For years, hackers have been using MS Office macros in Word and Excel to target their victims with malware and ransomware. That’s why more recent versions of Office applications have macros disabled by default and warn users before enabling them.
However, a recent discovery by experts at FireEye and McAffee unveiled a critical zero-day vulnerability—an undiscovered security hole—that enables hackers to deliver malware without using macros.
Spy agencies and cybercriminal rings usually reserve zero-days for high-value targets in order to avoid giving them away. But this doesn’t cancel the possibility of some hacker group unleashing their wrath at random populations. Hackers are allegedly exploiting the vulnerability to target millions of users with Dridex, a notorious malware that steals banking credentials.
According to security experts, the attacks involve sending an email with an attached Word document. Once the document is opened, it connects to an attacker-controlled server from which it downloads and executes its malicious payload.
The attack bypasses most exploit mitigation measures, including those contained in Windows 10, Microsoft’s most secure operating system. It also opens a decoy Word document to erase its traces.
Microsoft issued a patch for the vulnerability on Tuesday. You should install it ASAP. But there are other general practices you can use to protect yourself against other MS Office vulnerabilities that will crop up in the future.
How to protect yourself against Microsoft Office hackers
- Start with adopting general cybersecurity hygiene, which means avoiding links and attachments in emails that come from unknown sources, keeping your system, software and antivirus up-to-date, and securing your passwords, especially those that belong to critical accounts.
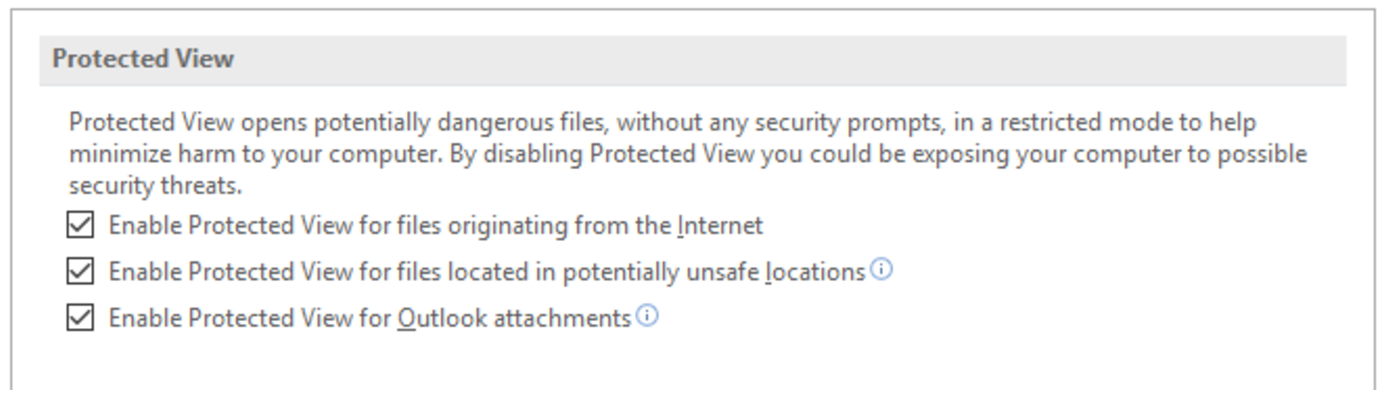
- By default, MS Word opens files from untrusted sources in Protected View, which disables features that might have malicious functionalities. However, some users find Protected View noisome and disable it. Don’t be one of them. You’ll regret it. To make sure Protected View is enabled by default, go to Options > Trust Center, then click on Trust Center Settings and go to the Protected View tab, and make sure all options are enabled
- Install Microsoft’s Enhanced Mitigation Experience Toolkit, a utility that helps control software functionality and prevent vulnerabilities being successfully exploited. Though it’s not clear whether EMET protects against this particular exploit, it adds a robust layer of overall defense against security holes.
- Use a limited user account. Most software vulnerabilities give attackers user level code execution capability. If you’re using a user account with administrative privileges, this means intruders will be able to do whatever they want with your computer. A limited user account, on the other hand, will minimize the damage and limit the scope of their destructive capabilities.


