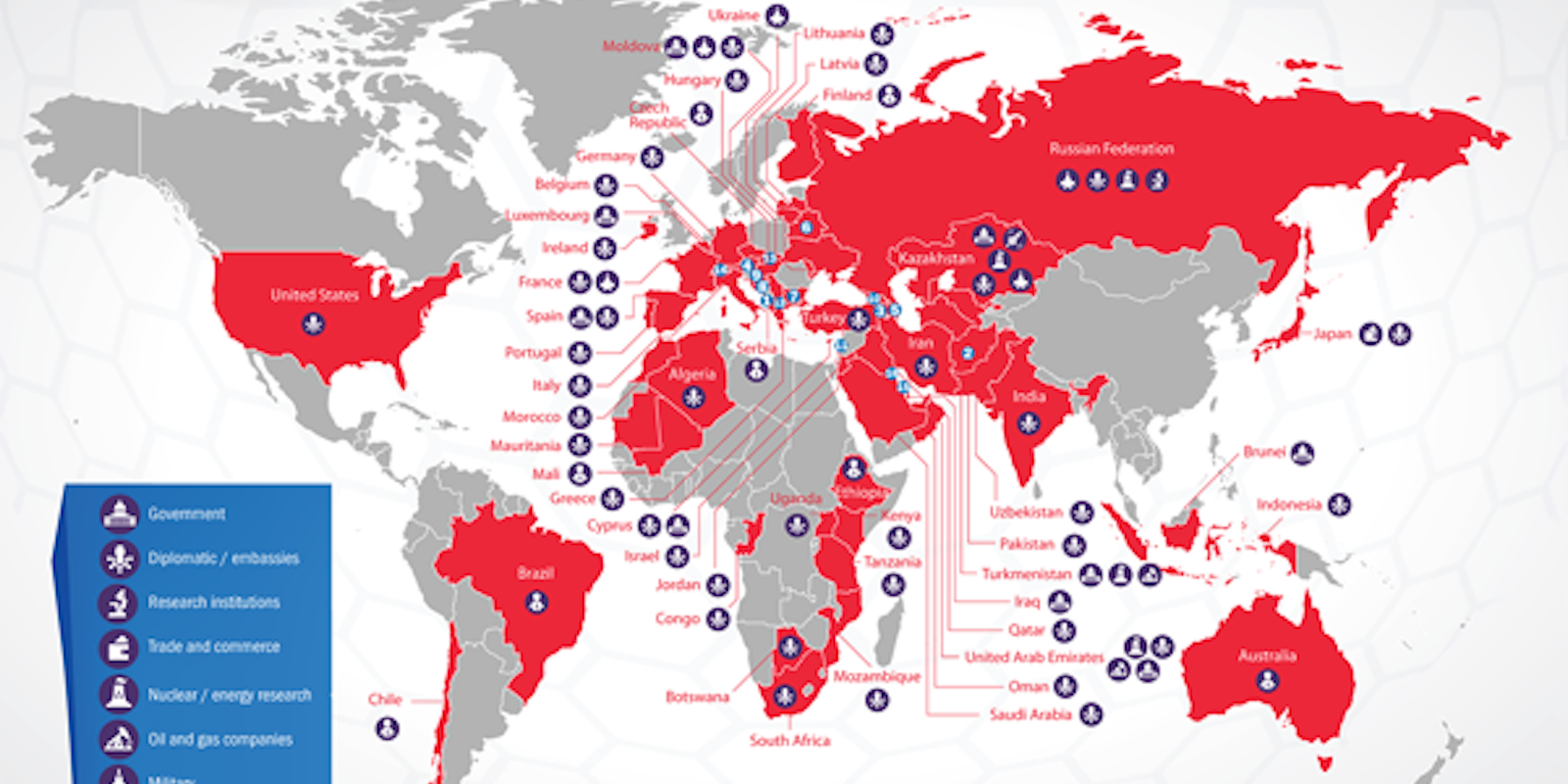
For five years, electronic ne’er-do-wells have been conducting an online spying operation that, while focused on targets in Central and Eastern Europe, has ranged across 69 countries and victimized hundreds of governments and research and diplomatic institutions.
Kaspersky Labs, the Muscovite antivirus and Internet security software firm that discovered the campaign, has branded it “Red October” and believes, given language clues they’ve uncovered, that it is likely conducted by Russian speakers.
The campaign, according to Kaspersky, “is currently still active with data being sent to multiple command-and-control servers, through a configuration which rivals in complexity the infrastructure of the Flame malware.”
The focus on the campaign has been on diplomatic and governmental targets, with information from each successful attack being used in future operations; credentials and passwords seized in one attack, for instance, were used in subsequent missions to gain access to further information.
To control the increasing network of infected machines, “the attackers created more than 60 domain names and several server hosting locations in different countries (mainly Germany and Russia),” creating “a chain of servers working as proxies and hiding the location of the true mothership command and control server.”
The campaign, says Kaspersky, did not target individual computers and servers alone. It also successfully breached smartphones, network equipment configuration, removable media, POP/IMAP servers and FTP servers.
Three different previously known exploits were used in the campaign, including vulnerabilities in Microsoft Word and Excel. Spear phishing was used at a high level, with most of the attacks tailored to specific systems or system users.
Although the malware modules were, Kaspersky believes, created by Russian speakers and the exploits by Chinese hackers, they do not believe there is necessarily a national actor behind it.
“Currently, there is no evidence linking this with a nation-state sponsored attack. The information stolen by the attackers is obviously of the highest level and includes geopolitical data which can be used by nation states. Such information could be traded in the underground and sold to the highest bidder, which can be, of course, anywhere.
Kaspersky first detected the campaign in October 2012, as part of a job for a customer. The first part of its extensive report is available online now, with the second part, detailing more of the technical side of the attacks, available later this week.
Graphic from Kaspersky Labs