A PowerPoint slide from an internal NSA presentation in 2012, included among documents leaked by Edward Snowden, details the agency’s malware-based Computer Network Exploitation program, Dutch news service NRC has reported. It appears that some 50,000 networks globally were at some point compromised by such routine intrusions.
The malicious spying software, distributed by hundreds of hackers working for the NSA’s Tailored Access Operations unit, provides remote access to infected computers, and can easily be toggled on or off—any given “implant” a digital “sleeper cell” to be woken at an opportune moment. A profile of TAO’s operations indicated that they’ve been keeping tabs on China this way for 15 years, almost since the department’s conception, and could at any moment launch a cyberattack crippling the targeted foreign devices if the president so ordered.
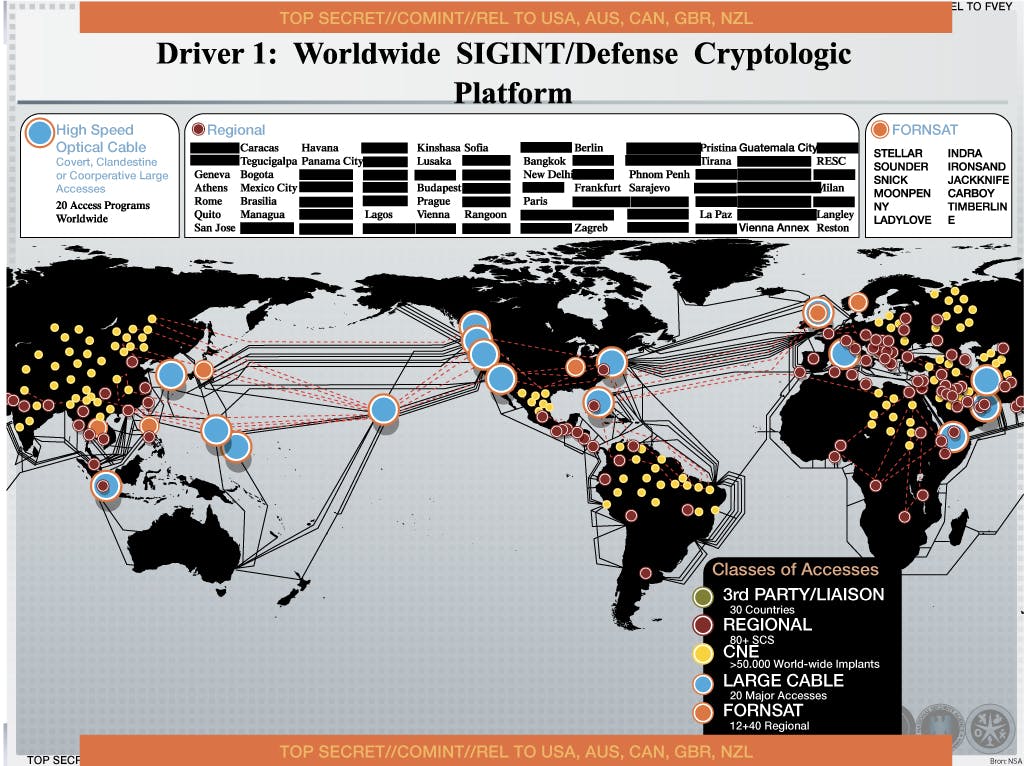
More likely, many security experts agreed, the real utility of the CNE is in eavesdropping and siphoning information to be shared between the so-called “Five Eyes” nations indicated in a legend at the bottom of the slide: the U.S., U.K., Canada, Australia and New Zealand. There’s also a good chance that TAO has been bugging telecoms and similar data hubs.
Over on Twitter, what looked like a typo turned out to be an interesting way of differentiating between independent cybercrime and military-backed network invasions. (“Stuxnet,” for example, is a computer worm discovered in 2010, thought to have been designed by the U.S. and Israel in order to infiltrate Iran’s nuclear operations.)
Only 50k milware installations globally? Must be restricted to the telcos, ISPs, banks, etc that allow for bulk collection.
— the grugq (@thegrugq) November 23, 2013
@alexm_py no, it was coined for stuxnet then dropped out of favor cause ppl was the emotive term “malware”, & “implant” sounds like boob job
— the grugq (@thegrugq) November 23, 2013
@octal like, 50k sites that are relevant to bulk monitoring, rather than everything
— the grugq (@thegrugq) November 23, 2013
@alexm_py yeah, HW makes sense. Milware is better for this stuff. Malware for criminal crap
— the grugq (@thegrugq) November 23, 2013
Even so, intelligence agencies are using methods familiar to petty hacker-thieves. From NRC:
One example of this type of hacking was discovered in September 2013 at the Belgium telecom provider Belgacom. For a number of years the British intelligence service—GCHQ—has been installing this malicious software in the Belgacom network in order to tap their customers’ telephone and data traffic. The Belgacom network was infiltrated by GCHQ through a process of luring employees to a false LinkedIn page.
The necessity for a “social engineering” tactic puts government spies on the same footing as some of the world’s most successful heist artists—no matter how sophisticated and discreet the malware or “milware” is, it still takes human error on the other end to deploy.