On June 5 of this year, the Guardian began publishing reports of the U.S. National Security Agency’s massive online spying operations. As the world would soon find out, the classified documents were given to the paper by former intelligence contractor Edward Snowden, who is now a fugitive living under asylum in Russia. In the past seven months, the Guardian, as well as the Washington Post, Der Spiegel, the New York Times, O Globo, and other outlets have been publishing details of the NSA’s various spy programs, most based on Snowden’s files. The leaks have sparked a global debate about the nature of privacy on the Internet and have forced the world articulate the type of future we want for our digital selves.
To place these leaks in any absolute ranking from most to least importance is, of course, futile (even after setting aside the fact that the true scope of many of these operations may have yet to come to light). As former Guardian journalist Glenn Greenwald put it to the Daily Dot, “their effect has been cumulative and it all depends on what metric you use.”
With that in mind, the leaks on this list were chosen (and to some extent ordered) for their contribution in conveying to the public the current character of the NSA’s surveillance program: its scope, its mentality, its motives, its operations.
These are, in other words, the leaks most important for forming a clear and complete picture of the highly secretive spy agency.
1) Metadata collection from Verizon: NSA collects the phone records of millions of Americans
Despite the general ambiguity surrounding any attempt to rank these programs definitively, the NSA’s dragnet collection of Americans’ telephony metadata—the who, when, and where of their calls—is decidedly number one with a bullet.
This was the very first leak published from Snowden’s trove of stolen documents. Posted by the Guardian on June 5, it revealed to the world that the secretive Foreign Intelligence Surveillance Court issued an order for the telecom giant Verizon to turn over the phone records of millions of Americans. The story would set the tenor for seven subsequent months of NSA spying revelations: It introduced Americans to the FISC, which, despite being charged with protecting their privacy from government surveillance, has denied only a handful of the thousands of state requests for (often bulk) data collection since it was created in 1978. The leak also raised questions about previous statements made by Director of National Intelligence James Clapper, who months earlier denied that the NSA collected bulk data on millions of U.S. citizens. In December, a federal judge ruled that the collection program may in fact be unconstitutional, making it the first NSA program successfully challenged in federal court.
Also in December, Greenwald testified before an E.U. committee inquiring into U.S. surveillance. In the hearing he stated that according to Snowden’s trove of secret documents, metadata collection was the “supreme priority” of the NSA. “It isn’t just surveillance experts that think that way,” he told the committee. “It’s the NSA itself.” When the Daily Dot asked Greenwald about which program should occupy the top spot on this list, he echoed those sentiments: “If forced to choose,” Greenwald said, “I’d say it was that Verizon story, because it was first, implicated all Americans, was so clear in its content, destroyed the credibility of NSA officials, and infuriated Congress.”
2) XKeyscore: NSA monitors browsing histories, emails, chats
Snowden disclosed the existence of a handful of different NSA monitoring programs. But XKeyscore stands out for several reasons: First, according to a report on the program published in late July by the Guardian, the NSA considers it to be the “widest-reaching” surveillance tool in its arsenal. Connected to a massive searchable database of chats, emails, browsing histories and login information, the program, by the agency’s own reckoning, allows agents to monitor “nearly everything a typical user does on the Internet.”
One of the most striking aspects of the leak was how it illuminated the shortcomings of the agency’s so-called minimization procedures. Legally, under the legislation such as the Foreign Intelligence Surveillance Act which was designed to protect Americans from foreign surveillance operations, the NSA can only perform warrantless surveillance on Americans if they are communicating with a known target, a person outside the U.S., or are themselves outside the country. As the XKeyscore leak revealed, all agents had to do to satisfy this standard was to select from a dropdown menu which of the above justifications they believed qualified a person for online surveillance.
XKeyscore was the first program to suggest the extent of the NSA’s partnerships with other intelligence agencies around the globe. As Der Spiegel reported, the U.S. shared access to XKeyscore with Germany’s domestic and international intelligence agencies. The close relationship, ostensibly justified by the high level of terrorist activity in Germany, began to suggest that the NSA’s embrace of surveillance had spread to countries in Europe and beyond.
3) PRISM: NSA uses secret court orders to obtain Americans’ social media data
Revealed jointly by the Guardian and the Washington Post on June 6, the NSA’s PRISM program collects citizens’ social media data from Silicon Valley companies like Google, Facebook, Yahoo, Apple and Microsoft. PRISM is far from the most damning of Snowden’s leaks, but it is arguably the most widely publicized as it was the first to suggest the NSA was engaged in extensive online surveillance operations.
PRISM functions by obtaining warrants for Americans’ private online data through the secretive FISC. For Silicon Valley, the leak was devastating. Email and social media companies have long grappled with the issue of user privacy. Although they were forced to disclose their customers’ information under a gag order, the leak nonetheless caused Americans to question how wise it is to entrust their personal information to Internet corporations. Around the world, the response was similar. International email clients saw a boon in new customers and countries began discussing ways of softening the U.S.’s grip on Internet infrastructure. It is estimated that PRISM cost technology companies as much as $35 billion.
