The Tor network is designed to cloak its users with powerful location- and identity-masking technology as they use the Internet. It’s no surprise, then, that eavesdroppers regularly try to pierce that the anonymity network’s protection to discover who Tor users are and what they’re doing.
New research from Princeton University and the Tor Project identifies some of the most aggressive spies on the network: so-called “Sybil” attackers who create many pseudonymous identities and thus exert an exceptionally large influence over the network.
Sybils can wield that influence in many ways, including deanonymizing Tor users, sniffing traffic, website fingerprinting, disabling hidden services, and harvesting the addresses of otherwise hidden “bridges” that allow people in countries where the Internet is heavily censored to connect to the network.
This access represents a valuable level of insight into the activities of Tor users, and one can achieve it by contributing to the relays on the network (Sybils) and owning as much of the Tor ecosystem—which totals over 7,000 such relays—as possible.
Sybil attacks are not theoretical, nor are they limited to Tor. They can and do hit various kinds of decentralized networks.
Carnegie Mellon University’s Software Engineering Institute, which receives funding from the U.S. government, used Sybil attacks as part of a multifaceted attack on Tor in 2014. Federal authorities subpoenaed SEI to learn the IP addresses of Tor users, resulting in numerous arrests of suspected criminals who had used the service.
Tor developers claimed that the FBI paid CMU $1 million to conduct the attack, though they offered no supporting evidence.
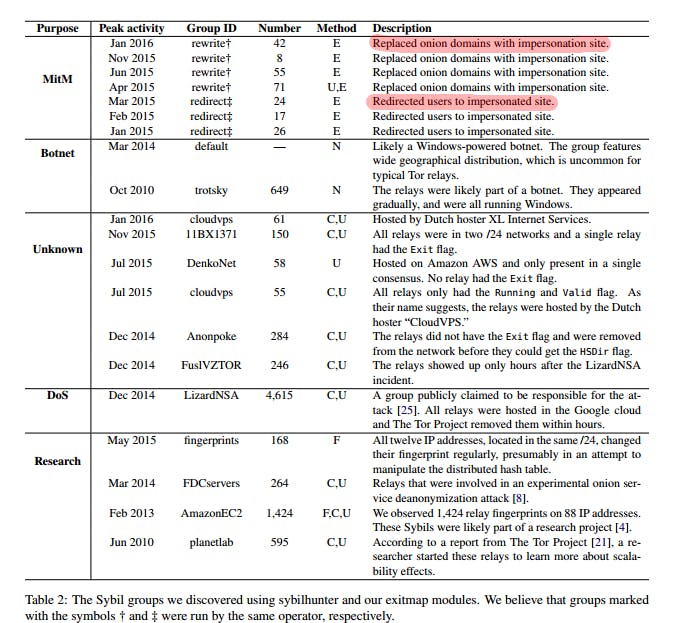
To beat back Sybil attackers, researchers wrote a program called sybilhunter that detects and exposes the attackers by analyzing nine years of Tor network information, including 100 gigabytes of data and millions of files.
They found 20 groups of Sybils, some of which were engaged in various types of malicious operations. Some were running denial-of-service attacks, in which computers flood Web servers with traffic to overwhelm them. Others were surreptitiously stealing data through man-in-the-middle attacks. And still others were running botnets.
The researchers reported the Sybil attackers to Tor developers, who blocked them.
You can read the full research paper below:
Correction: Not all found groups of Sybils were engaged in malicious operations. Additionally, there’s no reason to believe the botnets were being used to unmask Tor users.
Photo via Ruiwen Chua/Flickr (CC BY 2.0) | Remix by Max Fleishman