Police records obtained by the Daily Dot reveal in unprecedented detail how the Obama administration enables law enforcement to suppress information about controversial phone-surveillance technology used by police throughout the United States.
The documents, which link the purchase of so-called Stingray devices to various North Carolina state and local police agencies, include a fill-in-the-blank warrant drafted by the U.S. Justice Department (DOJ) and intended for use by state and local police that extends the veil of secrecy over law enforcement’s Stingray use.
The records, originally acquired by Working Narratives under North Carolina public records law and shared with Daily Dot reporters, also offer new specifics about the capabilities of Stingrays bought by police in North Carolina from Harris Corporation, a leading U.S. manufacturer of cell-site simulators, and the company behind the original “StingRay” procured by the Pentagon and various intelligence agencies more than two decades ago. The North Carolina agencies referenced by the documents include the New Hanover County Sheriff’s Office; the Wilmington Police Department; and the North Carolina State Bureau of Investigation, an agency that reports directly to Gov. Patrick L McCrory (R).
A batch of internal emails also obtained by the Daily Dot show police debating tactics to keep certain officers away from the witness stand, as well as discussing with a U.S. Secret Service employee the federal government’s efforts to prevent disclosures about these closely guarded surveillance tools, which are used to pinpoint the location of a targeted individual through the interception of cellphone signals.
U.S. attorneys have portrayed the Stingray—the colloquial term for a “cell-site simulator”— as an invaluable law enforcement tool, one that aids in complex narcotics investigations, kidnapping cases, and fugitive apprehension efforts. The government has argued against the disclosure of any information related to Stingrays, stating that it would pose “significant risks to effective law enforcement, and ultimately the safety of the public and the national security of the United States.” The government also requires non-disclosure agreements for police departments that obtain them.
Legal experts, however, say that Department of Justice has purposefully crafted a template for police Stingray warrants that obscures critical details about the device’s operational capabilities from the judges who authorize their use. Multiple civil- and digital-rights organizations claim the language applied in the warrants effectively downplays the most intrusive feature of simulated cell-site technology: jamming the cellphone signals of dozens, if not hundreds, of innocent bystanders while collecting information about them.
How Stingrays work
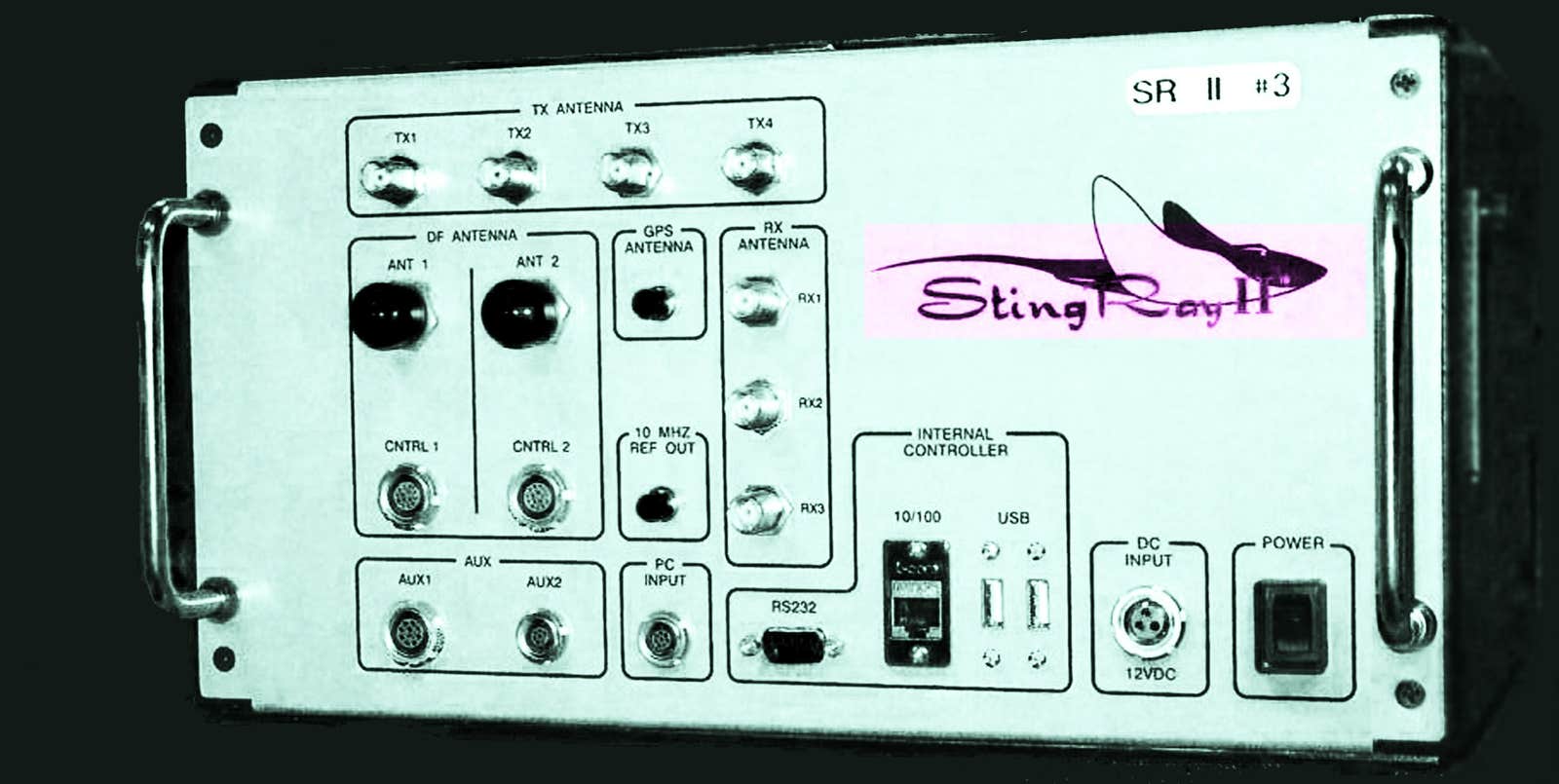
Stingrays, sometimes called “IMSI catchers,” work by emulating the base transceiver stations—commonly referred to as “cell towers”—that serve as a midpoint, essentially, between cellphones and the cellular networks operated by telecom giants such as AT&T, Verizon, and T-Mobile. The purpose of a Stingray, which is roughly the size of a suitcase, is to hack this connection.
