When you’re excited to download an app, the last thing you want to do is read through all of its terms and conditions. It’s usually not until much later, when you’re unnerved about how personal the ad-targeting appears to be, that you start to wonder what you signed up for. But now, thanks to a team of researchers at three renowned institutions, there’s an easy way to see exactly what information your apps are sending and where that information goes.
The Lumen Privacy Monitor is a free Android application created by researchers at the International Computer Science Institute (ICSI), IMDEA Networks, Stony Brook University, University of Massachusetts at Amherst, and University of California, Berkeley, that will figure out which of your apps collects sensitive information, like your phone number or location, for advertising or tracking purposes, and who exactly those apps are sharing the information with.
There’s an irony to the Lumen Privacy Monitor, which is available for download in the Google Play Store: You have to grant the app all sorts of permissions to analyze your data in order to benefit from it—I admit, I had my own doubts—but its creators claim they are interested in where your data travels, not its content.
“I totally understand there is always ethical and privacy-related considerations when trying to do something like this,” said Abbas Razaghpanah, a Ph.D student at Stony Brook University. “To that, we are a research organization. Our interest is in studying the data, not the people. We are just interested in the app, not what people are doing in the apps, and all of the data we collect is anonymized.”
I downloaded Lumen to see what I could find out about my other mobile apps. What I discovered led me to uninstall some suspicious apps. Here’s how you can do the same.
How to set-up Lumen Privacy Monitor
Once you’ve downloaded and opened the app, you’ll see the Lumen monitoring state under the home tab. When you turn it on, Lumen will start tracking all internet traffic on your phone, and the other tabs will begin to populate. Here is a quick rundown of what those tabs mean, and how you can use them to your advantage.
Leaks
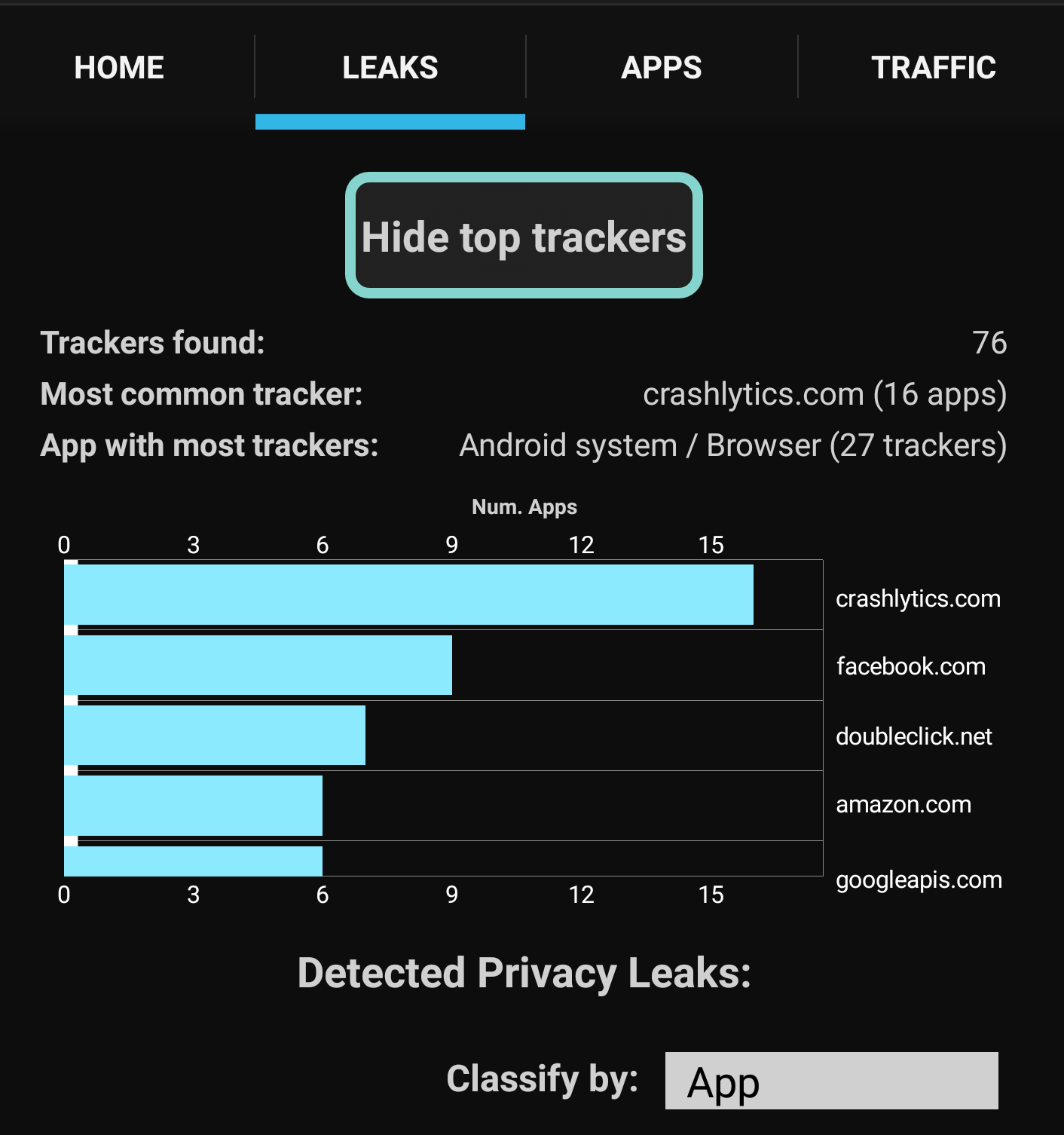
The leaks tab shows you what information has been “leaked,” which app sent that information, and the name of the analytics service receiving it. If you press on the “Show top trackers” button, you will see a graph of the top five data tracking services using your information, and the number of apps that send your information to those services.
READ MORE:
- The best free password managers
