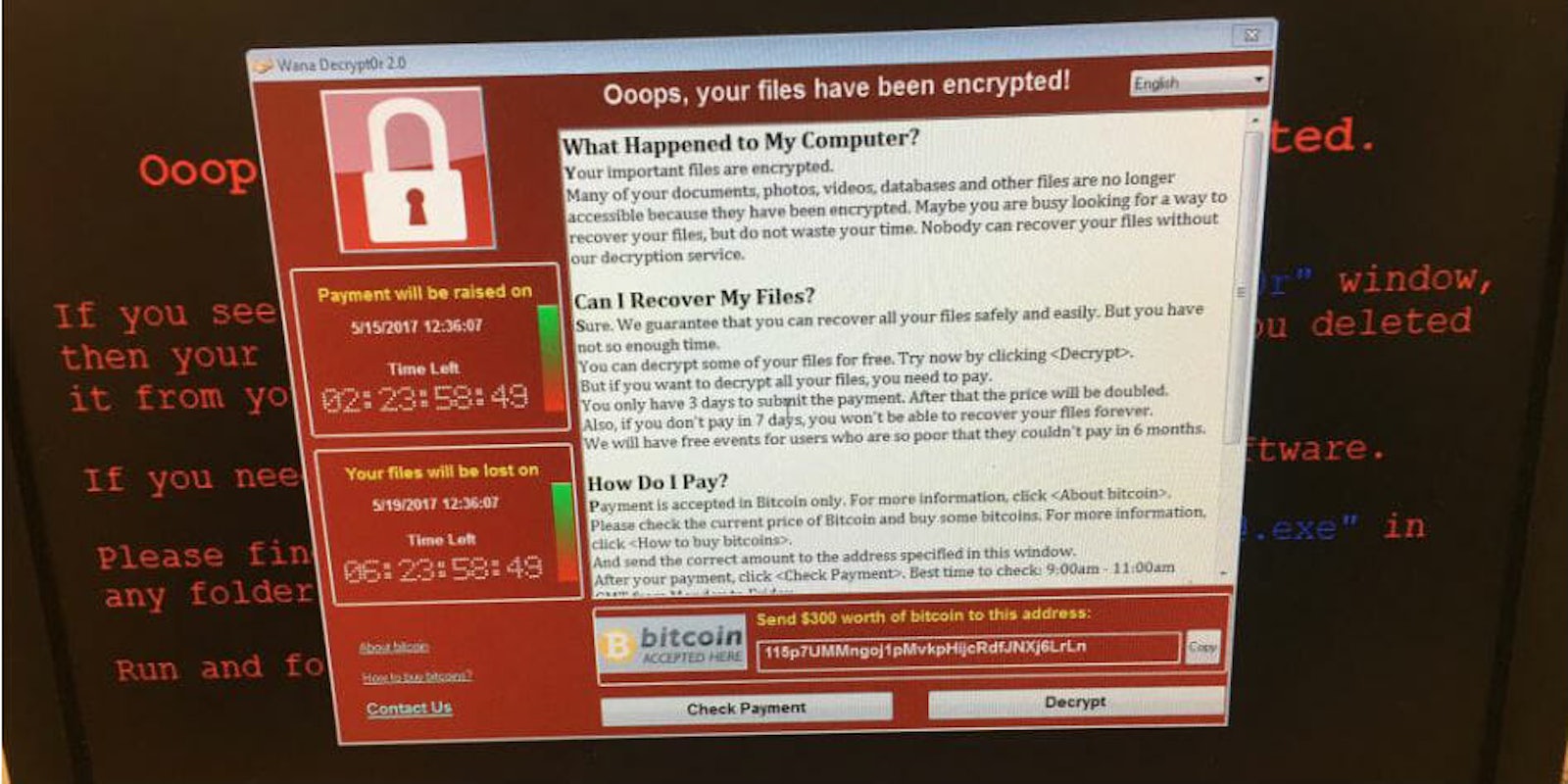
A widespread cybersecurity attack using leaked NSA hacking tools is infecting computers in tens of thousands of locations throughout the world, according to a BBC report. The infected software appears to be launching a large-scale ransomware campaign against dozens of organizations, including hospitals and telecom companies.