A cellphone is itself a tracking device. An AT&T subscriber will not receive calls or messages unless AT&T can locate their phone. In the high-speed LTE network, the relative location of a cellphone is tracked at all times to ensure calls are placed as quickly as possible. This is accomplished, in part, because the network is always checking to see which cell towers subscribers are closest to. If a subscriber is no longer in reach of the last tower they connected to, the search expands outward, starting with nearby towers within the same tracking area. Police exploit this technical process by positioning Stingrays to serve as the cell tower closest to their target.
“Whether or not they’re using it, there’s no way to tell. It is scout’s honor.”
The moment the Stingray is deployed it begins to masquerade as a cell tower, transmitting a radio signal slightly more powerful than the legitimate towers in the area. The effect is such that cellphones within reach of the police signal drop their connections to the legitimate cell towers and connect instead to the police device, which can be carted around in a van or the trunk of a car.
Cellphones, once connected to a Stingray, lose their ability to send or receive calls, texts, and any other form of communication. This communications blackout could potentially affect dozens or hundreds of subscribers at once—not only an intended target.
When the target’s phone is located among those affected by the device, police can use a direction-finding (DF) antenna to track the phone’s transmission to its source—down to a specific room in a house. A common DF antenna attachment for the Stingrays is called “AmberJack.” The range of Harris Corporation’s Stingray, according to manuals previously leaked by the Intercept, is approximately 200 meters. However, various range-extending attachments are available as well.
“There are two versions of the software for Harris cell-site simulators: a federal version and a state/local version,” says Mike Katz-Lacabe, a California-based researcher and privacy activist. “Based on my research, I believe that the state and local versions cannot intercept phone calls and text messages, but the federal version can. The hardware is the same for both versions of the software.
“Given the secrecy surrounding these devices, little is known about when they are used, how frequently, how much data they collect, or how long that data is stored,” adds Katz-Lacabe of the Center for Human Rights and Privacy, whose website lists 25 non-disclosure agreements between police departments and the FBI.
With LTE now in use by more than a billion devices worldwide, the process for intercepting cellphone signals is not as easy as hoisting an antenna in the air. Older GSM networks only require phones to authenticate with cell towers, but with LTE, authentication goes both ways: Cell towers—or in this case, Stingrays—must likewise authenticate back to the phone.
