It’s been two years since Edward Snowden leaked NSA documents to journalists, revealing a vast high-tech surveillance operation targeting millions of Americans and foreigners around the world.
Since the first Snowden articles were published in June 2013, the global public has increasingly adopted privacy tools that use technology like strong encryption to protect themselves from eavesdroppers as they surf the Web and use their phones.
Of course, there are concerns other than the National Security Agency to contend with as well, most notably hackers and privacy-invading corporations, both of which make privacy tools that much more appealing.
Tor
One of the most powerful privacy tools ever built is Tor, an anonymity network that allows anyone to use the Internet without easily revealing their location or identity.
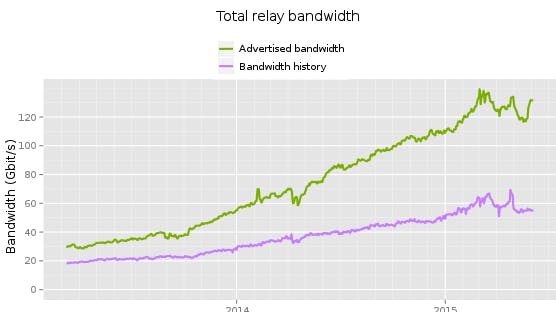
The Tor network has more than doubled in size since Snowden’s revelations, to over 2,000,000 concurrent users, as of June 2015. The relays that handle the network’s traffic have doubled in number as well, to almost 7,000, while the network’s total bandwidth has more than quadrupled to 130 Gbit/s available for use.
Tails
The growth in popularity of privacy tools extends beyond Tor.
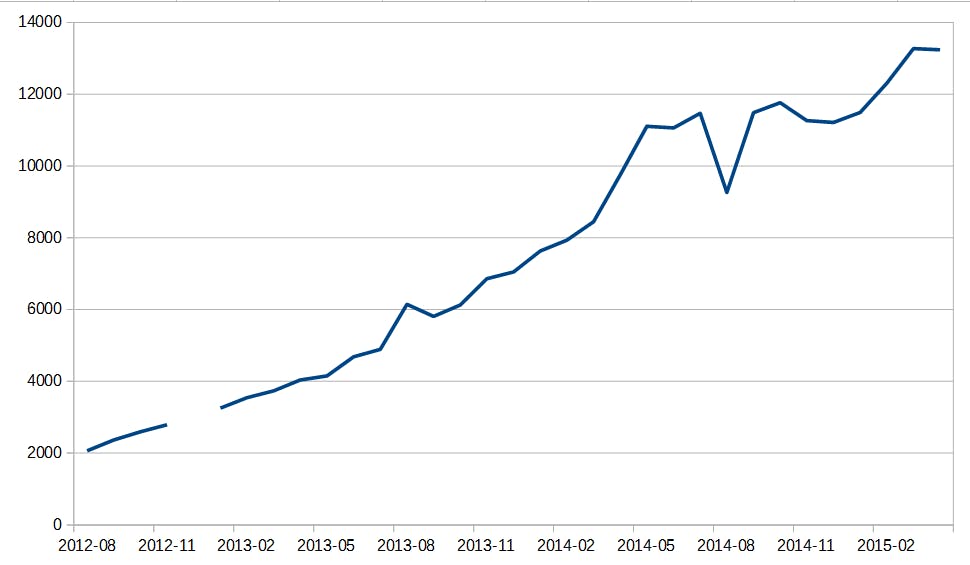
Tails, the operating system designed as an anonymity-focused competitor to Windows and Mac, is booted up 13,239 times per day, according to the developers.
That’s a three-fold increase from pre-Snowden days, attributable in big part to the credit journalists Glenn Greenwald and Laura Poitras have given to Tails by securing their work with the OS (and talking about it publicly) over the past several years.
Tails—The Amnesiac Incognito Live System—can be loaded on to almost any computer via DVD or USB stick. Tiny and powerful, it forces users to be secure and anonymous by default. Utilizing Tor, PGP data encryption, and OTR (Off The Record) chat encryption, users operate in a far more secure environment than commercial operating systems offer.
