In a report released today, the Dallas-based cyber-intelligence firm iSight Partners alleges that since at least 2011, a group of mysterious hackers based in Iran have used fake digital personas to deceive and defraud (amongst others) several current and former senior members of the United States military, state and federal politicians, defense contractors, and members of the U.S.-Israel lobby of personal information. According to iSight, the news website NewsOnAir.org is one front on which this nearly four-year-long campaign has been waged.
The Iranians, iSight believes, aggregate news content from other digital publications, adjusting it slightly—changing the byline, adjusting copy here and there—and republish it. Once published under the new byline, the content would then be pushed out across social media. Someone give them six million dollars, they’re a journalism startup!
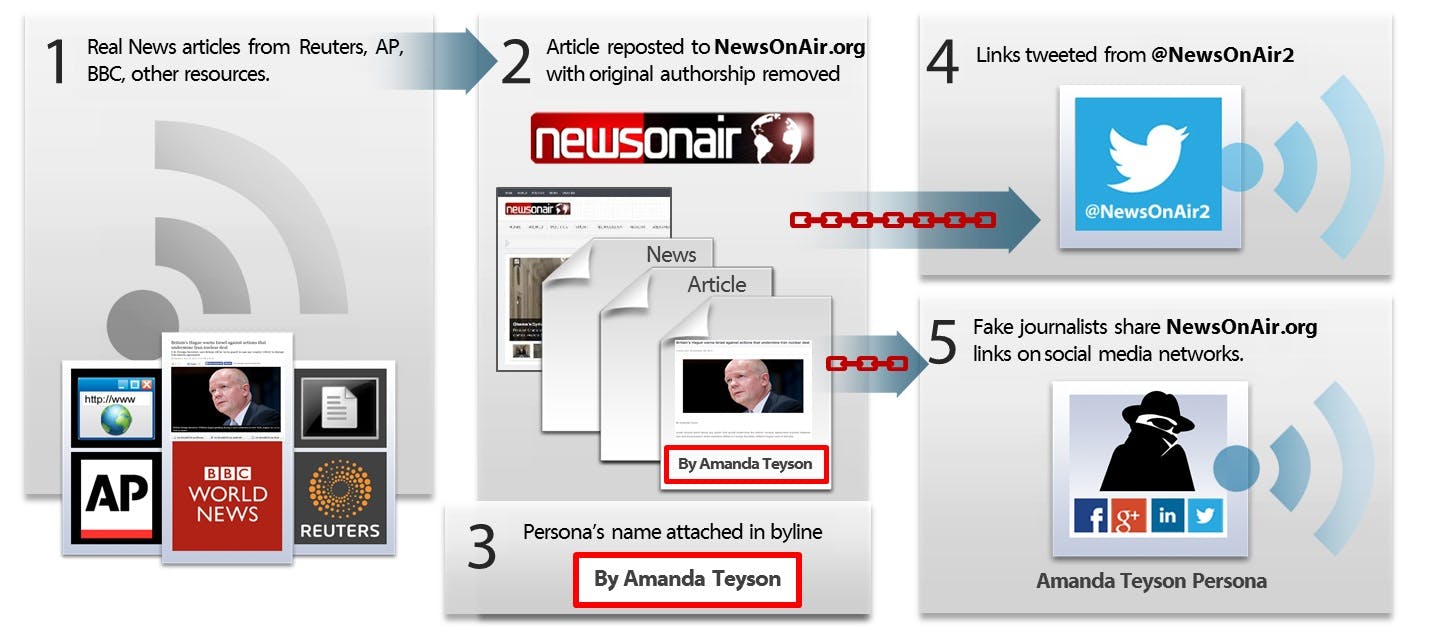
via iSight
Using fake Facebook pages, fake Twitter accounts, and fake LinkedIn profiles, the hackers interacted with each other online; according to the New York Times’ Bits blog, one hacker “also used social media platforms to publicize a personal blog about depression, aptly titled ‘My Loneliness.’” Having created a sense of personality and continuity, these hackers approached friends and family and other peripheral connections of high-value targets, asking them to engage with their content in the way that we all do—login with your Facebook, your Twitter, your Google account, whatever it may be.
