A new study published by the Center for Internet and Society (CIS) at Stanford Law School suggests that the methods the NSA uses to determine reasonable and articulable suspicion (RAS) of terrorist activity may authorize the agency to examine the call records of more American citizens than previously believed.
The standard for NSA phone record acquisition, as defined by the Foreign Surveillance Intelligence Court, permits analysts to target individuals “three hops” from a terror suspect. In other words, a person who is talking to someone, who is talking to someone, who is talking to the suspect.
The three degrees of separation method used by the NSA sounds innocuous at first. After all, when the population of an entire city is at risk, who has time to gather evidence for a warrant?
After watching a few NCIS reruns, it’s easy to imagine how the plot unfolds: Islamic fundamentalists in the United States are contacted by their al-Qaeda leader in the Middle East. They receive instructions to commit an act of terrorism. These operatives then contact another associate, who transports explosives, or radioactive materials, perhaps, which were acquired from a nefarious black market dealer-type guy.
In the TV scenario, the NSA’s three-hop method gives intelligence analysts immediate access to the records of each conspirator—invaluable time wouldn’t be wasted trying to obtain four separate warrants. Of course, that’s television, where the privacy of millions of citizens wouldn’t be violated in this process; even if it were, surely the ends justify the means.
Unfortunately, in the real world, the benefits of providing the U.S. government with unfettered access into the personal lives of its citizens aren’t nearly as discernable. And historically speaking, the potential for abuse is simply too great to ignore. As the world recently learned, there are over 700,000 people on the U.S. terror watch list.
Likewise, there are are tens of thousands of individuals, which the government refers to as “seed” numbers, who have been designated by the FISA court as legitimate targets for record collection, CIS notes. These records are immediately accessible to intelligence analysts and the three-hop process can also be applied.
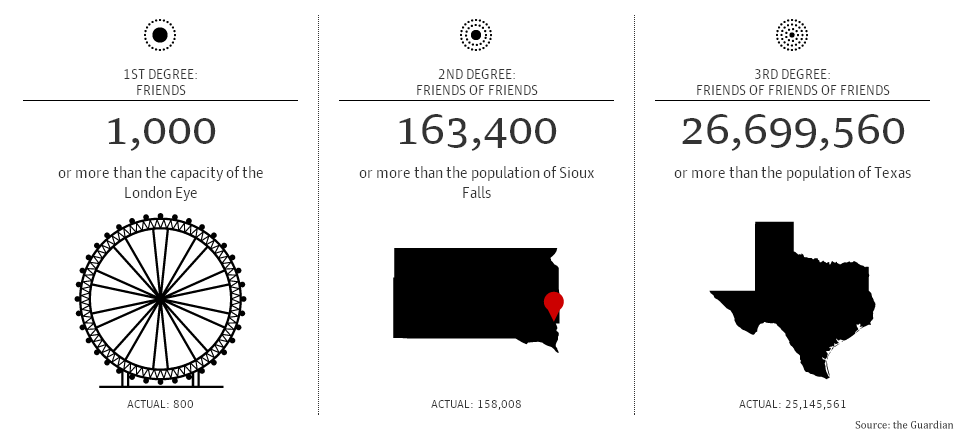
In October, the Guardian released an online tool which provides users with an estimation—derived from university research—of how far the NSA’s reach really extends, based on a calculation of Facebook contacts. Obviously, many Americans use mobile devices to access their social media accounts.
Based on averages, if a suspect has 190 Facebook friends, the NSA can legally access the records of 31,046 others by the second hop alone, which is more than Columbia University’s entire student body. By the third hop, the NSA would have access to the records of over 5 million individuals, or more than the entire population of Colorado.
By targeting an individual with 1,000 Facebook friends, the estimation of how many people can be linked through the three hops method becomes truly incredible:
CIS is collecting cell phone data through a recently launched mobile app called MetaPhone. The goal of the project is to reverse engineer NSA surveillance by collecting information volunteered by willing subscribers. With enough data, the Stanford researchers hope to provide the public with a better understanding of exactly what kinds of information might be collected by their government. MetaPhone hasn’t been working long, but already the dataset has yielded some interesting results.
As CIS explained, “Given our small, scattershot, and time-limited sample of phone activity, we expected our graph to be largely disconnected. After all, just one pair from our hundreds of participants had held a call.”
“Surprisingly, our call graph was connected,” CIS said. “Over 90 percent of participants were related in a single graph component. And within that component, participants were closely linked: on average, over 10 percent of participants were just two hops away, and over 65 percent of participants were four or fewer hops away!”
CIS research shows that numbers dialed frequently by individuals, with seemingly no other connection to one another, may link entire populations—within only two hops. This could potentially be used as a kind of cheat, allowing NSA analysts to legally obtain the call records of most U.S. citizens.
According to CIS, by graphing their results, a “hub-and-spoke structure” was illustrated; not the diffused social network researchers previously imagined. An example of a common number used in the research was T-Mobile’s voicemail service. By factoring the number into the NSA’s three hop process, 45 million Americans were instantly linked, and with one hop remaining.
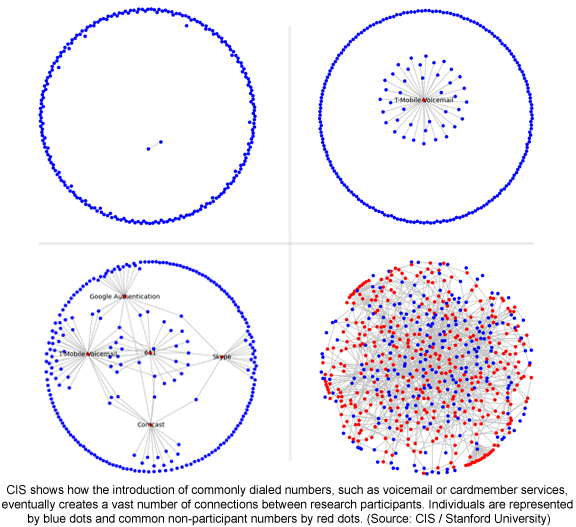
“Ever received a call from a Skype user? Authenticated your Google account by phone? You’re just two hops from everyone else in the same boat,” CIS said. Skype calls, the researchers claim, are placed by default from a small set of shared numbers.
Phone spam can also be factored into the NSA’s three step process, researchers noted. This is especially problematic because the entire point of spam is to reach as many numbers as possible.
While the users participating in the MetaPhone research aren’t precisely a microcosm of all American phone users, the figures provided by CIS do show how easily the NSA’s three-hop process can be abused. CIS also admits, “we do not know the properties of NSA seed numbers.”
“But our measurements are highly suggestive that many previous estimates of the NSA’s three-hop authority are conservative,” the researchers concluded.
H/T The Center for Internet and Society | Photo via Flickr