This “handshake” between phone and tower is a complex, multi-step protocol that modern Stingrays must now emulate. Some North Carolina authorities have purchased an upgraded version of the Stingray called “HailStorm,” the sole purpose of which is to circumvent the enhanced security protocols built into LTE networks.
Given the complexities involved in exploiting the LTE network, referring to a Stingray as simply a “surveillance tool” is reductive. They are, in fact, sophisticated hacking machines.
Deceiving judges
Public interest in Stingrays rose sharply in 2012 following an Arizona court battle (U.S. v. Rigmaiden) concerning their use. FBI agents had deployed one of the devices during a mail and wire fraud investigation, which led to a suspect’s capture. In doing so, it collected information on a number of “innocent, non-targeted devices.” (FBI said it purged all information unrelated to its case, as required by a court order.) That same year, it’s worth noting, a government prosecutor in New Orleans claimed in court that cellphone owners have “no reasonable expectation of privacy” with regards to cell-site data collected by providers. That argument failed to sway the presiding magistrate. In 2013, however, the U.S. Court of Appeals for the Fifth Circuit, in a 2-1 decision, reversed the ruling, stating that law enforcement did not require a search warrant to access historical data obtained directly from a phone company.
In September 2015, the Justice Department reversed course, announcing a new policy that requires all federal law enforcement agencies to obtain a probable cause warrant before deploying a Stingray. The Justice Department would not concede, however, that warrants should be required in all cases, meaning it has preserved the ability to argue in court that warrants are not necessary. Nevertheless, the announcement was met with applause from influential digital rights groups, such as the Electronic Frontier Foundation (EFF).
The policy—which is not to be confused with law—further requires all state and local law enforcement to obtain warrants before using a Stingray in conjunction with a federal investigation. According to internal police records acquired by the Daily Dot, the Justice Department has provided agencies below the federal level with a template for how these warrants should be drafted.
“There are good reasons for police and prosecutors to want to save time when they’re in an investigation and having to re-write an application from scratch probably doesn’t make sense,” says Nathan Wessler, a staff attorney at the American Civil Liberties Union. “What becomes troubling is when some of the boilerplate they intend to just be copied and pasted fails to give a robust enough description of what police want to do.”
According to Wessler and other legal experts who reviewed the warrant, the DOJ’s template is deliberately vague when police tell a judge exactly what the device they want to use is capable of. The warrant minimizes the device’s expansive surveillance capabilities, effectively lies about the technical consequences to bystanders, and deliberately keeps judges in the dark and shielded from oversight responsibilities.
In a statement to the Daily Dot, the DOJ says that the use of Stingray devices are designed to be compliant with the law.
“The current language of Department warrants related to cell-site simulators makes clear that in order to follow department policy and federal law, the devices are designed to comply with the warrant requirement of the Fourth Amendment and Rule 41 of the Federal Rules of Criminal Procedure, as well as the Pen Register Statute,” DOJ spokesperson Dena W. Iverson said.
The DOJ warrant describes the Stingray as a “trap-and-trace device/cell-site simulator”—making the two descriptions seem interchangeable—that will “determine the location” of their target. But the cell-site simulators can do a whole lot more. It doesn’t just take metadata on call numbers and duration; simulators can do anything up to and including recording phone calls.
“It has the capability, depending on software settings, to intercept text messages and [phone call] content,” says Stephanie Lacambra, a staff attorney at EFF. “They keep trying to say, ‘Oh we’ll make sure that isn’t going to happen.’”
With little oversight, law enforcement is armed with a tool that can capture and record texts and phone calls. They are trusted to use the tool at its minimum capabilities, but there is no publicly known enforcement mechanism or logging to ensure police are following the law and not engaging in illegal surveillance, according to legal experts. “Whether or not they’re using it, there’s no way to tell,” Lacambra says. “It is scout’s honor. We’re just supposed to take them at their word.” The relationship between the courts and police in these cases seems built on trust rather than verification.
“That’s what I find so troubling,” Lacambra says. “The courts are so ready to defer and say, ‘Well, of course we would not expect the police to lie to us whether it’s intentional or unintentional.’”
