Cyberattacks grew more sophisticated in 2015 as hackers built better tools and reached targets with savvier techniques, according to a new report from the European Union’s information-security agency.
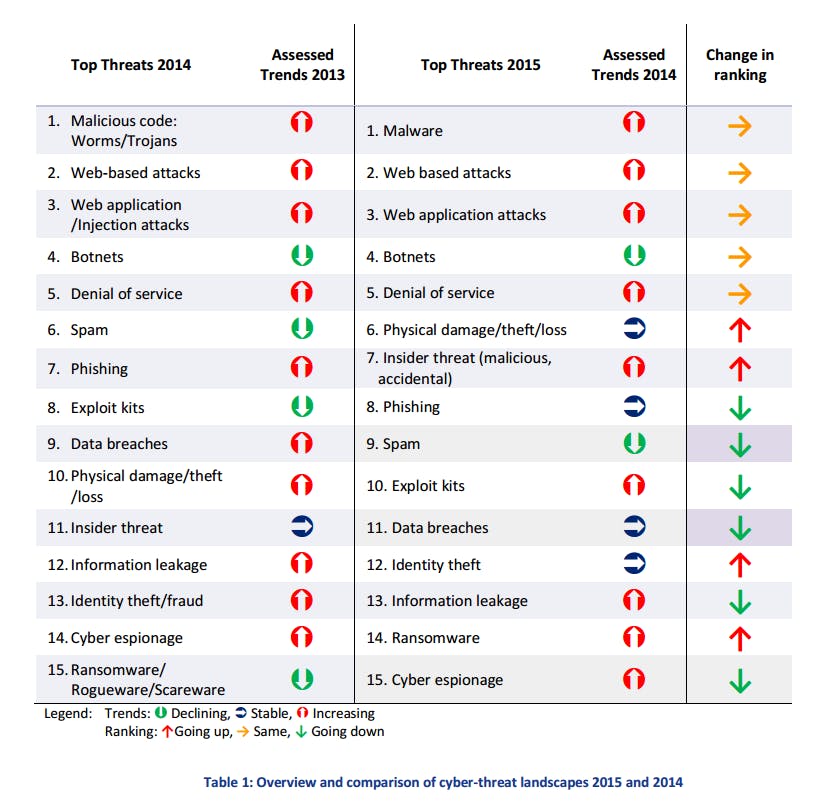
Malware, cyber espionage, and distributed denial-of-service (DDoS) attacks—which involve flooding a website with bogus traffic to overwhelm its servers—all increased in prevalence last year, while attackers moved away from botnets—networks of computers remotely commandeered to conduct attacks—and email spam.
Hackers also stepped up their use of exploit kits, pieces of software that exploit unpatched holes in commercial technology.
Rogue actors are also increasingly “performing persistent attacks based on hardware, far below the ‘radar’ of available defence tools and methods,” the report said. Attacks that are hard to detect are commensurately hard to mitigate, which has led to unique concerns about these below-the-radar attacks.
The massive report from the European Union Agency for Network and Information Security (ENISA) also identified an interesting shift in the secret delivery of infected software. Whereas hackers used to sneak malware onto computers by infecting email attachments, they now prefer to infect webpages and get people to click those URLs.
The report attributed this shift to a new focus on social engineering, the process of posing as a trusted party to convince someone to do something they otherwise might hesitate to do.
“Sending malicious objects via e-mail attachments has declined in recent years,” the report’s authors wrote. “Instead, social (Facebook) scams, downloaders, redirects and phishing are gaining in importance.”
The report also offered fresh ammunition to opponents of mandatory backdoors in encryption, which experts warn would weaken encrypted systems and make their users easier prey for hackers.
“A manipulation or vulnerability included in a delivered [electronic] component by a supplier can be used as backdoor to numerous prospective (malicious) uses within industrial systems,” the report warned.
Elsewhere, the report cited a news article about the unintended consequences of secret National Security Agency backdoors in commercial technology, echoing one of backdoor opponents’ key arguments against their installation.
Hackers have achieved continued success through a combination of simple and sophisticated tactics, the report found. They have used the low-tech approach of social engineering to deliver high-tech, increasingly complex malware. This approach offers twin advantages: It avoids basic security sweeps by using a low-tech delivery method, then escapes detection by relying on code that security software has not yet encountered.
Current trends are not looking good for Internet security. Experts say that companies “have made only modest gains” in fighting hackers in the past two years, while a security firm said on Monday that 27 percent of all known malware was created in 2015.
To improve detection and mitigation of cyber threats, the ENISA report’s authors urged governments to “foster voluntary reporting [of cyber threat data] and perform analysis of reported incidents and recycle results for better planning of defenses.”
Congress recently passed, and the Department of Homeland Security is in the process of implementing, a law meant to ease the sharing of such data between the public and private sectors.
Illustration by Jason Reed