As though your drone nightmares weren’t vivid enough, a newly manipulated security hole might leave an array of consumer drones open to hijacking. That may not explain the drone that buzzed the White House, but it’s yet another unsettling layer on top of the seven-layer dip of scary that is the growing realm of consumer-level unmanned aerial vehicles.
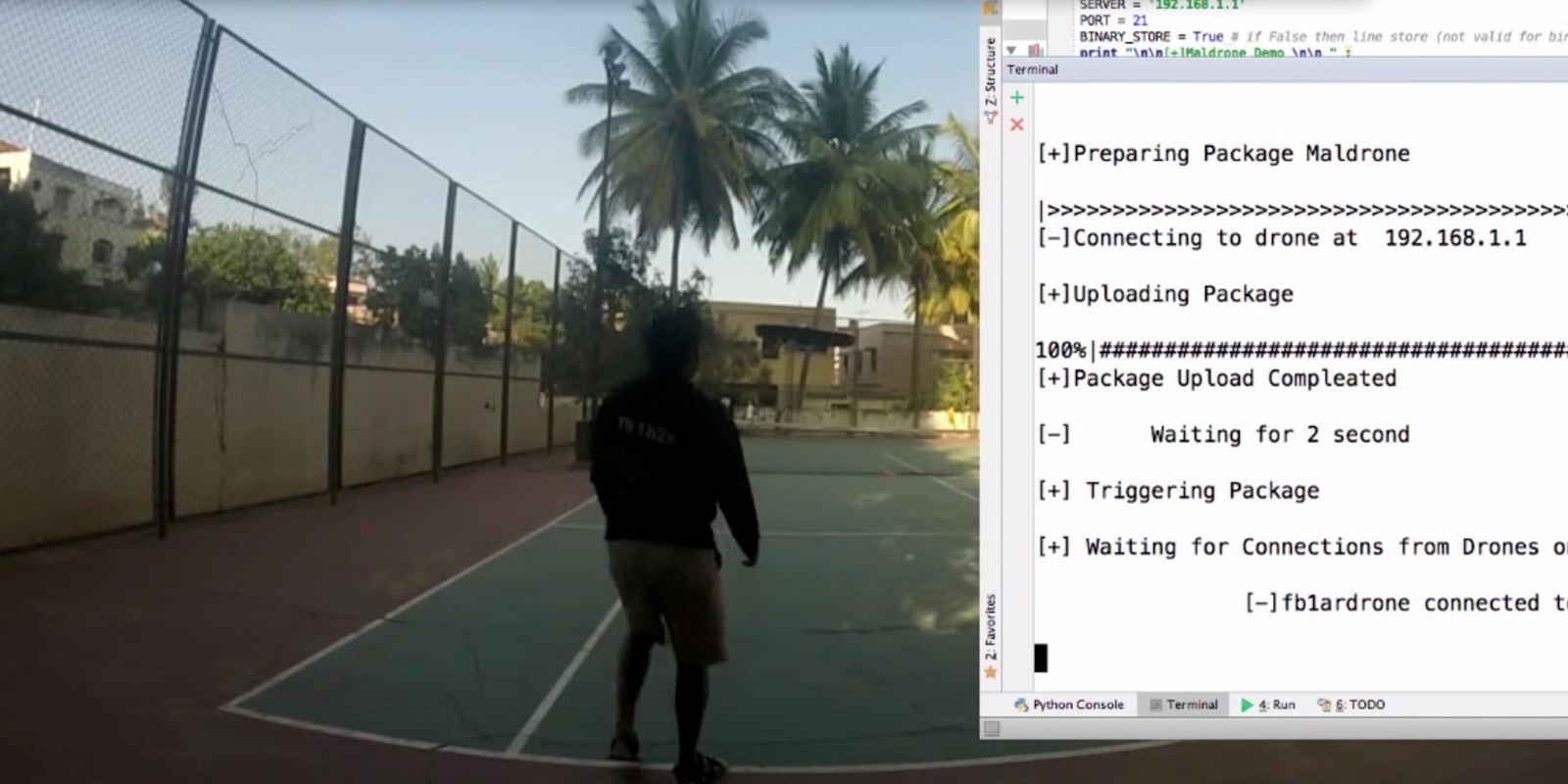
According to a blog post linked on the Hacker News (no, not that Hacker News), a nasty but fascinating little software experiment called Maldrone makes it possible to sneak into a drone’s computing brain via a backdoor style intrusion and take over. The drone can then be disabled instantly—in which case it will literally fall out of the sky—or be steered away from the drone owner, escaping to the “bot master” who has taken control. You can see how it all would go down in the video below.
The example drone used to demonstrate Maldrone is a Parrot AR Drone 2.0. For context, Parrot was one of the earliest commercial companies to move into the drone space. Its range of affordable, commercially available drones are some of the most popular around. Parrot’s drones appear to be open to an an existing exploit called Skyjack, which pops open the backdoor for Maldrone’s malicious software payload.
According to Rahul Sasi, Maldrone’s creator who “hacks things that are not hacked,” Maldrone brings up some serious questions, which he poses on his site Garage4Hackers:
“There are over 70 nations building remotely controllable drones. Most of these drones are capable of making autonomous decisions. Countries buy drones from [their] neighbors. What are the possibilities that there could be a backdoor in the drone you brought. What would be the impact if a security issues is found in a computer devices that make decisions of [their] own.”
We emailed with Dr. Mike Lloyd, the CTO of network security analytics firm RedSeal about the implications of this whole drone hijacking situation.
“With all the talk about the Internet of Things, it’s important to remember that essentially all things can be hacked—the recent announcement of a backdoor attack on a type of personal drone is just one more example,” Lloyd said.
“Drones communicate, clearly—the whole point is they fly away from you, and you need to keep talking to them. As a result, they are vulnerable.”
Keeping devices like personal drones safe from malware like Maldrone might just be a matter of dotting I’s and crossing T’s while writing tight, secure code. Althought keeping a human around doesn’t hurt.
“Automation is like a chess computer—it’s far better at exhaustive detail-checking than any human would be. But we don’t ask the machines to run the machines—nobody wants to build Skynet!” Lloyd said.
“The ideal in security is to combine human talent, intuition, and high-level thinking with machine automation. The human doesn’t come out of the loop. Think about physical security—we don’t use automated machine guns to guard our buildings, we keep a human involved.”
It might be common sense, but keeping an eye on your code is ultimately the best insurance against drone-jacking. And keeping an eye on where your drone goes cruising off to won’t hurt either.
Screengrab via Rahul Sasi/YouTube