Law enforcement is instructed to ask the court to keep the warrant to use the Stingray secret, according to these documents, even though the Justice Department claims publicly that it encourages disclosure, Lacambra says. On the blank warrant, the DOJ instructs police to tell judges that Stingray disruption is just like “ordinary” cell service. Elsewhere, however, the DOJ admits that Stingrays can disrupt cellphone calls and interfere with the cellular network for anyone within up to 650 feet of the target. In a major American city, that distance potentially encompasses hundreds of homes and thousands of individuals.
We know from sworn testimony from Toronto police that Stingrays can disrupt all cell activity up to and including 911 calls. Even though the devices are programmed to disengage when citizens in the area attempt to reach emergency services, they often fail to do so, according to an internal Royal Mounted Canadian Police (RCMP) memo, published this April by the Globe and Mail.
Due to frequent malfunction with Stingrays, Canadian authorities admit the contraption is run at a “calculated risk to public safety,” Globe and Mail reports. According to RCMP, police are now only allowed to use the device for three minutes at a time. And while the U.S. Justice Department’s warrant is meant to reassure judges that any service disruption will be “brief” and “minimized,” at least one documented case shows the continuous use of a Stingray in Oakland, California, for over nine hours.
The lack of oversight and the potential widespread consequences for innocent Americans exacerbate concerns over the DOJ telling police to go for warrants with no time limits. With this warrant, officers arguably have carte blanche to turn the device on whenever they feel like and keep it going for hours at a time.
The Justice Department’s warrant contains no explanation about how Stingrays send signals not only into public spaces but also through the walls of homes and into private spaces. Nor does it address how Stingrays may affect bystanders’ phones or privacy. “That’s all really important and relevant information for a judge to structure a warrant to try to minimize impact on people’s privacy,” Wessler says.
“None of these nuances are being conveyed to the judicial officer,” adds Lacambra. “That’s disingenuous when they’re saying this is the template and they’re representing to the court that ‘this is what we’re going to strive to [do],’ but when in practice that’s absolutely not what’s happening. And there’s no way to have any public judicial oversight over that because they’re not disclosing to us the methods they use.”
“I guess this is one way to avoid FOIA and the ACLU.”
Internal records acquired by the Electronic Privacy Information Center (EPIC) in 2012 revealed concerns at DOJ over the use of cellphone-tracking equipment and how it might conflict with federal laws governing the use of radio transmissions, namely, the Communications Act.
By design, Stingrays transmit signals over commercial radio frequency bands licensed exclusively to cellphone companies; because law enforcement agencies operating Stingrays do not have a license to transmit over these bands, legal experts have argued their use is prohibited under federal law. Last month, the Center for Media Justice, Color Of Change, and New America’s Open Technology Institute began pushing the Federal Communications Commission (FCC), which regulates wireless communications in all 50 states, to investigate police use of Stingray technology.
Stingrays also appear to meet the criteria for being considered a “jamming device” under FCC guidelines. In a 2014 advisory notice underscoring FCC’s prohibition on police using jammers, P. Michele Ellison, chief of the agency’s Enforcement Bureau, explained that a jammer generally does not discriminate between desirable and undesirable communications,” meaning innocent people are as affected by their use as police targets. Further, Ellison explains that “cell jammers” are devices that prevent “your cellphone from making or receiving calls, text messages, and emails.”
In a statement on Aug. 17, the EFF called on the FCC to begin proceedings to address “not only the harmful interference but also the duty of every police department to use Stingrays in a constitutional way, and to publicly disclose—not hide—the facts around acquisition and use of this powerful wireless surveillance technology.”
Funded by drugs
Many of the new Stingray documents from North Carolina are notable for their lack of redactions, according to Katz-Lacabe, given the level of secrecy typically surrounding their use.
The records, for instance, show that the Wilmington Police Department, whose port-city jurisdiction resides within New Hanover County, spent $33,900 on Stingray maintenance in February 2015, roughly a year after upgrading a StingRay II device and purchasing a range extender for a total of $93,625.
Wilmington P.D. did not respond to a request for comment.
