An iCloud hacking tool that could be behind the proliferation of illegally obtained nude celebrity photos has a few suggestions about making a stronger password. Well, 500 of them, really.
When a tool known as iBrute bubbled up to the surface of Hacker News yesterday, speculation turned to a vulnerability in iCloud’s Find My iPhone feature as a possible source for the cache of photos. And while it’s not clear if iBrute or a similar method was actually the route into the private photo collections of Jennifer Lawrence and others, the weakness in iCloud—which Apple has since patched—is certainly cause for alarm.
Posted to GitHub, iBrute is a brute-force tool, meaning that it breaks into an account by guessing one password after another in rapid succession. It’s a pretty crude kind of hack, made possible by weak passwords and an unsettling loophole in Find My iPhone that failed to shut out suspicious users after a handful of failed login attempts.
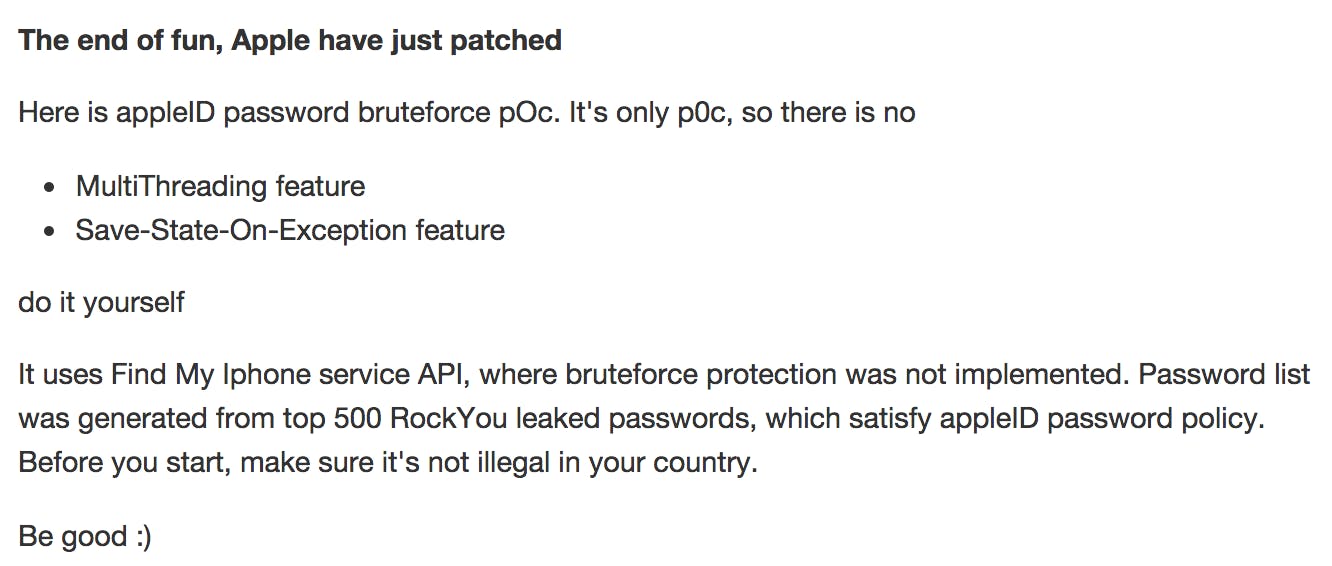
Making a strong password is always in style, but this list of 500 weak passwords that came packaged with the iBrute hack is so last season. Here are some highlights:
- Password123
- Fuckyou2
- Jesus777
- Jesusis1
- Princess4
- Princess23
- Princess19
- College1
- 1qaz@WSX (look at your keyboard)
- 1qaz!QAZ
- Devil666
- Death666
- Blink182
If your password looks anything like any of these, sprinkle in a healthy dose of extra characters, numbers, and symbols before it’s too late. And if your password has been “Blink182” since Enema of the State came out, you’ve got bigger issues.
H/T Kevin Poulsen/Twitter | Photo via Anonymous Account/Flickr (CC BY 2.0)