Journalists in particular have taken to Tails.
“Tails have been vital to my ability to work securely on the NSA story,” Greenwald said last year. “The more I’ve come to learn about communications security, the more central Tails has become to my approach.”
PGP
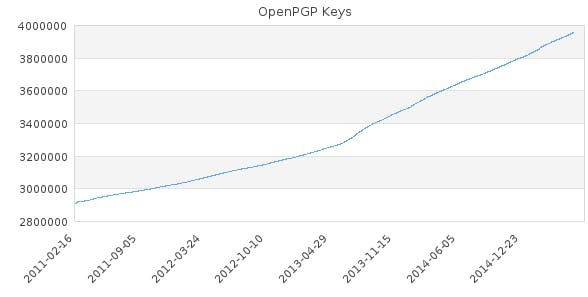
PGP (Pretty Good Privacy), the data-encryption software used most commonly to secure private emails, has experienced double the daily adoption rate, to over 1,100 new keys added, according data collected by Kristian Fiskerstrand on over 80 key-storage servers around the world.
The growth rates haven’t been without turbulence. In the months following Snowden’s revelations, for instance, daily PGP adoption reached even higher levels than they’re at today.
SecureDrop
SecureDrop is a whistleblower-submission system that allows anyone to anonymously pass data on to journalists through the Tor network without compromising a source’s identity. At the time of Snowden’s revelations, only a single media outlet used the software: the New Yorker.
Today, the number is much higher. Forbes, the Intercept, the Guardian, the Washington Post, Gawker, and the Globe and Mail are among the most prominent publications to use SecureDrop as protection against government eavesdropping. The complete list of SecureDrops lists 17 currently active organizations.
OTR messaging
Off The Record messaging (OTR) is an encrypted instant-messaging protocol that allows users to have private conversations instantly while reliably authenticating the user on the other end.
Snowden “unquestionably spurred interest in the privacy technology
community to get usable tools out there,” Ian Goldberg, OTR’s lead developer, tells the Daily Dot. Within just a couple of months of Snowden’s disclosures, the number of OTR users had doubled. (Goldberg didn’t have immediate access to more recent records.)
The big picture
Tor, Tails, SecureDrop, OTR, and PGP are all open-source software. This means that the code that powers each tool can be examined by anyone to test for flaws and backdoors that make the systems vulnerable. Open source doesn’t mean perfect—like any software, there’s no such thing as 100-percent security—but transparency is considered a key necessity for many users seeking security so that nothing malicious can be snuck in through a backdoor.
The increasing adoption of privacy tools coupled with popular disapproval of massive American surveillance has driven some of the world’s biggest companies to make privacy a top priority.
Apple CEO Tim Cook has made encryption a selling point for Apple products while carrying out a political war of words with Washington, D.C., institutions and officials, like FBI director James Comey, who aims to ban strong encryption and offer fundamentally weaker protection to Americans in an effort to aid law enforcement.
Both Apple and Google are increasingly offering strong encryption as default options on their smartphones, while personal computers have experienced an explosion of privacy tools as well, a few of which we outlined above.
Additionally, massively popular apps like WhatsApp are rolling out their own strong encryption with the incorporation of secure-messaging system TextSecure.
“The right approach, in my opinion, is to give private communications tools to people without their asking for it,” Goldberg says. “People shouldn’t have to choose between ‘communicate’ and ‘communicate securely/privately.’ There should not be a way to communicate insecurely.”
Goldberg praised the inclusion and strengthening of encryption in popular services like WhatsApp and in Web browsing, calling the moves “a great beginning in that direction.”
While power tools like Tor and Tails may offer the most secure experience for their users, it’s the default encryption on popular devices like iPhones and Android devices that will touch the most people and deliver strong privacy through strong encryption to hundreds of millions of mobile phone users in every country on Earth.
Illustration by Max Fleishman