A data breach at a Missouri law enforcement agency in January left thousands of sensitive records exposed online, including jail incident reports, arrest records, and more.
Security researchers who discovered the breach at the Warren County Sheriff’s Department say the leaked backup files—numbering in the hundreds of gigabytes—also include multiple audio recordings containing police interviews with confidential informants, as well as witnesses and victims of crimes, raising concerns about the safety of the individuals exposed, as well as the integrity of police investigations.
“This type of data is extremely damaging for ongoing cases and to protect crime victims,” said Bob Diachenko at the MacKeeper Security Research Center, which discovered the breach on an unsecured network-storage device and reported it to Warren County in mid-January. MacKeeper said that the audio recordings included cases involving “child molestation allegations, weapons and drug charges.”
Other exposed files reportedly include crime-scene and incident reports, mail archives, detention officer files, and use-of-force reports.
It remains unclear for how long the data was accessible online—or whether the MacKeeper team was the first to discover it—but the breach was secured in February after the researchers contacted the sheriff’s department.
Reached for comment on Thursday, a Warren County employee said that no one authorized to discuss the incident was available.
In a twist, the MacKeeper researchers discovered a number of encrypted records on the unsecured network pointing to an unrelated ransomware attack. The files also included instructions on how to download and install the Tor Browser and pointed to a dark net website where the agency could submit a payment.
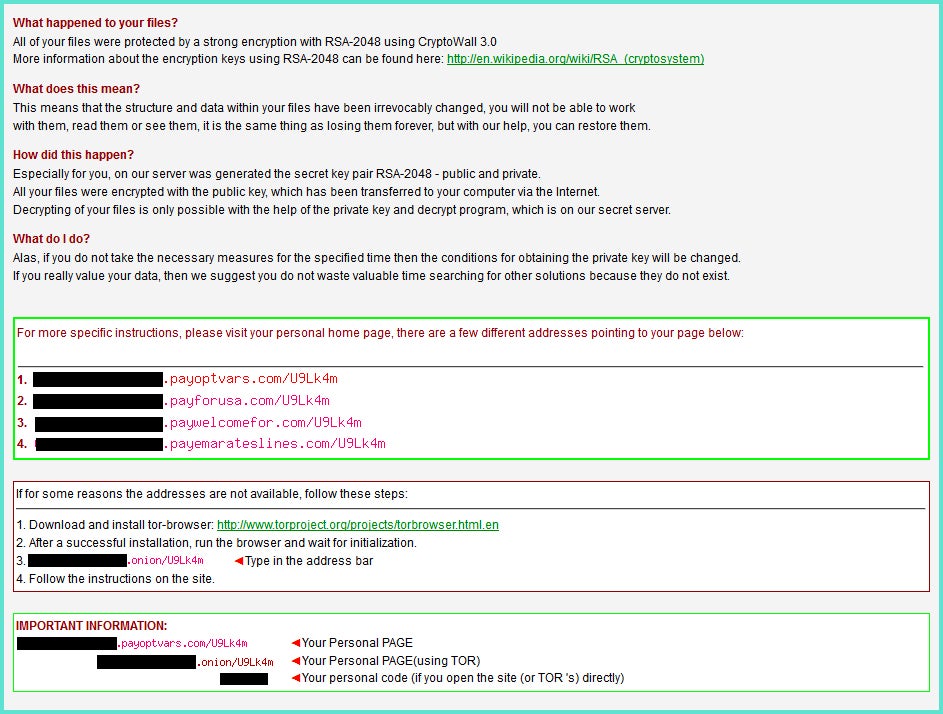
“Decrypting of your files is only possible with the help of the private key and decrypt program, which is on our secret server,” a letter to the sheriff’s department said. “Alas, if you do not take the necessary measures for [sic] the specified time then the conditions for obtaining the private key will be changed. If you really value your data, then we suggest you do not waste valuable time searching for other solutions because they do not exist.”
An IT employee at the Warren County Sheriff’s Department told MacKeeper by phone that the agency had fallen victim to a ransomware attack in mid-2016, but reportedly claimed that “no ransom was paid.” MacKeeper told the Daily Dot that the same ransomware instructions had previously been found in other organizations’ backup files similarly exposed online, including a major U.K. investment firm.
“Despite the amount of sensitive information in the backup database what really concerns researchers is the ransomware instructions,” the researchers said, explaining: “Ransomware is computer malware that executes a cryptovirology attack, locks the files and demands a ransom payment to decrypt it. More advanced malware can not only encrypt the victim’s files, but also back up data to a remote server where cybercriminals can review the files to see how valuable or sensitive they are.”
MacKeeper said it could not independently confirm whether the ransom was paid. “This would effectively mean that the citizens of Warren County had their data compromised by cyber criminals who could use the information for fraud or extortion,” they said.“Were citizens or state authorities informed that the data was leaked? Did local authorities pay the ransom?”
In January, MacKeeper unearthed—and helped to secure—a data breach at a major telemarketing firm in Florida. The breach exposed at least 17,000 recorded telephone conversations in which customers provided sensitive information, including their credit card details. In total, nearly 400,000 calls had been left accessible online.