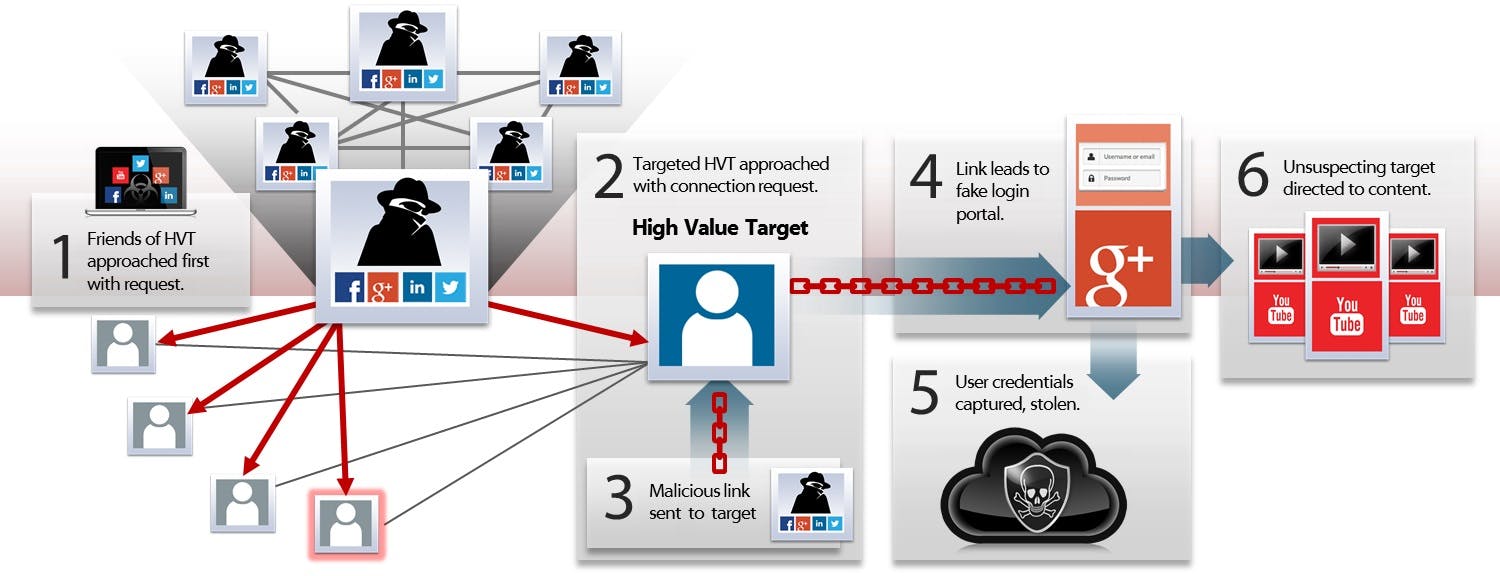
via iSight
High-value targets were then approached, the credibility of NewsOnAir.org and the personalities associated with it having been established. Some 2,000 people were caught in this web, according to the BBC. Of those, only about 200 people were actually being targeted.
Initially the links being shared and engaged with were free of malware; at first this was just your average content farm. “This campaign is not loud. It is low and slow,” Tiffany Jones, a spokeswoman for iSight, told the BBC. “They want to be stealth. They want to be under the radar.”
If iSight’s report is an accurate representation of how this “spear-phishing” scam works, it’s pretty fascinating that these hackers drew upon the implicit authority of journalism and journalists to instill their characters with authenticity. While only six of the 14 personas were (fake) journalists, all drew upon the stories published under the auspices of journalistic truth to establish trust with the secondary and primary targets.
Far be it from me to make a breach of the nation’s cybersecurity about myself, but in a roundabout way this illustrates something pretty interesting about the state of Web publishing. (Or, at least, what Iranian hackers perceive to be the state of Web publishing.)
Then again, it’s nothing you wouldn’t be able to intuit from a glance over your Facebook News Feed. For every link to reputable publications doing original reporting like the New York Times or the BBC there is another to a content farm simply in the business of repackaging news with varying degrees of value added. (*Looks around nervously.*) You probably don’t have to scroll too far down before you come across a death hoax or a piece of viral content of suspect provenance. I suppose there is just something horrible and hilarious to me about the idea that Elite Daily or Viral Nova could be a front for Iranian hackers. Heck, maybe this is, too. You don’t know, I could be a fake Internet persona suckering you into a grand scheme to steal your money and also the nuclear launch codes. Who can say for sure!
H/T Bits | Illustration by Jason Reed


