Since its debut last year, battle royale sensation Fortnite has attracted tens of millions of gamers—and a procession of scammers and fraudsters who are preying on unwary players and cheaters to make money.
The most recent scam, discovered by researchers at Malwarebytes, tricks users into installing a malicious file that steals data and information about bitcoin wallets. This is concerning since it’s a break from typical Fortnite cheat scams that involve “low-level surveys and downloads that never actually materialize,” notes Christopher Boyd, the researcher who published the findings.
The developers of the malware lure gamers into their trap through YouTube, where other scammers usually promote cheats, hacks, aimbots (tools to make aiming more accurate), and schemes to make free V-Bucks, Fortnite’s in-game currency.
Typical Fortnite scams include shortened links in YouTube video descriptions that direct users to a site where they can find more info or download the tool associated with the cheat. Those sites earn money by taking visitors through several steps where they must complete online surveys and view ads before giving them the download link. The practice has earned scammers quite a fortune, since some of their YouTube videos have amassed hundreds of thousands of views.
How the scam works
Most cheat sites run users in circles without actually delivering anything, which means it costs scammers nearly nothing to setup a profitable business.
The latest scam however delivers a malware disguised as a cheat tool. “Offering up a malicious file under the pretense of a cheat is as old school as it gets, but that’s never stopped cybercriminals before. In this scenario, would-be cheaters suffer a taste of their own medicine via a daisy chain of clickthroughs and (eventually) some malware as a parting gift,” Boyd says.
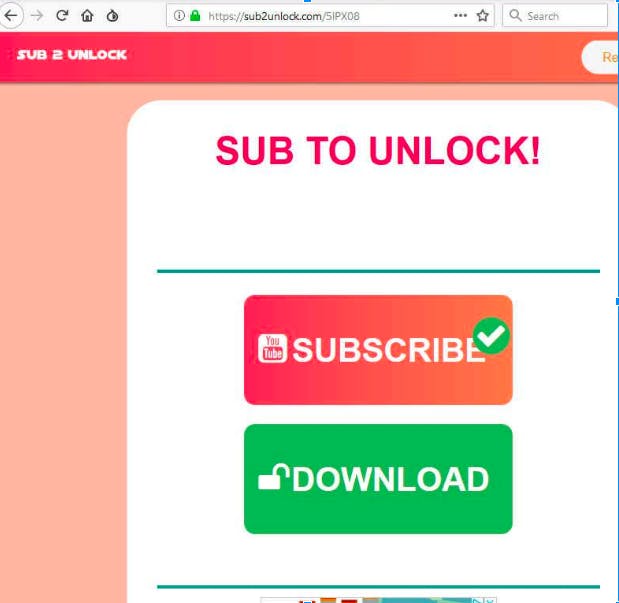
Like other scams, this one starts with a YouTube video and a link that points to Sub2Unlock, a link shortener service. But unlike other scams, the destination site doesn’t take the user through multiple steps or surveys before revealing the download button. It only contains a “subscribe” button that takes the visitor to the YouTube channel of the scammer. This is meant to make sure victims download and install the malware without getting frustrated.
“Here, we had no validation taking place during our testing. Clicking the subscribe button simply opened up the YouTube channel’s subscribe page but nothing checked to ensure we’d actually subscribed. All we had to do at this point was go back to the Sub2Unlock site and click the download button,” says Boyd.
Clicking download takes visitors to a site that Boyd describes as “a fairly good-looking portal claiming to offer up the desired cheat tools” which stands a fair chance of convincing youngsters of its legitimacy.
Victims are finally led to a general file-sharing service, where they can download the supposed cheat tool. At the time of the report, the file had been downloaded 1,207 times. “That’s 1,207 downloads too many,” Boyd says.
Once victims run the application, it fires up a remote access trojan (RAT), a type of malware that enables attackers to control the infected computer through an online server. The malware gathers information about the targeted computer and sends it to its command and control server in the Russian Federation. The most notable data in the bunch is browser session information, cookies, bitcoin wallet data, as well as Steam sessions.
That information can be used for a number of malicious purposes, such as hijacking online accounts and draining cryptocurrency wallets of their funds. There are several known ways that malware can steal bitcoins from computers, but in this case, no theft has been detected yet.
“In this example, we know the file is enumerating that the system may have wallets onboard but we’re still investigating the specifics of any potential coin theft activities,” Boyd says, adding that if the command and control center for the infection file is taken down, it may not receive the required commands to do anything in addition to standard wallet enumeration and tallying up what other programs and files are on the system.
“While this particular file probably isn’t that new, it’s still going to do a fair bit of damage to anyone that runs in. Combining it with the current fever for new Fortnite content is a recipe for stolen data and a lot of cleanup required afterward,” Boyd says.
This is not the first time that Fortnite cheaters have been inflicted with malware. In August, game-streaming service Rainway discovered a cheat tool installed on thousands of computers that directed web traffic through a web ads service, making the cheat’s creator money.
The moral of the story is that while shortcuts to Fortnite’s leaderboards might sound very tempting, you better avoid them altogether—you can’t know what kind of nasty surprises lay in your path. You’re safer going the long, legitimate way.
After all, what’s the point of winning when you know you’ve cheated your way to triumph?


