Syria is taking the war against its own citizens beyond the streets of Homs and into their computers.
Over the past two weeks, pro-government forces have installed malware on activists’s computers through chats, emails, and a fake YouTube channel, the Electronic Frontier Foundation announced Thursday.
The YouTube phishing site hosted fake videos of the Syrian resistance. Except the videos didn’t work, and the site asked you to install an Adobe Flash Player update to view them. The update was an executable file that, if opened, would eventually give the hackers remote access to the computer used.
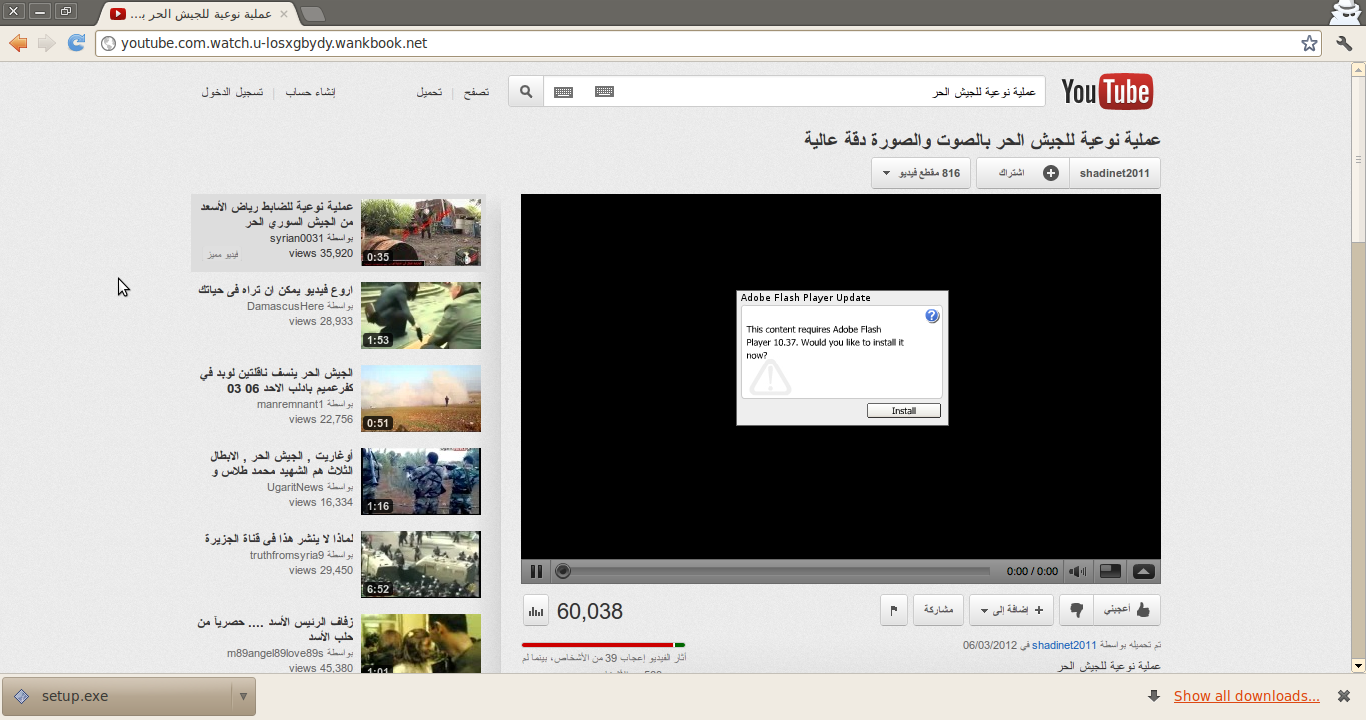
That particular phishing site has been taken down, but others may still be out there, the EFF warns.
“EFF is deeply concerned about this pattern of pro-government malware targeting online activists in authoritarian regimes,” the organization noted in a blog post.
In February, a CNN report uncovered similar malware that took control of activists’s web cams and stole passwords.
The free-Internet folks at the Tor project, meanwhile, analyzed the first batch of files used to attack activists, which the EFF first reported on March 5.
The batch included a fake PowerPoint slide that was actually a keylogger—a tool for recording what keys you’ve typed and a great way to nab passwords—as well as a phony screensaver that covered a back-door utility that gave Syrian operatives complete control over the targeted computer.
If you’re worried pro-Syrian spies might have taken control of your computer, the EFF has a couple of guides on how to find and delete the bad files.
Image via FreedomHouse