The financial losses may in fact run much higher in the future. A more recent disclosure revealed that the NSA tapped directly into Google and Yahoo’s offshore cloud servers to directly monitor traffic. Neither company was aware the infiltration had taken place.
4) The identity of Edward Snowden
In the immediate aftermath of the Verizon metadata and PRISM leaks in early June, the world still didn’t know who had turned the documents over. On June 9, from a hotel in Hong Kong, 29-year-old Edward Snowden came forward.
In the videotaped interview with Greenwald, Snowden explained himself: “When you’re in positions of privileged access like a systems administrator for the sort of intelligence community agencies,” he said, “you’re exposed to a lot more information on a broader scale than the average employee, and because of that you see things that may be disturbing but over the course of a normal person’s career you’d only see one or two of these instances.”
Snowden’s point, in other words, was that it wasn’t so much any individual at the NSA who had acted illegally—it was the institution as a whole that had strayed from its Signals Intelligence roots (somewhat without the knowledge of individual actors). This phenomenon of 20th century bureaucracies was popularized in the 1960s by journalist Hannah Arendt, who dubbed it “the banality of evil.” By diagnosing the systemic overreach of the NSA, Snowden was able to add a broader framework to the seven subsequent months of reports his massive trove of documents would produce.
By making his identity public, Snowden also effectively made public the complicated political relationship of countries around the world on issues of privacy rights: He fled to Russia, where he was granted asylum in large part no doubt because of the Cold War-era animosity that still exists between the U.S. and Russia. While Snowden’s leaks would reveal many spying programs in European countries, no nation offered him protection, as many are nurturing close, economically beneficial ties with the U.S., notably right now through the Transatlantic Trade and Investment Partnership for example. Meanwhile, a group of South American nations indicated a willingness to assist the fugitive leaker. In large part, this willingness reveals the ways in which South America has had less influence over the growing Internet economy.
5) Bullrun: NSA has sewed encryption backdoors into the Internet
The NSA’s interest in breaking the encryption schemes that protect much of the communications moving across the Internet was revealed by the New York Times in early September. On some level, the efforts aren’t surprising. Any national security-minded outfit focused on intelligence would certainly prioritize cracking cryptic communication. However, the Agency had taken the operation much further, attacking the schemes that protect medical records, banking transactions, and everyday communications on the Web.
Perhaps the most notable aspect of the leaked program, known as Bullrun, is that the agency spent billions in the past decade to insert backdoors into the world’s encryption schemes. Essentially, the agency helped sew deliberate weaknesses into the techniques that protect the most sensitive and personal communications online. One might argue that as long as the agency is the only outfit with access to these holes, there is little to worry about. Regardless of your opinion on that notion, many programmers have pointed out that theoretically, anyone can access these encryption loopholes. In other words, in its mission creep, the agency has made Internet encryption fundamentally weaker and more vulnerable to attack by malicious third-party hackers.
6) Parallel construction: NSA shares data with the DEA
In early August, the only leak on this list not to come from Edward Snowden was revealed by Reuters. According to anonymous sources and documents reviewed by the news agency, the U.S. Drug Enforcement Agency uses data obtained by the NSA to investigate domestic drug cases which are out of the jurisdiction of the spy agency.
The leak was problematic because the U.S. government had, up until August, argued that while Americans’ information may have been swept up in the NSA’s various collection programs, it was not put to use because this would be a violation of citizens’ Fourth Amendment rights to privacy. Counter to this claim, the Reuters story revealed that in fact the agency did share its information with domestic law enforcement agents. In short, that opened up the door for data illegally obtained under the justification of national security to be used in domestic criminal trials. It was later revealed that NSA data was also shared with the Internal Revenue Service.
The Electronic Frontier Foundation called this leak “one of the biggest dangers of the surveillance state.” Not only was the DEA using NSA data to prosecute citizens, but it was doing so in secret. Through a method disclosed by Reuters known as parallel construction, DEA agents arrest criminals identified through NSA data but then report that they came across the criminal activity through other means than surveillance. The logic here is that the use of NSA data must be hidden or it would jeopardize the effectiveness of surveillance programs abroad. The end result, however, is that one could find themselves on trial based on evidence that was illegal obtained by the NSA and neither they, nor their lawyer nor the judge would ever know it. The constitutionality of this parallel construction is an open question.
7) The U.S. shares raw intelligence collected on Americans with Israel
When the Guardian revealed that U.S. shares raw signals intelligence on its citizens with Israel, the leak was comparatively ignored by the media. For this reason alone, it earns a spot on this list. The leak revealed that, according to a five-page document viewed by the Guardian, the NSA shares “unevaluated and unminimized transcripts, gists, facsimiles, telex, voice and Digital Network Intelligence metadata and content” of Americans’ communications.
