On a nondescript and casual morning, you open your email to find a message from your bank telling you that your account has been compromised and you need to change your password at a link provided in the body of the email. Knowing the email might be a phishing scam, you check the sender’s address to make sure it actually comes from your bank. It does.
Except that it doesn’t.
As it happens, phishing scammers can easily falsify the sender’s address. The process, called “email spoofing,” enables attackers to make their emails look like they come from a trustable source and lure the recipient into downloading a malware-infected attachment or click on a link that steals sensitive information.
If well-designed, spoofed emails are hard but not impossible to spot. With a little effort and the right practices, you can considerably raise your chances against phishing scams that involve spoofed emails.
What is email spoofing?
All it takes to send a fake email is access to an email sender software, such as PHPMailer, and a server that can send emails, also called an SMTP server. Most web hosts offer SMTP services. You can also install it on your own computer. Traditional mailing software usually fills the “from” field with the email address you used to log in. Software such as PHPMailer enables you to select a custom sender address.
When you send the email, the recipient will receive a message that seems to have come from the address you typed—but if they look under the hood, there are details that indicate the email has been spoofed.
READ MORE:
- The best free antivirus tools for Windows and Mac
- The best free password managers
- How to encrypt an iPhone in seconds
There’s one caveat: If the recipient replies to the email, the response will be sent to the account whose address has been spoofed. That’s why spoofed emails usually contain a “don’t reply” notice and instead ask you to visit a website or download an attachment.
If you log in to your email account and find a lot of undelivered notifications or replies to emails you didn’t send, there’s a great chance that someone is using your address to send spoofed emails.
How can you identify spoofed emails?
In order to prevent email spoofing, the Sender Policy Framework (SPF) was created in the early 2000s. SPF instructs every domain to specify a list of authorized IP addresses that can send emails from that domain. Those addresses are stored in the Domain Name System (DNS) server where the domain is registered.
Every email envelope contains the IP address of the sending host, which the recipient can check against the domain’s SPF records to make sure it comes from a trustable source. But it’s totally up to the recipient to decide what to do with a non-conformant email.
SPF records are not a perfect method because they require an administrator to specify every IP that can send emails from that domain. That’s why many email servers do not block incoming emails that fail the SPF test to avoid rejecting legitimate emails but do flag them as potentially malicious emails.
More recently, a new record type called DMARC (Domain-based Message Authentication, Reporting, and Conformance) was created to complement SPF. DMARC enables domain owners to instruct receiving servers on how to deal with potentially phony emails, such as outright rejecting, quarantining, or flagging them.
READ MORE:
- What you really need to know about malware
- How a VPN works—and why experts think you should use one
- How to protect yourself against ransomware
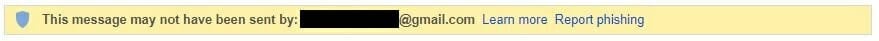
Email servers such as Gmail use SPF and DMARC to identify spoofed emails. In case you see the following alert when you receive an email, there’s a likely chance that the email is not from the original sender.
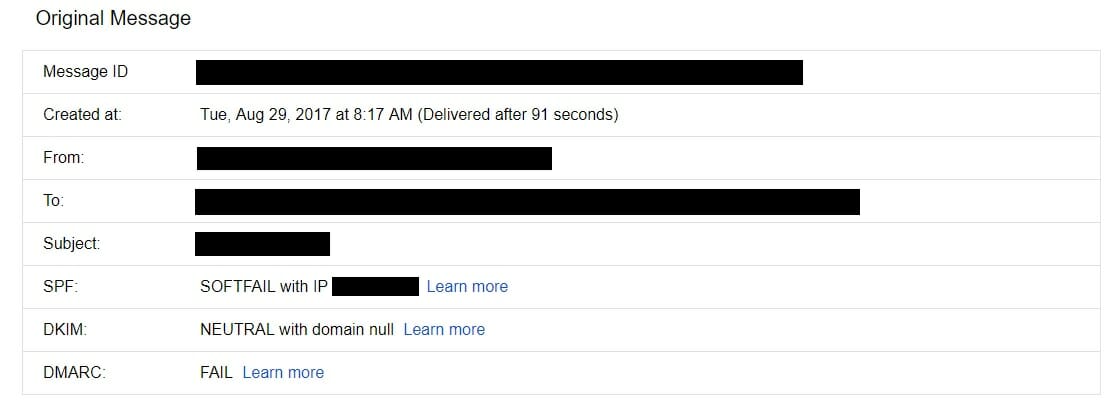
If you want to dig deeper into the details, click on “Show original” in the message options to view the email headers. This will show you the envelope details.
Here, you can see the IP address of the server that sent the email, which you can use to further investigate the sender. You can use this method to investigate any email.
How can you protect yourself against suspicious emails?
Checking the email headers is one way to verify the source of the email. Aside from that, here are several methods to avoid stepping into a trap:
- If the email appears to be from someone you know, send them a separate email or contact them through an alternate method (phone, messenger app, secondary email) and confirm that they’ve sent the original email.
- If the message instructs you to log into a website, don’t click on the link embedded in the email. Browse to the website by typing its original address and check to see if a similar notification has appeared in your account.
- Keep your anti-malware and web protection software active and up to date. Most antivirus solutions have tools to detect online scams.
At the end of the day, the best way to protect yourself against potential scams is a healthy dose of skepticism. Whether you see the spoofed email alert or not, if you run into an email that is urging you to take potentially damaging action, don’t click on links or attachments until you verify the identity of the sender.
Ben Dickson is a software engineer and the founder of TechTalks. Follow his tweets at @bendee983 and his updates on Facebook.