China possesses a weapon of mass disruption and is using it to attack sites that help users defeat online censorship, according to a cadre of academic researchers.
Services that allow China’s Internet users to view websites blocked by the Great Firewall of China—a powerful censorship tool that blocks certain websites outlawed by the government—have been under fire by what researchers have termed the “Great Cannon.”
The tool was recently used to take down GitHub, a popular site among programmers, and GreatFire.org, a site devoted to monitoring Chinese censorship. Code hosted by GitHub is used by GreatFire—along with a Chinese version of the New York Times—to allow Chinese users to circumvent the GFW.
We’ve been under continuous DDoS attack for 24+ hours. The attack is evolving, and we’re all hands on deck mitigating.
— GitHub Status (@githubstatus) March 27, 2015
On March 27, Github posted on its official blog:
We are currently experiencing the largest DDoS (distributed denial of service) attack in github.com’s history. The attack began around 2AM UTC on Thursday, March 26, and involves a wide combination of attack vectors. These include every vector we’ve seen in previous attacks as well as some sophisticated new techniques that use the web browsers of unsuspecting, uninvolved people to flood github.com with high levels of traffic. Based on reports we’ve received, we believe the intent of this attack is to convince us to remove a specific class of content.
The ongoing DDoS attack has changed tactics. We are experiencing intermittent service outages and working to mitigate.
— GitHub Status (@githubstatus) March 29, 2015
After 113 hours of sustained DDoS attacks our defenses are holding. We will keep our status at yellow until the threat has subsided.
— GitHub Status (@githubstatus) March 30, 2015
Hour 118: Mitigation remains effective and service is stable.
— GitHub Status (@githubstatus) March 31, 2015
Everything operating normally.
— GitHub Status (@githubstatus) March 31, 2015
GitHub managed to eventually mitigate the flood of traffic and was operating normally at press time, despite the continued attacks.
Initial reports indicated that China was manipulating the GFW to launch distributed denial-of-service attacks against the targeted sites. Netresec, an independent software vendor, concluded on March 31 that GitHub was hit with a “man-on-the-side” DDoS attack, which infected users with a malicious JavaScript, forcing their browsers to continuously reload two pages on GitHub.com.
“We believe the intent of this attack is to convince us to remove a specific class of content.”
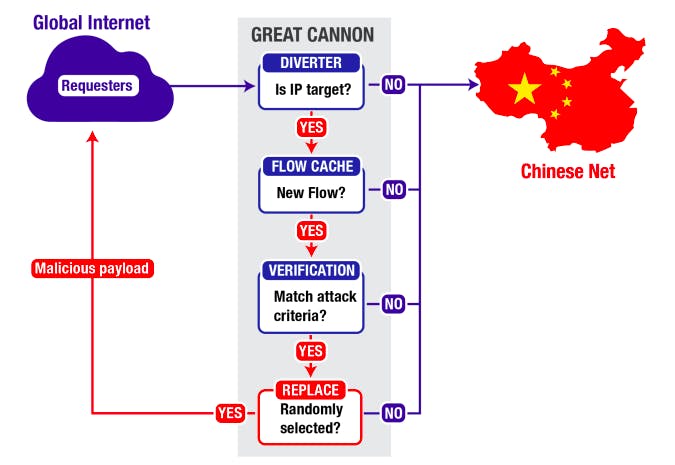
However, researchers at the University of California, Berkeley, and University of Toronto-based Citizen Lab, say the GFW is not the source of the attack. Instead, the so-called “Great Cannon,” a new weapon for censorship in China’s arsenal, is responsible for injecting malicious code into the browsers of unsuspecting users, essentially hijacking their computers, and creating an influx of traffic to overwhelm China’s targets.
“The operational deployment of the Great Cannon represents a significant escalation in state-level information control: the normalization of widespread use of an attack tool to enforce censorship by weaponizing users,” writes Citizen Lab. “Specifically, the Cannon manipulates the traffic of ‘bystander’ systems outside China, silently programming their browsers to create a massive DDoS attack.”
The Great Cannon, according to Citizen Lab, is comparable to a system developed by the National Security Agency code named QUANTUM, which provides for a wide range of injection-based attacks. According to documents produced by Edward Snowden, the NSA weapon was reportedly used by the British government for the exploitation of Belgacom, a state-owned Belgian telecom company.
According to a report by GreatFire.org, the Great Cannon was used to intercept Web traffic intended for the Chinese search engine Baidu. Netresec reported last month that only about 1 percent of requests to Baidu received the malicious injection in return. “So in 99 percent of the cases everything behaves just like normal,” researches said.
Baidu has reportedly denied any involvement and said it would work to prevent future attacks, adding: “Service interruptions could reduce our revenues and profits and damage our brand if our systems are perceived to be unreliable.”
“The attack launched by the Great Cannon appears relatively obvious and coarse: a denial-of-service attack on services objectionable to the Chinese government,” Citizen Lab concluded. “ Yet the attack itself indicates a far more significant capability: an ability to ‘exploit by IP address’. This possibility, not yet observed but a feature of its architecture, represents a potent cyberattack capability.”
Illustration by Max Fleishman