Free public Wi-Fi is everywhere: in hotels, malls, libraries, coffee shops. To most people, they’re an excellent way to save on your mobile data plan while reading news, managing your social media accounts and reading your emails.
But free Wi-Fi networks are also a major source of security vulnerabilities, and there are many ways malicious actors can exploit them to steal critical information from negligent users or harm them in some other way.
However, this doesn’t mean that you should avoid public Wi-Fi altogether. Here are a few tips to help keep you avoid the security pitfalls of public Wi-Fi while take full advantage of free internet.
Avoid using insecure and unencrypted apps
Because anyone and everyone can roam on public Wi-Fi networks, two of the greatest security threats they trail along are packet sniffing and man-in-the-middle (MitM) attacks. Packet sniffing involves a malicious user eavesdropping on your communications through a network-monitoring tool such as WireShark. MitM, on the other hand, is a kind of hack in which a third party intercepts communications between two endpoints to either steal data or to inject malicious content such as malware.
Your biggest defense against packet sniffing and MitM attacks is the use of encrypted communications. On your browser, it means visiting websites that have the green padlock icon and start with “HTTPS.”
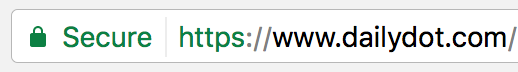
If you’re visiting websites that do not use the HTTPS protocol, you should take note that anyone with minimal IT skills will be able to eavesdrop on your network traffic. This might not be such a big deal if you want to browse through the news, but if you’re carrying out more sensitive activities, you might want to keep an eye out for that padlock.
In general, browsers are more resilient to MitM attacks than apps, and many apps are prone to accepting fake and spoofed security certificates when connecting to their servers. So, you’re better off using secure websites instead of specialize apps when using public Wi-Fi networks, except for apps developed by companies that are renowned for their security.
Avoid fake access points
Anyone with a cheap wireless router or even a mobile device can setup a Wi-Fi network. Hackers sometimes use this tactic to ensnare careless users and trick them into thinking they’re connecting to legitimate access points. In order to further conceal their ruse, attackers will often use the names of known networks, such as those belonging to your local Starbucks or McDonalds. This type of attack is called the “evil twin.”
Once you connect to an evil twin access point, your entire internet traffic will be channeled through the malicious router, putting your communications at the mercy of the attacker.
In order to avoid evil twin attacks, don’t connect to Wi-Fi networks you don’t recognize or networks with duplicate names (i.e. if you see two networks named “McDonald’s Wi-Fi”) . Always check with the owner of the network when in doubt. Don’t forget to use encrypted apps in order to prepare for the worse-case scenario. And to avoid unwittingly stepping into an Evil Twin trap, switch off automatic Wi-Fi connection both on your computer and your phone.
Log off from your accounts
Another type of attack that is similarly destructive is session hijacking. Session hijackers steal cookies—tokens of information sent between a server and a client to identify an ongoing session—in order to impersonate the user and access online accounts such as Facebook, Twitter, or Gmail.
What makes session hijacking particularly devious is the fact that attackers won’t need your password to get into your account, and once they get a hold of your session cookie they’ll be able to use it even after you disconnect from the network, until the session expires. This type of attack is especially effective on websites that use HTTPS on their login page but not on other pages.
I would advise against using any website that uses unsecure connections. But if you absolutely have to, an added measure of security would be to log off from any website you’ve signed into during before leaving a public Wi-Fi. This will expire session cookies and prevent them from being used by malicious actors. Some websites such as Facebook and Gmail let you view the details of all remote open sessions and end them manually.
Install a VPN
One of the best measures to play it safe and protect yourself against potential vulnerabilities in apps and websites is to sign up with a virtual private network (VPN), a service that reroutes all your network traffic through a secure and encrypted server.
VPN software are available for both mobile and desktop operating systems, however not all of them are as safe as they seem. There are a lot of free VPN services, some of which rely on selling user data to third parties as a source of revenue. While these VPN providers will protect you from Wi-Fi hacks, they might expose you to other security threats.
Paid VPN services are more reliable in general, so it doesn’t hurt to spare a few bucks a month to avoid security headaches in the future, especially if you frequently work on the move. According to a research by the Commonwealth Scientific and Industrial Research Organisation (CSIRO), an Australian government agency, F-Secure Freedome is a decent VPN service that offers robust encryption and ad blocking at $6 per month.
Prevent external access to your computer
While most of the tips we’ve share so far have to do with avoiding walking into traps while surfing the web, you should also harden your device against attackers who might want to directly connect to your device.
Windows and MacOS’s built-in firewalls are pretty effective in preventing intruders from gaining access to your device.
Also, disabling file-sharing will prevent other users from remotely accessing files on your hard drive. On a Windows computer, you can turn off file sharing by heading to the “Network and Sharing Center” in Control Panel, and selecting the “Turn off file and printer sharing” option for the public network profile. In MacOS, go to the Sharing entry in System Preferences and clear the File Sharing checkbox.
Furthermore, consider turning off network discovery to make it harder to find your device by roaming the network. Windows network discovery can be adjusted in same place where file sharing settings are found. In MacOS, you have to turn on Stealth Mode in the Firewall Options section to avoid network discovery.
Ben Dickson is a software engineer and the founder of TechTalks. Follow his tweets at @bendee983 and his updates on Facebook.


