In the hours after Donald Trump was declared victorious in his bid for the presidency, the notorious Russian hacker group alleged to be behind the DNC hack launched an organized phishing attack targeting American political think tanks and non-governmental organizations.
The criminal hacking crew behind it all are known mainly as “the Dukes,” but also as “Cozy Bear” or “APT29.” They’ve been connected to several major hacks and were known to have performed similar phishing campaigns in the past.
Phishing attacks are a popular form of email fraud. A perpetrator sends out a message that appears to come from a trustworthy source. Usually a link or attachment within the phishing email, when clicked, will install malware on the victim’s device. This malicious software then allows the criminal to access to all kinds of personal data, including financial information.
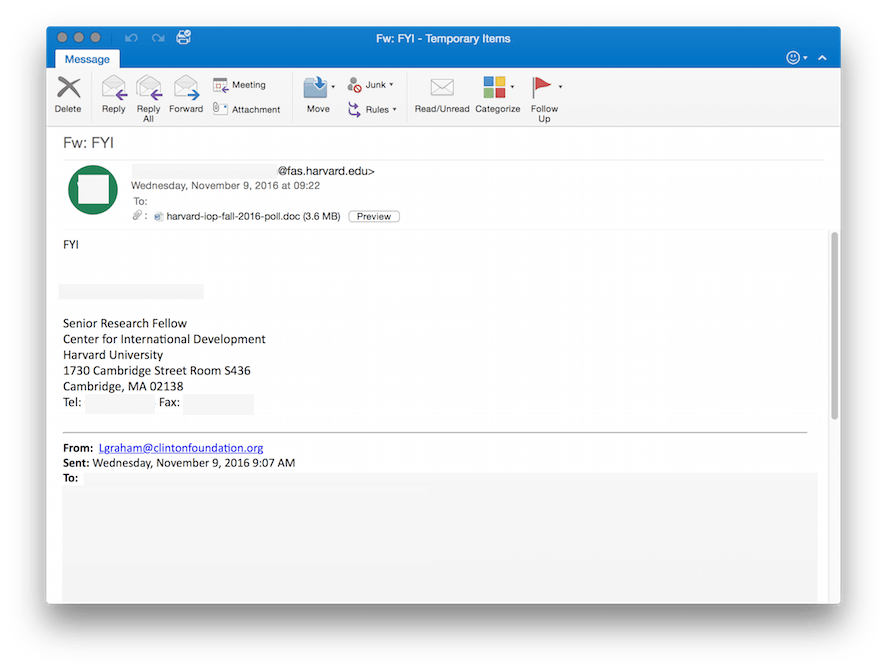
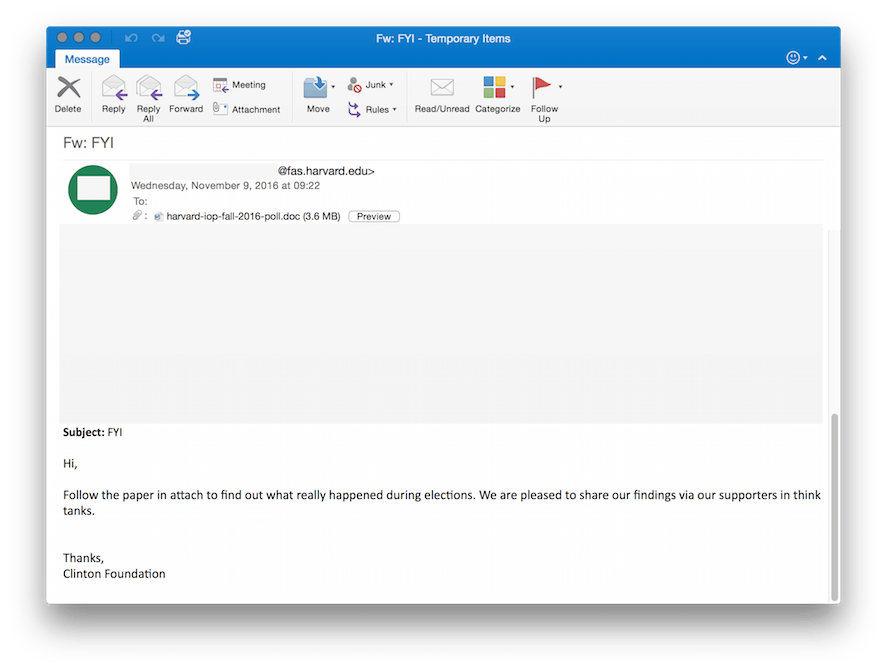
Two of the election-themed spear phishing emails deployed by the Dukes were disguised to appear as if they’d been sent from the Clinton Foundation, others came from compromised Harvard email addresses. The emails claimed to offer insight into the election, evidence of poll rigging, and included a PDF attachment: “Why American Elections Are Flawed.” Instead, users found that this attachment had been loaded with malware.
Cybersecurity research firm Volexity had been closely investigating the gang that develops a very specific signature brand of malware, which experts nickname PowerDuke, and released details on the attack in a report on Thursday morning.
“The PowerDuke malware [was] used in these most recent attacks,” the blog outlined. “Three of the five attack waves contained links to download files from domains that the attackers appear to have control over. The other two attacks contained documents with malicious macros embedded within them.”
The Dukes’ sophisticated malware tool creates a point of access for the hacker. It also analyzes the target computer, and in order to avoid detection by system administrators and security will stop activity.
In an interview with Krebs on Security, Volexity CEO Steven Adair commented that the organization was “well-funded and in some respects professional.”
Adair continued: “What they’re doing takes time and effort, and for eight-plus years now they’ve been in continuous development of new backdoors… They’re continually targeting different verticals— universities, NGOs, and governments—and they learn from others, retool and modify their attacks constantly.”
Volexity also alleged that the Dukes were one of the gangs behind the hacks on the DNC’s servers and the inbox of Hillary Clinton’s campaign chairman John Podesta. Material from both hacks ended up published on WikiLeaks.
The incident heightened international tensions as the Obama administration accused the Russian government of attempting to influence the presidential election. Vladimir Putin denied Moscow’s involvement, but some research organizations believe groups like the Dukes are part of a “hydra” of threat actors whom the Russian leader uses to fight his digital proxy wars.