When it comes to the security of our personal information, 2015 may be the worst year on record.
As of Dec. 15, according to a running tally kept by the Identity Theft Resource Center, the past year saw 750 data breaches at American corporations, government agencies, and nonprofits.
While not all of these breaches represented a definite case of nefarious activity, that number is an all-time high. Over 177 million individual personal records were exposed in one way or another. The ITRC only collects records for the United States, which has a population of around 319 million.
“Thieves know how to turn data into money, firms don’t.”
To top it off, these figures only include data breaches that organizations recognized and, in some manner, made public. They don’t account for all the sketchy, malware-filled attachments people opened in the privacy of their own homes.
Stop and think about that for a moment.
Some of these breaches you’ve likely heard about. When hackers publicly released the information of millions users of the adultery-themed dating site Ashley Madison, it made international news. However, it probably slipped under your radar when hackers compromised the data of customers who shopped at online at the American arm of the trendy, minimalist housewares company Muji. And you likely didn’t notice when the servers of the textile manufacturer Knit-Rite were infected with a virus designed to capture the personal and credit card information of an unknown number of users.
Of course, the main thing that makes data breaches matter is the data itself. As such, these data breaches, while often dangerous and damaging to Americans’ identities and finances, have sparked a surprising long-term effect— they will ultimately protect your privacy.
Inside the cybersecurity industry—that is to say, the people who periodically wake up in a cold sweat worrying about the consequences of the next Ashley Madison-style dataclysm happening on their watch—there’s been a growing realization: The big data revolution promised by the dual innovations of massive computing power and cheap, nearly unlimited storage capacity, has a dark side. Each piece of personal data collected from a user or employee and then stored for safekeeping also has the risk of eventually being stolen.
As Sam Pfeifle, publications director at the privacy organization International Association of Privacy Professionals notes, 2015 saw organizations accepting the conclusion that, in many ways, keeping 100 percent of their information safe 100 percent of the time is a losing battle. Instead, the way to manage the potential liability incurred from a data breach is not to collect the most dangerous pieces of data the first place.
“Privacy is this really hard thing to pin down,” Pfeifle told the Daily Dot. “It’s different culturally, it’s different from person to person. … Some people are exhibitionists, some people don’t care if the NSA is spying on them. But, for everybody, there is some thing that hits home. I think the nature of the breaches this year has started to make it hit home as a real issue for a lot more people.”
Not all personal information is created equal. When brick-and-mortar retailers Target and Home Depot were hacked last year, the attacks were major events that cost the companies both cash and reputation. Yet, for most customers affected by those breaches, the negative repercussions were minimal.
If an identity thief steals your credit card number, it’s probably not going to be an enormous inconvenience. The credit card company notices a suspicious purchase, sends you a message asking whether or not it was legitimate, and you tell them yes or no. Either way, the financial institution likely won’t require you to pay the cost of any fraudulent purchases because a certain level of losses from fraud are built into their business models.
The big data revolution promised by the the dual innovations of massive computing power and cheap, nearly unlimited storage capacity, has a dark side.
However, when hackers accessed the records of some 21.5 million current and former federal employees and government contractors by infiltrating the computer systems of the the Office of Personnel Management, which essentially functions as the federal government’s HR department, it was another story entirely.
Since OPM handles government background checks, much of the data it held was extremely intimate: names, current and former addresses, Social Security numbers, employment history, fingerprints, and much more.
The OPM hackers are believed to be from China, although Beijing officials have denied the attack was state-sponsored. Nevertheless, the CIA reportedly pulled its agents from the U.S. embassy in the Chinese capital as a precaution.
The OPM hack was a wake up call across the entire tech sector. In the hands of an identity thief, that level of detailed information is essentially a license to print money at someone else’s expense. Armed with the data from the OPM hack, a criminal could do everything from taking out fraudulent loans in the victim’s name to using their identity to obtain free medical care or prescription drugs to filing their tax return and stealing the refund.
“When storage first started to get cheap, everybody was gleeful. They could collect all this information, store it forever, and then figure out how to use it later,” said Pfeifle. “Now, you look at that OPM breach, some of that data was from employees who haven’t worked [for the federal government] in years and years and years. That should be been deleted unless it was absolutely necessary.”
The concept is here is called data minimization—organizations thinking critically about what data they absolutely need to collect and what carries a significant enough risk that having it on their servers may ultimately be more trouble than it’s worth.
“When you’re doing some marketing campaign or a hiring for a job, are you deleting all those resumes after the fact? Are you asking for their occupation for a good reason? You never know what data might start getting really personal and might make you subject to some sort of liability,” Pfeifle said. “This concept of data minimization is starting to become much more commonplace in corporate America. Whereas, it used to be, that big data was always viewed as an asset. Now, you better have a good reason for how you’re going to monetize that data, or else it’s going to bite you in the butt.”
A recent survey of 300 IT security professional commissioned by the cybersecurity firm SecureAuth found that 59 percent said their company had experienced a data breach in the past 12 months, and 62 percent felt that managing the consequences of data breaches is more costly than protecting against them in the first place.