- What’s the most secure operating system?
- How to encrypt an iPhone in seconds
The graph on my Nexus 6P showed “crashlytics.com” received information from more apps than any other service. Crashlytics is a “crash reporting” software designed to help identify bugs in the thousands of apps that use it. It is also a monitoring service that reports everything you do in an app to its creators so they can take appropriate measures to ensure you don’t stop using their product. Interestingly, Facebook and Amazon also made it on my top five, along with Google ad service DoubleClick and Google’s application program interface. That wasn’t too surprising considering those companies’ reliance on ad revenue and dedication to offering catered content.
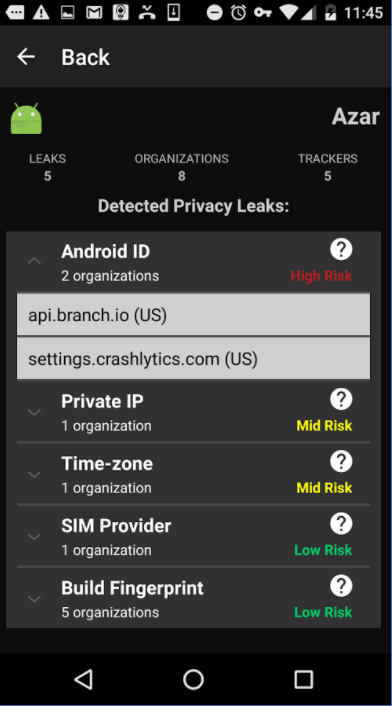
Scroll down a bit and you’ll see a scary list of topics that most people would consider private—for example, your Android ID, device model, hardware info, or time zone. If you see these categories, it means one of your apps is sending that information to another service.
READ MORE:
- The 10 best Facebook Messenger hidden features
- The best free VPN to maintain your privacy online
- TIL 25 fascinating facts about Reddit
- How to permanently delete Facebook
You can press on any of the permissions in the list to see the name of the app or organization using it. You will also see how many times they used it, and the last time they gained access.
The app conveniently tells you what each of these categories means, and the risk associated with them being leaked. I discovered Android ID has a “high risk,” and can be used by an app to track me across platforms when I search the web. This bit of information was being used by Groupon, so I immediately uninstalled the app and went back to using its desktop site. Build fingerprint, on the other hand, had a low risk, so I’m OK letting the dozen or so apps on my phone use that bit of data. It is this sort of insight that makes the Lumen app useful in helping you monitor where your data goes.

This info is particularly significant because the links between which apps send data and where can determine what you’ll see on those apps, and a lot of that data isn’t “privileged” by the operating system, so apps don’t explicitly need to request it.
“Imagine you have two apps: Facebook and Tinder. Both are using Crashlytics. The service now knows what phone the apps are on, in what time zone, and what you’re doing with these apps,” Razaghpanah said. “You won’t be surprised when you see an ad for another dating service on your Facebook feed.”