While the document urged that the Israeli government respect the constitutionally guaranteed privacy rights of U.S. citizens, it appears to take no provision to ensure such urgings are heeded. In fact, it goes so far as to state, “This agreement is not intended to create any legally enforceable rights and shall not be construed to be either an international agreement or a legally binding instrument according to international law.” Further, provided the Israeli government conceal the identity of particular U.S. persons, it is free to circulate the NSA data. In sum, Americans’ private data, questionably obtained, is passed on to Israel with no enforcable restrictions on the use of that information.
8) NSA spied on U.N. video conferences
In August, Der Spiegel revealed that the U.S. spied on U.N. video conferences, decrypting some 450 conversations between international diplomats in the summer of 2012 alone. By any measure of scope, in comparison to most of the other surveillance leaks, this one is relatively minor. However, several factors make this revelation stand out: First, the surveillance runs counter to international law. Specifically, it violates the 1961 Vienna Convention on Diplomatic Relations, which bars member states from spying on one another during diplomatic missions. The reason for this law is that diplomatic missions are held sacred, as they are gestures toward peaceful resolutions between countries. By spying on the U.N., the NSA undermines this sanctity.
The leak also lead to the Obama administration’s suspension of U.N. surveillance in October. While Snowden’s files had up to this point provoked much international conversation about the boundaries of spying, this was one of the first instances where surveillance activites were actually suspended.
It should be noted that the leak revealed that diplomatic spying was not simply a U.S. problem. China too was engaged in similar activities, which gave credence to the NSA’s claims that its practices were not out of character with those of other countries.
9) NSA tapped German Chancellor Angela Merkel’s private cellphone
When it was revealed in October that the NSA tapped into German Chancellor Angela Merkel’s private cellphone, the story received top billing from media outlets around the world. It is included here not for its significance but for the questions it raised about whether or not the spying it revealed warranted the popular outrage that greeted it.
Unlike many of the leaks that showed how the U.S., U.K., Germany, Canada, and other nations spied on citizens of the world, particularly through the Internet, this leak was a case of one superpower spying on another’s leader. The outrage surrounding the leak suggested that the world (or at least the media) had decided that state-sponsored spying of any form was no longer acceptable. Short of this view, the tapping of Merkel’s phone certainly seems within the jurisdiction of an national security surveillance outfit. In the end, the reaction to the leak raises more questions than answered: Are we striving for a world where all surveillance of any form should be outlawed? Is Merkel’s anger at the U.S. justified or is Germany engaged in similar spying?
10) The Black Budget: How much the U.S. spends on spying
The list ends with a relatively straightforward revelation from the Washington Post: The U.S. spent $52.6 billion across 16 spy agencies and more than 100,000 employees in the fiscal year 2013. The NSA alone spent more than $10 billion in 2013, a 53 percent increase from 2004. Here’s how that money was spent:
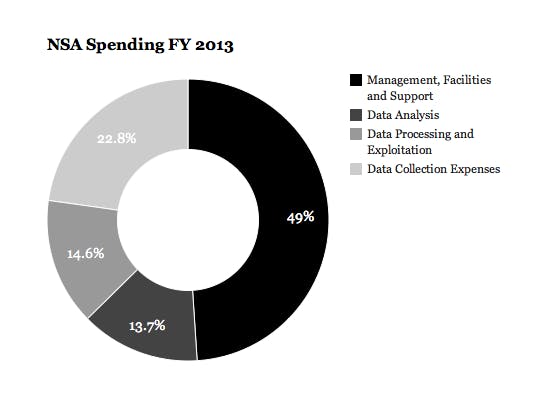
Further, the report revealed that the government has put half a trillion dollars into intelligence collection and surveillance since the Sept. 11 attacks on the World Trade Center. The massive injection of funds reflects the fundamental ideological shift that occurred inside the NSA after 9/11. As Thomas Drake, a former NSA senior executive who blew the whistle on the agency in 2006 told the Daily Dot that after the attacks the NSA’s priority became “to own the Internet.” The black budget reflects this decision.
•••
In his testimony before E.U.’s investigatory committee in mid December, Greenwald commented that, after viewing the trove of top secret documents leaked this year by Snowden, he was convinced that the NSA’s goal was the “elimination of privacy worldwide.” This, he assured the committee, was not hyperbole but a “literal description of what the NSA and its closest surveillance partners are attempting to achieve.” He went on to add that the philosophy of collecting everything was “repeatedly said in their private documents.”
While the vast majority of these documents will no doubt never be viewed by the public, the sentiment of the agency that created them has been fleshed out throughout 2013, and a clear picture of the world’s most powerful Internet surveillance outfit has begun to emerge.
Back when the NSA leaks started, in early June 2013, Snowden told Greenwald, “I’m just another guy who sits there day to day in the office, watches what’s happening and goes, ‘This is something that’s not our place to decide, the public needs to decide whether these programs and policies are right or wrong.’ And I’m willing to go on the record to defend the authenticity of them and say, ‘I didn’t change these, I didn’t modify the story. This is the truth; this is what’s happening. You should decide whether we need to be doing this.’ “
What we’ll ultimately decide remains to be seen—a different story for another year.
Illustration by Jason Reed