Pfeifle notes this gradual shift from a “gather all the data” mindset to one more agnostic about universal collection is not yet a sea change affecting the entire tech industry. Amassing an enormous amount of data is still, in many ways, the norm. Even so, some industries have taken the concept to heart—the healthcare field, for example
In an interview with the Daily Dot earlier this year, Greg Virgin, the founder of cybersecurity consulting firm RedJack, recalled how he was recently talking with an executive at a small medical technology startup, and said something that made his client turn white. Virgin commented that the firm’s total liability was far greater than the startup’s total value. A significant data breach would, almost certainly, put them out of business immediately. “Compared to financial data, which is usually short-lived, the information in medical records tends to last a lot longer—it’s a lot more sticky,” Virgin said.
Changing your credit card number is a painless process that can be accomplished in a few minutes. Getting a new Social Security number is an epic ordeal, and the U.S. government only grants under a very rare and specific set of circumstances. Your blood type is forever.
All that information can be, in some way, valuable to thieves. On online black markets where stolen personal information is bought and sold, someone’s full medical records can go for as much as $4,700, whereas a stolen credit card number is only worth the equivalent of loose change.
Andy O’Hara, the founder of Austin, Texas-based telemedicine startup Chiron Health, told the Daily Dot earlier this year that his company takes great pains to only collect the bare minimum amount of personal information from its users as necessary in order to minimize the risk associated with holding it.
“Companies are really starting to think about there being a certain set of laws we need to comply with and they have a compliance department for that. But what do they want to do as a company?” said Pfeifle. “What do they believe in terms of privacy and how do they want to integrate that throughout the entire organization?”
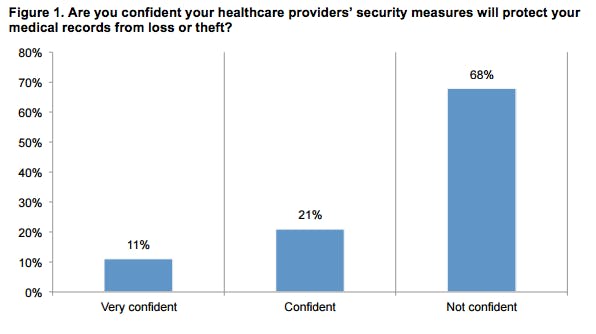
As wave after wave of major hacking scandals break, the level of trust everyday people have in the institutions tasked with holding on to their data drops. A study by the Ponemon Institute found that 68 percent of respondents were not confident their healthcare provider was taking sufficient security measures to keep their medical records safe.
Charles Leonard is co-founder of the cybersecurity Cybernance, which provides tools for corporate leaders to better understand risk posed by their data stores. He argues that, while companies like Facebook and Twitter seem to be more valued for the data they’re able to extract from users more so than for their actual ability to generate revenue, converting that data into profit can often be nebulous. For identity thieves, turning data into dollars is considerably more direct.
“Thieves know how to turn data into money, firms don’t,” Leonard told the Daily Dot. “But firms who collect data will subsidize the cost of damages to their owners and customers.”
Even though companies can buy insurance against data breaches, Leonard added, the damage an organization suffers can be far greater than the costs associated with cleaning up the mess, from a forensic analysis to determine what went wrong to legal fees associated with potential class action litigation.
Your blood type is forever.
“At the peak of their breach disclosure [in February of 2014], Target had lost $2.2 billion in market value. You could think of this as the market’s appraisal of the collateral brand damage outside of the financial liability,” Leonard said. “This was the breach that brought cyber risk into the public imagination, and the watershed moment when people realized this isn’t something you can blame on ‘the IT guy.’”
If Target was collecting more information than just customer names and credit cards, that number would have likely been even bigger. That’s why it isn’t just scrappy startups like Chriron that are attempting to bake privacy into their DNA by keeping certain pieces of user information away from prying eyes—including their own.
“A lot of [big tech] companies are dedicated to privacy [and] I think Apple is the best example here,” Nate Cardozo, a staff attorney at the Electronic Frontier Foundation, told the Daily Dot. Cardozo complies an annual report rating tech firms on their policies toward user data. “Apple is the biggest company that has ever existed in the history of the world, and their CEO, Tim Cook, has made it very clear to his customers and to the U.S. government that the security of their users is his number one priority.”
One of the ways Apple is selling itself as an organization that takes the privacy of its users seriously is though data minimization. In the iOS 9 mobile operating system released earlier this year, Apple boasted that users’ personalized data will be stored locally on their devices rather than in the cloud, where it could become vulnerable through an attack on the company’s servers.
At its core, Cardozo believes, Apple’s fight with the U.S. government over encryption—technology that makes user data unreadable to the company and, notably, police and spies—is largely about data minimization. Apple has set up its messaging systems so not even the company is able to decrypt messages sent from one user to another—even if ordered to by law enforcement or intelligence officials.
“[Cook has] made a stand there, and I absolutely don’t see him backing down on that.,” Cardozo said. “And, where Apple goes, so the industry will have to follow.”
Clarification: The International Association of Privacy Professionals identifies as a privacy organization, not a cybersecurity group.
Illustration via Max Fleishman