Analyzing your apps
The apps tab is similar to the leaks tab, but it breaks all your traffic down by destination. Press on one of the apps in the list and choose “see privacy leaks.” If you’re lucky, you’ll get a notification saying Lumen hasn’t identified any. Now choose an app you saw over on leaks. As you’d expect, the app will show you the same permissions it broke down in the leaks tab.
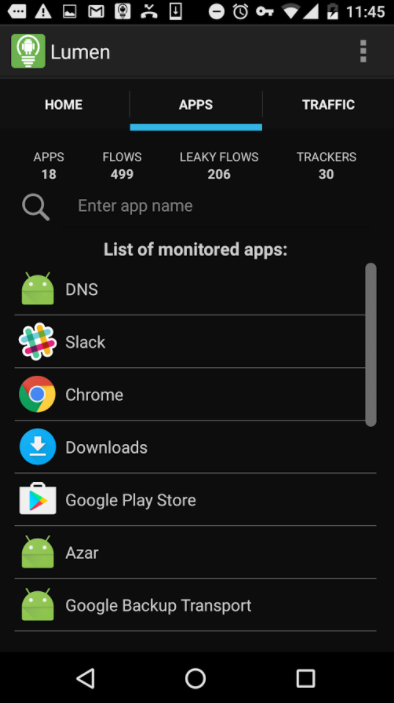
If you press on an app and choose “see traffic logs,” you will be shown a list of traffic stats broken down by the services being contacted. An eye icon means it is either an analytics or tracking service. Press on the three vertical dots to the left of the domain names. You should now be looking at a pop-up box that shows the percent traffic your app is sending to that specific location, which country that service is located in, how popular the service is, and what other apps use the same service.
In the example below, one of the ride-hailing apps I use is sending all of its data to Amazon, which the app claims is not a popular analytics service, ad network, or tracker. It also shows that five other apps including the Android system use Amazon.
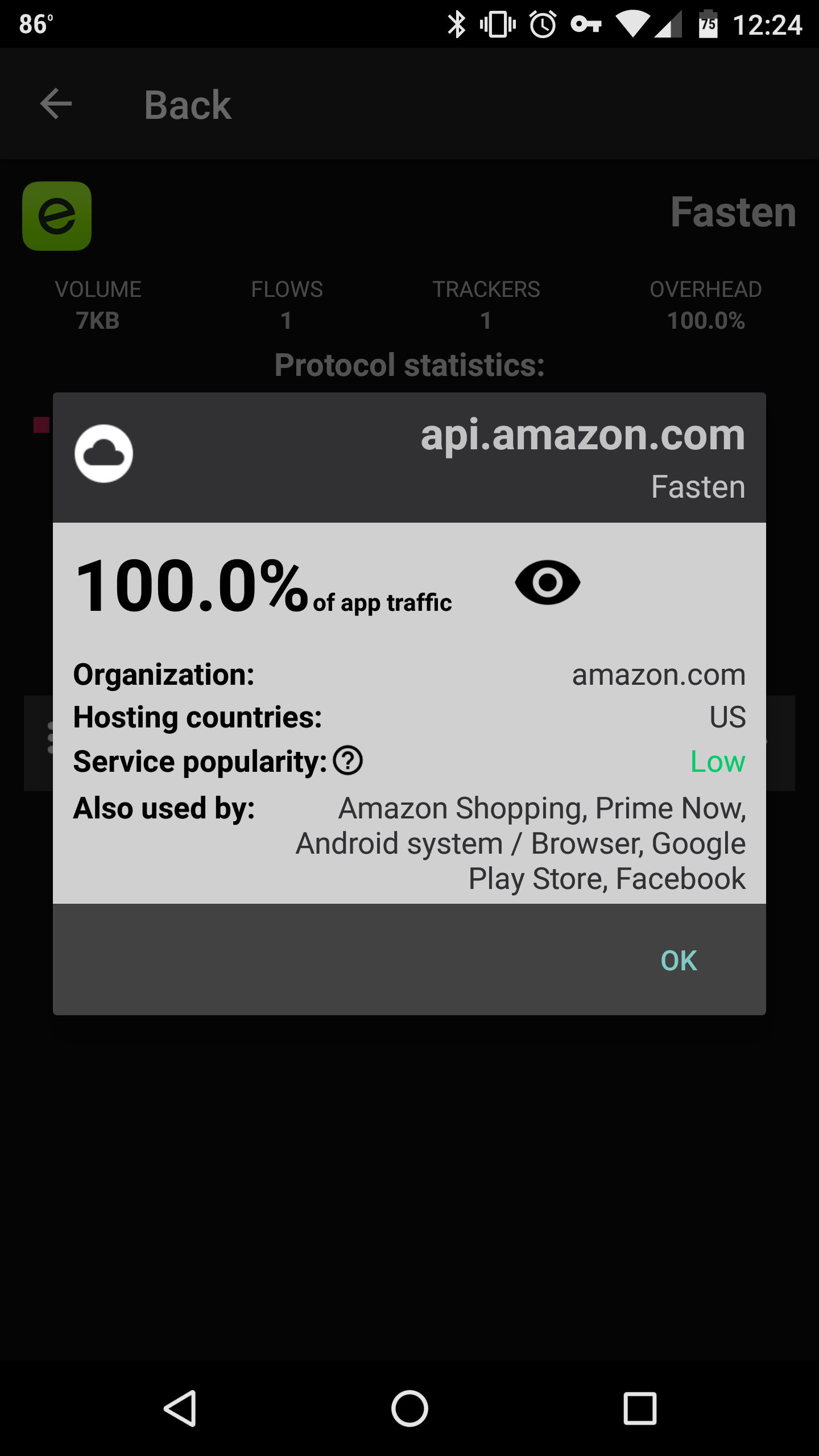
This dialog box gives you a good indication of the data traffic flowing from each of your apps, and the services using them. Chances are pretty good that a number of your apps send information to Crashlytics, which has a “very high” popularity (its SKD is installed on 2.5 billion phones). I found that 15 of my apps send info to the company.
Razaghpanah claimed that a number of these analytics services were first discovered by Lumen. “One very important thing we have uncovered is that a lot of these third-party tracking and ad services weren’t known in all the lists that have been compiled by people writing ad blockers,” he said.
