When NSA leaker Edward Snowden spoke to the crowd at this year’s South by Southwest Interactive conference in Austin, Texas, his message was clear: encrypt all the things. Snowden’s argument was basically that the best way to stop widespread government surveillance of online activity isn’t to put political pressure on the governments themselves. Instead, he said, computer scientists must come up with more secure methods of encryption that aim to make it virtually impossible for even the most advanced code-breaking computers to operate on a near-ubiquitous scale.
Better encryption also has the added benefit of making it slightly less likely that hackers will be able to steal your identity.
In an effort to create fool-proof encryption, a team of researchers at Lancaster University looked inward, literally. In a paper published in the American Physical Society’s journal Physical Review X entitled ?Encoding Data Using Dynamic System Coupling,” the scientists incorporated recent discoveries about how different organs in the human body communicate with each other. In particular, they looked at the way in which the lungs and heart are able to perfectly time their interactions so they function as a single unit while operating independently. In doing so, they seem to have found a “nearly unbreakable” encryption method.
“This promises an encryption scheme that is so nearly unbreakable that it will be equally unwelcome to Internet criminals and official eavesdroppers,” said Professor Peter McClintock, one of the paper’s authors, in a statement.
At its heart, all of cryptography is aimed at solving a singular problem: How do you get a piece of information from point A to point B such that an outside observer could intercept that information but not be able to understand a word of it? This issue is actually slightly trickier than it initially seems because, since the aforementioned observer is theoretically able to see everything transmitted between the two parties, agreeing beforehand on a simple cipher won’t suffice. The details of that cipher could also have to be transmitted on a line that is already compromised.
Computer scientists solved the problem through a complex system of public and private keys used to scramble and then decode messages intended to be secure. The system works as long as hackers—be they government snoops or tech-savvy ne’er do wells hoping to go on a shopping spree with your credit card—aren’t able to guess the random string of characters that comprise a private key.
While there’s been a push to make encryption stronger by increasing key lengths, the effort is essentially an arms race between the computer scientists who develop new encryption methods and the computer scientists dedicated to beating them. Documents leaked by Snowden, a former contractor with the NSA, revealed that the agency is currently able to break most of the encryption currently in wide use and is working on developing a quantum computer that could provide them access to the few remaining forms of encryption they’re still unable to beat.
At the end of the day, the length of the keys on most currently available encryption formats are finite—meaning that, given enough time and computing power, they can eventually be cracked.
The team at Lancaster University’s goal was to add another level of complexity into the mix, making the private keys even more difficult to break by creating a system that can generate an infinite number of possible keys. Their system uses mathematical models initially developed to determine the time variations of what’s called ?coupling functions” between a pair of independent systems—in this case, the heart and lungs.
Using this system, a sender composes his or her message, which is then split up into two different systems using a coupling function. The output of each system is then independently sent to the recipient, who uses the same coupling function to put them back together by ensuring that the two systems are interacting with each other at the exact time time intervals as the ones that originally sent the message.
Yes, it’s extremely complicated. This diagram from the paper provides a helpful visual:
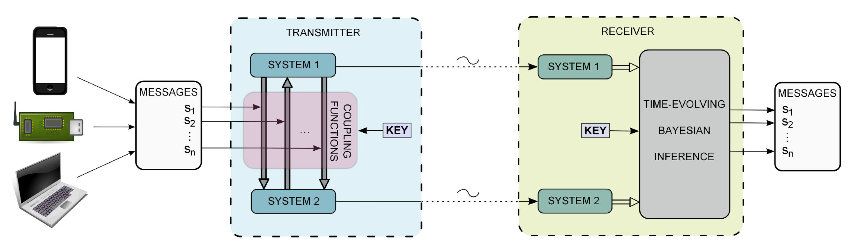
The paper’s authors, who have filed a patent application for their technology, insist that this encryption method is particularly resistant to the random interference (called ?noise”) that affects all communications systems. Since it can transmit multiple data streams at once, the system can send encrypted information simultaneously to multiple receivers without the need to create multiple keys. It is also easily portable between different platforms.
This system isn’t the first time that computer scientists have looked to the natural world for inspiration. Algorithms to aid in ?machine learning” have long been based on research into the functions of the human brain, and models of how computer viruses evolve over time are often inspired by examinations of their biological namesakes.
Professor Aneta Stefanovska, one of paper’s authors, explains, “As so often happens with important breakthroughs, this discovery was made right on the boundary between two different subjects—because we were applying physics to biology.”
Illustration by HBKerr/deviantART (CC BY-ND 3.0)


