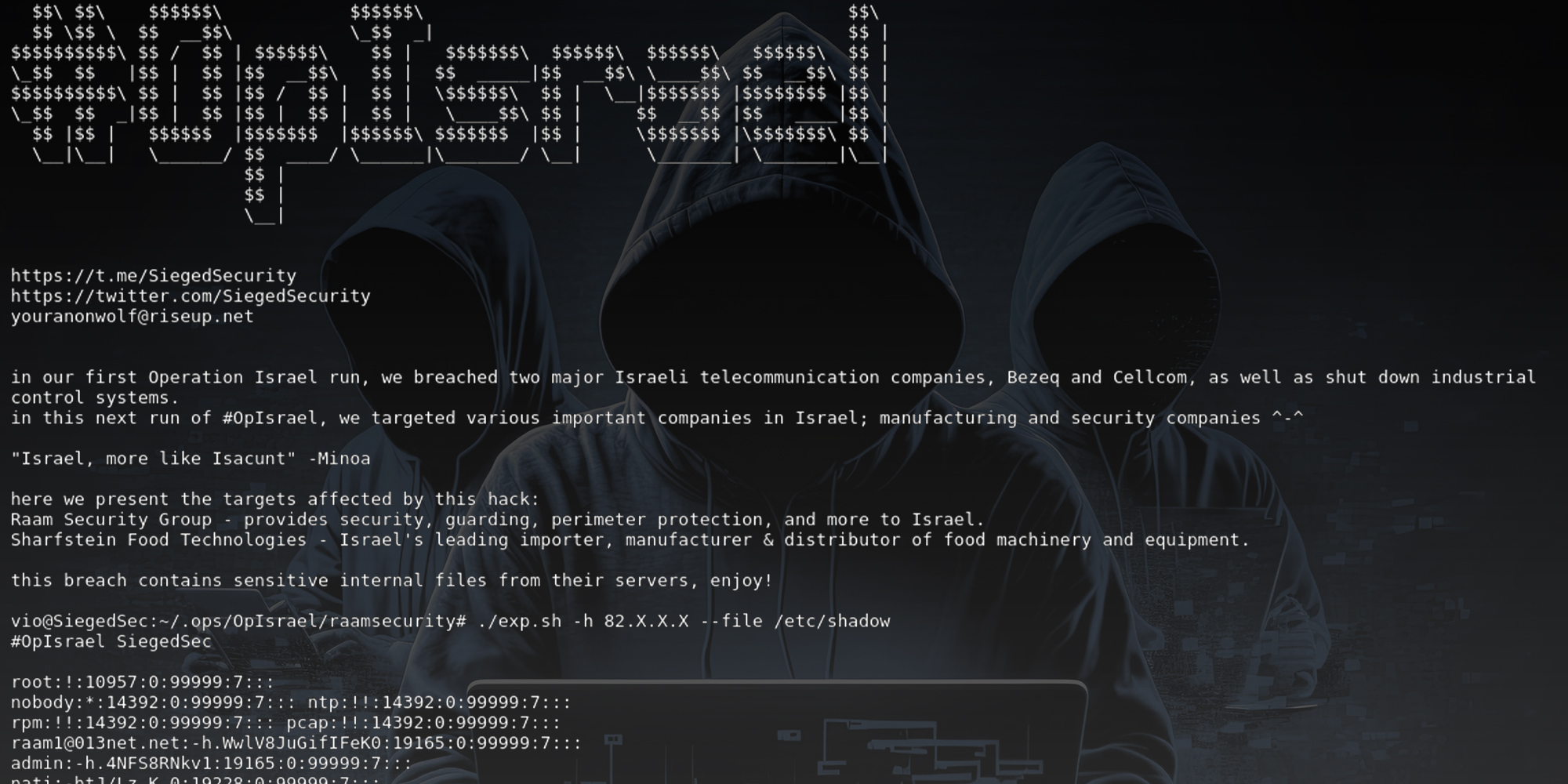
The "gay furry hackers" from the group SiegedSec announced on Sunday the breach of two Israeli companies in retaliation for the country's war in Gaza.
The hacks, part of the group's ongoing campaign known as "Operation Israel," are SiegedSec's second action against the nation following last year's breach of two prominent telecommunications companies.
"In our first Operation Israel run, we breached two major Israeli telecommunication companies, Bezeq and Cellcom, as well as shut down industrial control systems," the group said in an announcement to its Telegram channel on Sunday. "In this next run of #OpIsrael, we targeted various companies in Israel; manufacturing and security companies."
The two breached companies are Raam Security, which provides armed guards and security in Israel, and Sharfstein Food Technologies, the country's top manufacturer of food machinery and equipment.
SiegedSec states that the breach allowed them to access "sensitive internal files from their servers."
Examination of the data by the Daily Dot revealed, among other things, hashed passwords for administrator accounts on both company servers. If cracked, the passwords could be used to take over each website.
While small, SiegedSec said the leak would be followed by "more Israel attacks" in the near future.
"This is only the tip of the iceberg of what we're working on," the hackers added.
The Daily Dot reached out to both Raam Security and Sharfstein Food Technologies but did not receive a response by press time.
Operation Israel was launched by SiegedSec in response to the conflict in Palestine, which has led to the deaths of an estimated 37,000 people. Israel's bombardment of Palestine came after the militant group Hamas attacked the south of the country, killing nearly 1,200 people.
In between its two actions against Israel, SiegedSec has kept busy releasing data from a host of other targets. In April, the group targeted a far-right news outlet that hosts podcasts for prominent figures such as conservative influencer Charlie Kirk. The group has also carried out numerous hacks in defense of transgender rights.
In a statement to the Daily Dot, the SiegedSec member known as vio described the hack as "very easy" and cited a recent firewall exploit as the means of entry. The hacker also alluded to future targets related to OpIsrael.
"We have more attacks planned on embassies within Israel and companies related to Israel's power, construction and other important fields," vio added.
This post has been updated with comment from SiegedSec.
The internet is chaotic—but we’ll break it down for you in one daily email. Sign up for the Daily Dot’s web_crawlr newsletter here to get the best (and worst) of the internet straight into your inbox.