Analyzing your traffic
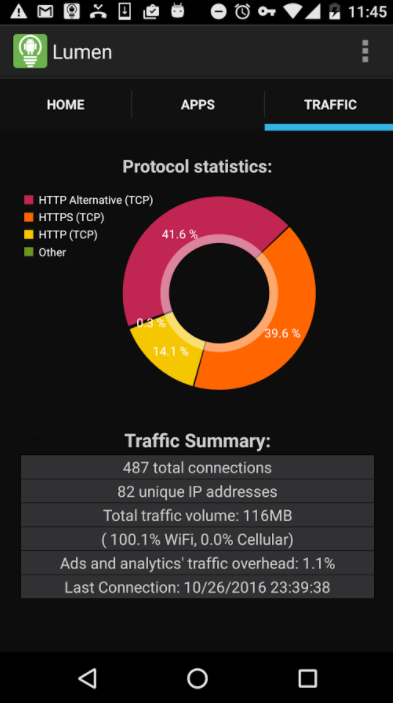
The last tab is the traffic tab, which tells you the number of unique IPs gathering data, the total volume of traffic being transferred, and the total number of connections. The main graph shows which protocols are being used. You probably won’t need to use this information, but it’s pretty interesting if you know what it all means. You’re in good shape if most of your apps use HTTPS, a communications protocol created to protect your privacy. A few of my apps also used QUIC, an experimental protocol created by Google and primarily used for gaming and streaming. I’d recommend doing a quick search online search if you see anything other than QUIC, HTTP, or HTTPS.
If you aren’t happy with the apps Lumen is tracking, or want to start tracking from scratch, you can press on the vertical dots on the top right corner of the app and press database. On the next screen, you’ll be able to wipe all data or individually remove data from individual apps.
In the end, Lumen told me a lot about the apps I had downloaded on my smartphone. I discovered that a few of them were sending information Lumen considers “high risk” to tracking and ad services. This led me to uninstall the apps and find alternatives. Fortunately, most of my applications were only sending low-risk data to Crashlytics, a data-monitoring company purchased by Google earlier this year. It’s nice to periodically keep tabs on what apps are doing with my information, but I did find Lumen became a lot less useful once I got rid of the bad apples.
Update 2:02pm CT, July 13: This article has been updated to include the full list of research institutions involved in the creation of Lumen.