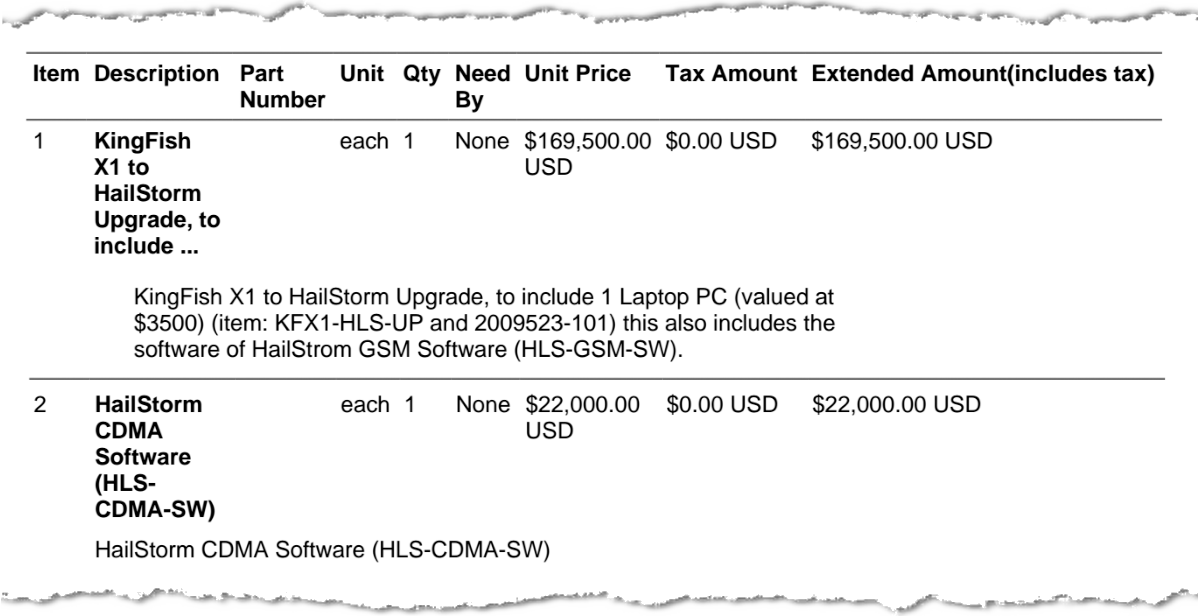
Records from the North Carolina State Bureau of Investigation (SBI) show that in June 2013, $169,500 was expensed by the agency to purchase Harris Corp. hardware, including a “KingFish X1 to HailStorm Upgrade,” in addition to a software package ($22,000), three “Harpoon” signal boosters (up to $22,200), and a wide band “Amber Jack” radio directional finder ($38,400). Internal emails also show that SBI was operating a “Sting Ray” as far back as February 2010, when the SBI assistant director authorized a $60,000 expense to upgrade the device to track Nextel phones.
SBI declined to comment for this story.
The money to purchase the 2010 upgrade was allocated from a “drug tax” fund, the records show.
A drug tax, also known as the unauthorized substance tax, is levied against citizens in possession of illegal narcotics. By law, North Carolinians are required to pay a drug tax within 48 hours of coming into possession of a controlled substance. The tax, which nets the North Carolina government millions of dollars every year—75 percent of which is reportedly allocated back to law enforcement—ranges from $3.50 per gram of marijuana and $50.00 per gram of cocaine up to $200 per gram for other narcotics illegally sold by weight.
Just as drug arrests overwhelmingly target communities of color, disruptions caused by Stingrays also disproportionately impact minority communities, according to civil rights groups criticizing police use of the device. Rend Smith, communications director at Working Narratives, says the purpose of his organization is to expose the increased scrutiny of these targeted communities. “New technologies are increasingly being adopted by law enforcement agencies already struggling with inbuilt bias, and will ultimately exacerbate racial disparities,” he says. “The mainstream media have largely failed to tell the story of this trend, and so we began a campaign focused on exposing it.”
The Free Movement Campaign, founded by Working Narratives under the direction of Executive Director Nick Szuberla, began investigating the use of Stingrays in North Carolina as part of a state-based effort to shine a light on the lack of protection from surveillance and police militarization overwhelmingly affecting communities of color. “In terms of Stingrays, a surveillance technology that scans for and captures cellphone communication, the civil liberties threats are particularly egregious—with law enforcement agents making a concerted effort to avoid court oversight and keep the public in the dark,” Smith says.
Working Narratives, he adds, intends to continue targeting “strategic counties and municipalities” with public information requests concerning police surveillance practices.
