Look closely before you download an attachment someone sends you on Gmail—even if it’s someone you know.
Security experts discovered a clever phishing scheme that fools users into clicking a fake image of an attachment that opens into a fake Gmail login page. Perhaps thinking Gmail logged them off by accident, users then re-enter their username and passwords—only for them to be quickly scooped up by hackers.
As security firm WordFence explains, the fake attachments phishing scheme gained popularity among hackers in 2016, and in the past few weeks, it has fooled even “experienced technical users.” What makes it such an effective con?
As Tom Scott of the “Things You Might Know” YouTube channel noted on Twitter, the fake image is pretty realistic looking:
https://twitter.com/tomscott/status/812265182646927361
Second, the infected email could even come from someone you know and contain an attachment that seems like it could be from them.
Here’s how one commenter from Hacker News described it:
“The attackers log in to your account immediately once they get the credentials, and they use one of your actual attachments, along with one of your actual subject lines, and send it to people in your contact list.
“For example, they went into one student’s account, pulled an attachment with an athletic team practice schedule, generated the screenshot, and then paired that with a subject line that was tangentially related, and emailed it to the other members of the athletic team.”
The commenter added that the hackers used a bit.ly URL to hide the fake link’s address, a method identical to the one experts say Russian hackers used in hacks against the Democratic National Committee and Hillary Clinton campaign chairman John Podesta.
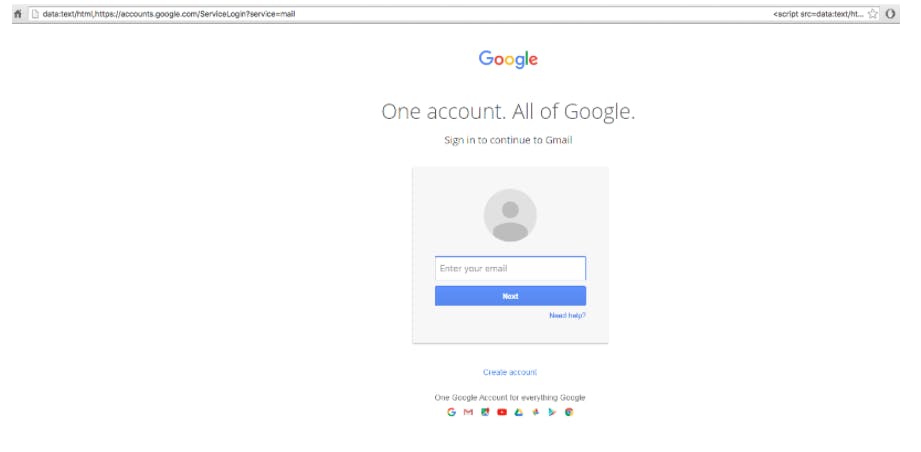
Also, the fake log-in page is a perfect clone of Gmail’s—even down to the user interface—as noted on Github.
Google says it is working on solutions to help better protect its users from this particular attack while stressing that it has other protections already in place.
“We’re aware of this issue and continue to strengthen our defenses against it,” a Google spokesperson told the Daily Dot in an email. “We help protect users from phishing attacks in a variety of ways, including: machine learning-based detection of phishing messages, Safe Browsing warnings that notify users of dangerous links in emails and browsers, preventing suspicious account sign-ins, and more. Users can also activate two-step verification for additional account protection.”
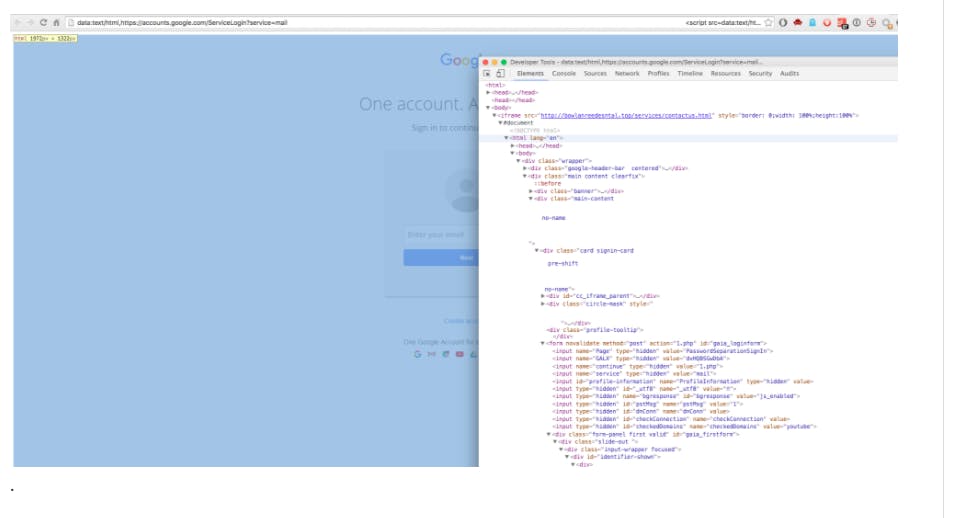
So how do you prevent becoming a victim of this nefarious phishing scheme? According to WordFence, the answer lies in the address bar.
In the phony Google login page, instead of “https” you have ‘data:text/html,’ followed by ‘https://accounts.google.com….’.
To avoid being scammed, always, always, always check the URL and host name of a site before you enter in your credentials.
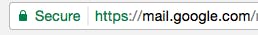
Look for the magic green key:
Writes WordFence:
“You should also take special note of the green color and lock symbol that appears on the left. If you can’t verify the protocol and verify the hostname, stop and consider what you just clicked on to get to that sign-in page.”
Also, don’t make the same mistake John Podesta did! Enable two-factor authentication—if you haven’t already—stat.
Update 4:44pm CT, Jan. 18: Added comment from Google.