The next time you’re in a hotel room, make sure to slide the deadbolt into the locked position. Researchers at Finnish cybersecurity firm F-Secure discovered a technique for building a master keycard that can bypass every locked room in a hotel. The exploit works on locks made by the world’s largest manufacturer and is estimated to affect 140,000 hotels in more than 160 countries.
The vulnerability was unearthed after a friend of researchers at F-Secure lost their laptop containing sensitive information in a mysterious hotel room break-in. The hotel staff was notified of the theft but dismissed the case after an investigation turned up empty. There were no indications of forced entry and no signs of access to the room entry logs. It was as if the laptop had vanished.
But two researchers at F-Secure, Tomi Tuominen and Timo Hirvonen, were convinced someone had found a stealthy way to break into the room and snatch the computer without leaving footprints. They focused their attention on the electronic lock that opens the room with a corresponding keycard and spent more than a decade searching for methods to compromise it.
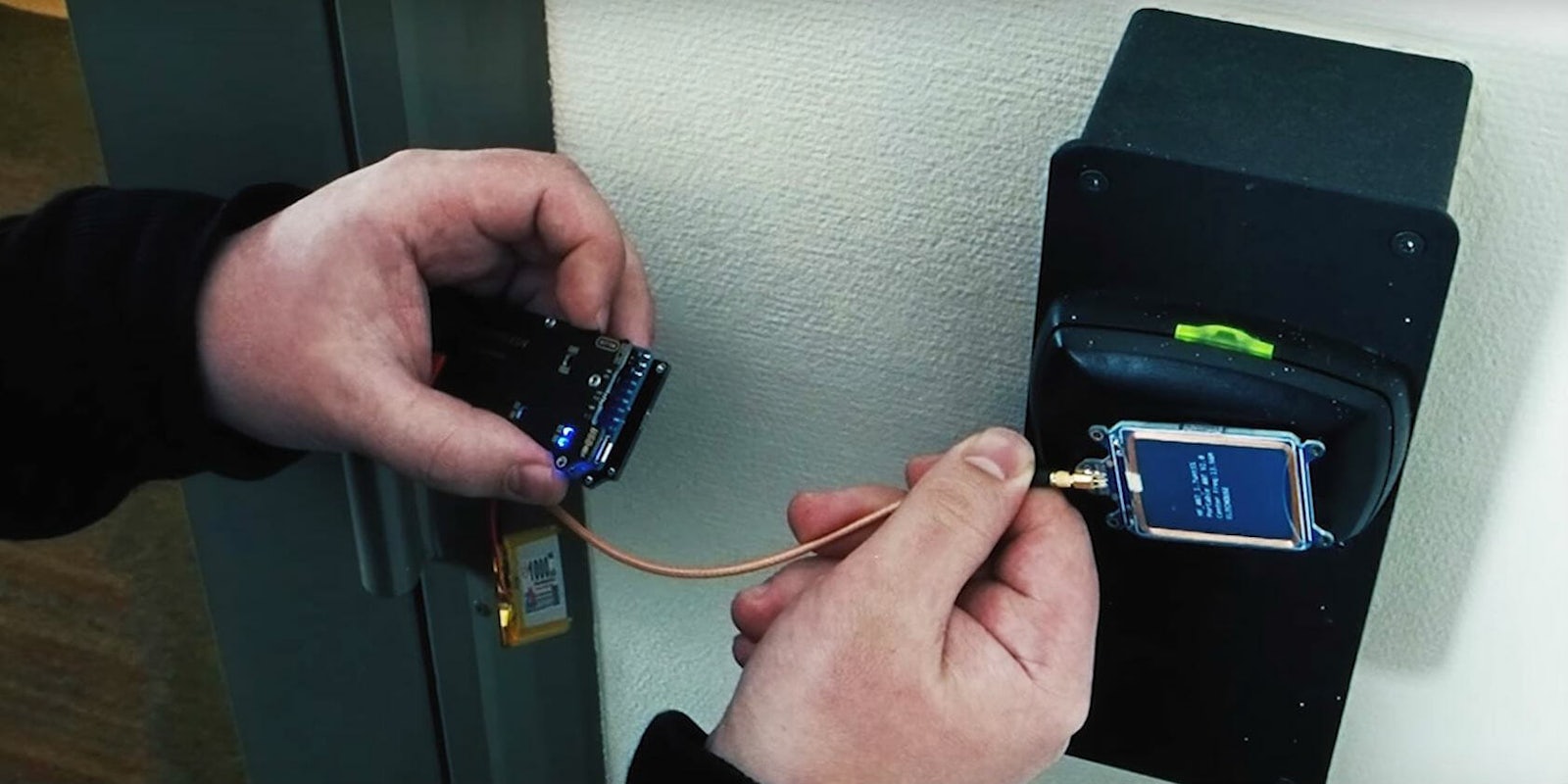
After thousands of hours of trial and error, the two researchers discovered a critical security flaw in the Vision by VingCard software system created by Swedish lock manufacturer Assa Abloy. With a $300 Proxmark RFID card reading and writing tool, bad actors could create a master key that would open any room in a given hotel. All they would need to do is obtain a keycard (even an old or expired one would work) and scan it using the card reading tool with complex cryptographic methods.
Once that’s done, the Proxmark device reads a piece of information on the card that identifies the hotel. It then simulates all possible codes for any key at the facility and flashes a red light for each incorrect keycard. After about one minute of searching, it flashes green and creates a master key capable of unlocking any hotel room. You can see the attack in action in the video below.
“This attack is pretty sneaky so by definition it would be very difficult to notice,” Tomi Tuominen, practice leader at F-Secure, told the Daily Dot. “Unlike many people think, the majority of hotel door locks are standalone. If we wanted to break into a hotel room, we can impersonate your key, the master key, or any valid key on that facility. We could get access to your hotel room, and you don’t know about it. Nobody knows about it. If you were to suspect something was going on, the hotel staff would have to manually extract logs from the door.”
Assa Abloy told F-Secure the problem affects millions of hotel locks but later said the number was between 500,000 and a million in a statement to Wired. That number could be even higher considering how difficult it is to get a firm number on how many hotels replaced their locks with new ones. The hack works on Assa Abloy locks that use the older Vision software, not its newer Visionline products, so hotels that have upgraded in recent years should be secure. The two security researchers said they collected more than a thousand keycards from friends over the last decade and found 30 percent of them were the older, vulnerable model. Hotels that use the Vision software include independent establishments, local chains, and some well-known global brands.
F-Secure will not divulge specific information on how to implement the attack in fear it would be used by burglars. In 2012, a security researcher disclosed details on how a hacker could breach an electronic lock system used in more than four million hotels. A few months after the reveal, a series of thefts were reported in Texas that affected vulnerable rooms.
Instead, F-Secure notified Assa Abloy of the vulnerabilities and worked with the company for the last year to deploy fixes. An update was pushed out to affected properties in February. However, because the cards aren’t connected to a network, they can’t be forced to update. Hotel managers would have to call in a technician to update the locks one-by-one, a task that could prove more expensive and time-consuming than buying new ones, “There’s a good chance that not everybody has patched, but we don’t have visibility into that,” Tuominen said.
“This is the new normal. If you have software you need to upgrade it all the time,” Assa Abloy’s hospitality business unit head Christophe Sut told Wired. “We upgrade our phones and computers. We need to upgrade locks as well.”
There are no known reports of hotel break-ins using this method of attack, though that doesn’t mean they haven’t happened. F-Secure says it would take “deep technical knowledge” and a significant investment of time to create a master key.
Assa Abloy did not respond to our request for comment.