Avoiding the courtroom
One focal point of police secrecy on Stingrays has been the witness stand. An email exchange between officials at the New Hanover Sheriff’s Department obtained by the Daily Dot, which accompanied the DOJ’s Stingray warrant, reveals the concerns of officers who may be called to testify about their department’s surveillance practices.
The FBI has gone to extraordinary lengths to keep local, state, and federal law enforcement quiet about the surveillance device—even if it means dropping a criminal case. Faced with the prospect of revealing information about Stingrays in court, prosecutors around the country have repeatedly dropped criminal charges. Non-disclosure agreements between the FBI and other agencies specifically prohibit talking about Stingrays even in court, an unprecedented step in the name of secrecy and surveillance in the United States.
The 2014 email exchange shows members of the New Hanover Sheriff’s Department strategizing over how to avoid the witness stand by having other officers sign affidavits. One officer who dealt with every pen register affidavit across the department sought advice from others on how to “keep me off the witness stand.” The full reasoning behind the exchange is unclear.
“Perhaps there is a legitimate reason for this if he isn’t substantively involved with the pen register orders involving the StingRay,” Katz-Lacabe says. “Or maybe it’s something more devious and aligned with the portions of the [non-disclosure agreement between the FBI and local police] that prohibit disclosure to the judicial system.”
Other emails obtained by the Daily Dot reveal the ways in which law enforcement view media coverage of Stingrays and the court battles meant to add transparency their use.
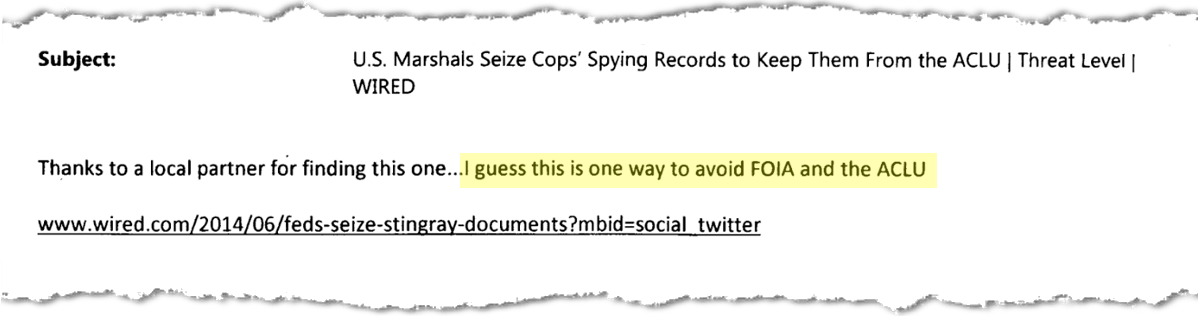
In an email thread, New Hanover Sheriff’s Department officers discuss Stingrays with an employee of the U.S. Secret Service. The employee, who does not appear to be communicating in an official capacity, forwarded to police a Wired news article describing how U.S. Marshals seized records related to Stingrays from a Sarasota, Florida, police department to prevent the documents from being released to the ACLU under public records law. The confiscation was described by Wessler at the time as “extraordinary” and “beyond the worst transparency violations.”
“I guess this is one way to avoid FOIA and the ACLU,” the Secret Service employee remarked.
SBI emails show the Secret Service had assisted North Carolina authorities with Stingray surveillance as far back as 2010. “This is problematic in that they are not always able to assist due to other core missions that naturally take priority within their agency,” one SBI agent wrote while requesting funding to upgrade his agency’s equipment.
In response to the Wired article, one New Hanover officer, apparently a member of a narcotics squad, replied: “Yep, saw it this morning. good thing none of us have a stingray… lol.”
A spokesperson for the New Hanover Sheriff’s Department declined to confirm whether the agency possesses a Stingray, though purchase orders from Harris Corporation suggest it does. After reviewing the documents, the department said it had “paid for maintenance on equipment that we use in our investigative processes.”
Another email from the same Secret Service employee contains several links to articles about Stingrays from outlets such as USA Today, Ars Technica, and Threatpost. The stories were accompanied by the message: “A compilation of recent propaganda for all to enjoy.”
Update 9:50am CT, Oct. 7: Added statement from DOJ.
Correction: A previous version of this article incorrectly cited the focus of prosecutors in New Orleans when they argued that citizens have “no expectation of privacy.” The case was addressing historical cell-site data collected by phone companies. We regret the error.