails to members of a company, encouraging them to click a link. Those emails are often manipulated to appear as though they are coming from a colleague.
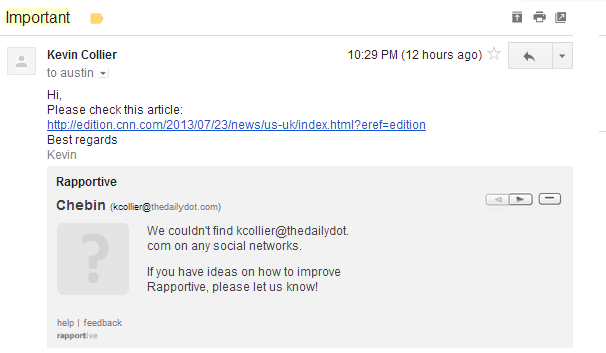
In this case, it looked like this:
But the link in that story actually redirects to a site that appears to be Google asking the user to verify his or her username and password. All it takes is a single person who has access to the content management system, and the SEA is in.
Earlier Monday, we sent out a company-wide email asking our contributors and staff members to be particularly careful about clicking on links. Clearly, some people missed the memo.
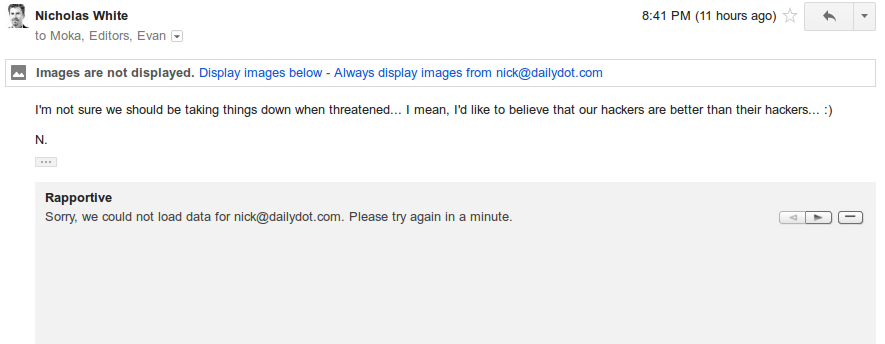
Worse, we tempted fate. The SEA found this one-liner tossed out by our editor-in-chief in regards to dealing with future threats from outside entities.
+1 SEA.
There are many basic lessons to be learned here. For starters, it’s critical to limit access to—or access within—any content management system to those who require it and understand the inherent risk that comes with it. The same goes for access to social media accounts. And users have to remain vigilant when using their email. It’s really that simple.
After all, the threat of another attack is always looming.
This time we deleted that article, the second time we will delete all your website https://t.co/mnuTVumSTD #SEA cc @dailydot
— SyrianElectronicArmy (@Official_SEA12) July 23, 2013
Illustration by Fernando Alfonso III