Some of Android‘s most popular games have been tainted by a virus installed in fake versions of the games that lets hackers take control of victims’ phones and add them to a botnet, according to new research from the Slovakian security firm ESET.
Infected games posing as Candy Crush, Temple Run, and Plants vs. Zombies 2 are among those on the Google Play Store that were affected by the Mapin virus from the end of 2013 until the end of 2014. The fake version of Plants vs. Zombies 2 alone was downloaded tens of thousands of times over the course of a year while it was infected, after which it was finally pulled from the store.
The fact that Mapin made it onto Google’s official app store means that it fooled Google’s security software, Bouncer, for nearly a year and a half.
This news comes just days after it was revealed that Apple‘s App Store suffered its largest ever attack, affecting hundreds of iOS apps with millions of users.
Mapin also hit third-party Android software markets, affecting more than a dozen apps there in the last two years. Many of these apps are still available outside of the official Google Play Store.
Nearly 75 percent of infections have hit India, according to the researchers.
The Mapin trojan takes a patient and clever attack route by waiting a full 24 hours before executing, so that the infected games don’t seem responsible for problematic behavior.
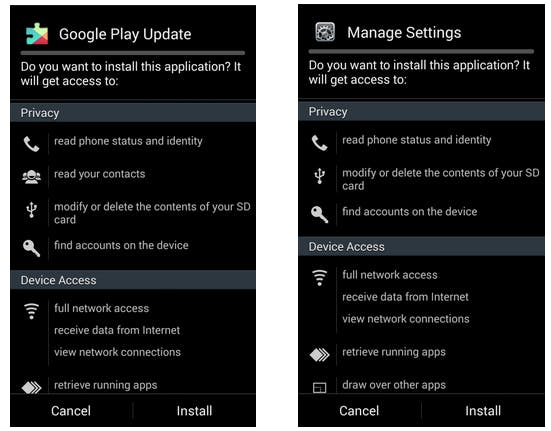
Instead, the user is led to believe that the phone itself asking to install new software called Google Play Update or Manage Settings—authoritative names for nefarious tools.
“The average user will be convinced that this is some important update and at some point is likely to install it just to get rid of this notification,” the researchers told the Daily Dot.
After successfully installing itself, the trojan demands administrative privileges from the user so that it can’t be removed. By then, Mapin has connected back to a command-and-control server through which the hackers can pull the strings.
To add insult to injury, the trojan serves advertisements to the user, interrupting every action with full-screen commercials.
To help protect yourself against threats like this, ESET researchers recommend sticking to trustworthy developers and reading app permission requests closely when installing new software. If a request stands out as unjustifiable, something might be wrong.
Clarification: The apps being attacked by the Android/Mapin Trojan are not the actual popular arcade games, but rather fake versions of those apps that are also available in Google Play as well as third-party stores.
Screengrab via Palo Alto Networks/Google Play