Imagine all the worst things a hacker could do to your computer: Steal your files, access your webcam, record your login credentials for websites, and spread itself to computers belonging to your friends and family. Well, those are capabilities of the Blackshades remote access tool/Trojan (RAT), a malware authorities and computer security firms have called powerful, easy-to-use, and available to anyone for about $40.
The threat of attack from the Blackshades bug may have just taken a significant hit, however, as law enforcement agencies from 19 countries combined to arrest more than 90 alleged users of the inexpensive malware in a global sting operation over the past week.
Flanked by prosecutors and investigators from their respective cybercrime units, U.S. Attorney Preet Bharara and FBI Special Agent Leo Taddeo announced the arrests at a news conference in Manhattan on Monday. Bharara also said that law enforcement have apprehended three alleged Blackshades employees, including Alex Yücel, 24, the alleged owner of Blackshades and co-creator of the RAT software.
“The RAT is inexpensive and simple to use, but its capabilities are sophisticated and its invasiveness [is] breathtaking,” Bharara said.
Yücel, of Sweden, was arrested in Moldova in November, and prosecutors are in the process of trying to get him extradited to the U.S. Yücel faces more than 40 years in prison for charges including computer hacking, access device fraud, conspiring to commit access device fraud, and aggravated identity theft.
Computer security company Symantec described the Blackshades RAT as “popular and powerful,” in a blog post published Monday. Though, when asked to provide further context, a security expert from Symantec said that the Blackshades malware is far from singular.
“No, the software here was not exceptional,” Vikram Thakur, Sr., Symantec’s principal software engineer for security technology and response, told the Daily Dot in an email. “Its competitive pricing and simple point-and-click interface allowed a wide spectrum of threat actors—from entry-level hackers to sophisticated cybercriminal groups—to leverage it to steal data, browse file systems, take screenshots, record video, and interact with instant messaging apps and social networks.”
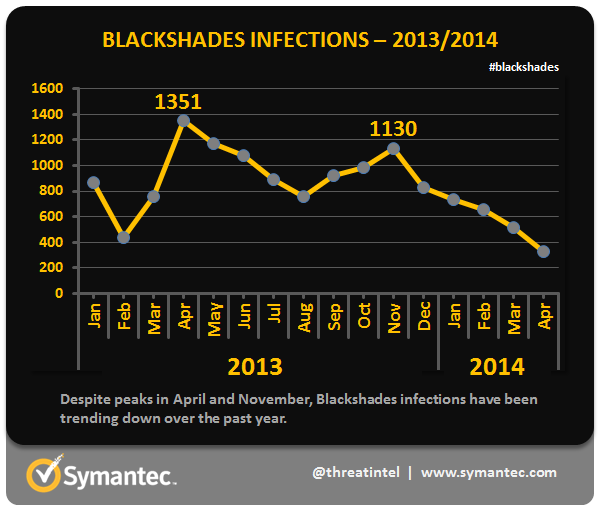
The malware is believed to have infected half a million computers in more than 100 countries. Symantec found that the U.S. was by far the country most-affected by Blackshades, with 37 percent of the total infections in 2013 and 2014, and that use of the product began to drop off around the time of Yücel’s arrest.
While Bharara’s Southern District of New York office has been responsible for a number of high-profile cybercrime prosecutions—ranging from that of hacker-turned-informant Sabu to the alleged operators and users of the online drug website Silk Road—he called the Blackshades investigation “amazing” because of what he described as unprecedented cooperation between nations. The federal prosecutor said the effort signifies a new unified global effort against cybercrime.
“A number of years ago, I don’t think we would have been able to get as many countries on the same page on the same day at the same time, in unison working shoulder to shoulder, to get as many bad guys,” he said. “You can’t just hide in another country anymore; the nations of the world appreciate that [cybercrime] is a global threat, not just a threat that affects particular countries like the United States.”
Symantec’s Thakur, Sr., also described the cooperative law enforcement effort as “unprecedented” and said he believes its success will encourage even more nations to participate in future investigations.
Investigators made a breakthrough in the case against Blackshades as far back as June 2012, when they arrested a man named Michael Hogue in Tucson, Ariz., as a part of a separate anti-cybercrime operation. Hogue, 23, who went by the codename “xVisceral,” pleaded guilty to helping create the RAT and agreed to cooperate with the investigation against Blackshades, according to court documents released Monday.
A third alleged Blackshades employee, Brendan Johnston, 23, was arrested in California on Sunday. Johnston allegedly helped market and sell the malware, and provided technical support to customers.
The sites through which Blackshades previously sold its software were unavailable Monday. Check out this page on the FBI’s website for signs that your computer may be affected and methods to test your system for infection.
Photo by Davide Restivo/Flickr (CC BY-SA 2.0)