Ransomware is a debilitating form of malware that breaks into a system and locks users out by encrypting all of their files. That data is then held as “ransom” until the hacker’s demands are met.
The software in today’s massive attack, a variant of “Wanna Cry,” was spread via email, and demands $300 in Bitcoin. Reports of infected computers have been seen in as many as 99 countries, including the U.K., U.S., China, Russia, Spain, Italy, and Taiwan.
“Affected machines have six hours to pay up and every few hours the ransom goes up,” Kurt Baumgartner, the principal security researcher at Kaspersky Lab, told CNN. “Most folks that have paid up appear to have paid the initial $300 in the first few hours.”
36,000 detections of #WannaCry (aka #WanaCypt0r aka #WCry) #ransomware so far. Russia, Ukraine, and Taiwan leading. This is huge. pic.twitter.com/EaZcaxPta4
— Jakub Kroustek (@JakubKroustek) May 12, 2017
The British National Health Service (NHS) is currently under siege and was forced to reject patients, cancel operations, and reschedule appointments. People needing medical attention in areas that were attacked by the ransomware have been told to seek care only in emergency situations, according to a report from Reuters.
“We are experiencing a major IT disruption and there are delays at all of our hospitals,” Barts Health Group, which manages major London hospitals, told Reuters.
Our statement on the reported ransomware issues: https://t.co/Pt47dvpbiR #nhscyberattack
— NHS England Digital (@NHSDigital) May 12, 2017
British Prime Minister Theresa May was briefed on the incident earlier Friday morning. Sixteen U.K. organizations have been affected by the ongoing attack, according to the latest update from the NHS, which added that there is no evidence patient data has been accessed.
Pharmacist Chris Magquire wrote on Twitter that even a general practice facility had to shut down computers and begin writing with pen and paper.
All shut down in Yorkshire-even in GP practice. Back to handwriting notes while seeing patients without full histories! #nhscyberattack
— Chris Maguire (@chris_magz) May 12, 2017
Jakub Kroustek, malware researcher at Avast, says there are 57,000 “Wanna Cry” detections so far, which are mainly being targeted to Russia, Ukraine, and Taiwan.
57,000 detections of #WannaCry (aka #WanaCypt0r aka #WCry) #ransomware by Avast today. More details in blog post: https://t.co/PWxbs8LZkk
— Jakub Kroustek (@JakubKroustek) May 12, 2017
Here is a photo of how the ransomware appears on infected computers.
https://twitter.com/fendifille/status/862997621039878145
Other victims of the attack include Spanish telecom giant Telefónica, which said the infection was limited to some of its computers on an internal network and did not affect clients or services. Portugal Telecom and Russia’s MegaFon were infected as well.
Delivery company FedEx was also a target, though it didn’t specify in which regions.
“Like many other companies, FedEx is experiencing interference with some of our Windows-based systems caused by malware,” it said in a statement. “We are implementing remediation steps as quickly as possible.”
The malware campaign is growing into one of the largest attacks in history.
“This is a major cyberattack, impacting organizations across Europe at a scale I’ve never seen before,” security architect Kevin Beaumont told the BBC.
Many security researchers have linked the attack to leaked NSA tools used to exploit vulnerabilities in Microsoft Windows computers. A group that calls itself “The Shadow Brokers” claims to have stolen hacking tools from the NSA, and started posting them online last year. In March, Microsoft says it released a patch for its Windows operating system that fixed flaws that made it vulnerable to the hacking tools, though many computers have not been updated with the latest software.
The incident highlights problems groups have protecting sensitive information. Organizations that have the responsibility of keeping customer’s sensitive records safe can often avoid being targeted by attacks like ‘Wanna Cry’ by simply keeping their systems up-to-date.