Malware hiding in the Google Play Store is infecting banking apps and stealing money from Android users, cybersecurity experts say.
Dubbed “BankBot,” the banking trojan disguises itself as supposedly trustworthy free flashlight or gaming apps, according to a report by Avast, ESET, and SfyLabs. The report claims “thousands of Android users” were infected in the past few months after new versions of the malware snuck their way into the Play Store.
After a user downloads one of these virus-infected apps, it will activate a fake user interface on top of trusted banking apps like WellsFargo, Chase, ING-DiBa, and Citibank. This gives it the ability to steal credentials and transfer funds from users’ accounts.
Google has measures in place to ensure malicious apps don’t get published in the Play Store, but bad actors are using new tricks to circumvent these protections, like waiting a few hours after Google’s checks to download malicious payloads and using multiple developer names.
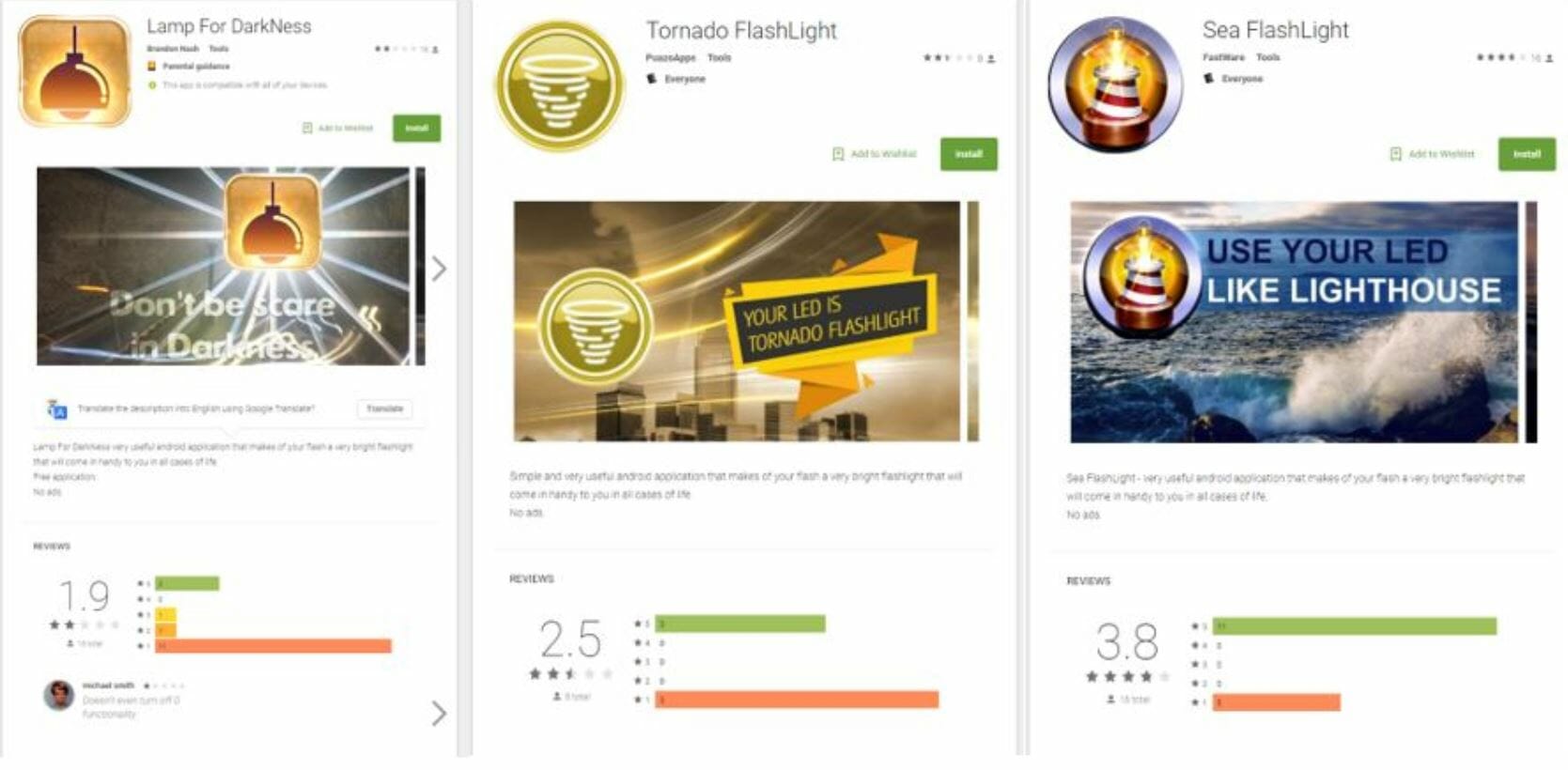
Researchers first found the apps in the Play Store in October. The first three discovered were flashlight apps “Lamp for Darkness,” “Tornado Flashlight,” and “Sea Flashlight.” A second wave of trojans appeared in November as Solitaire and smartphone cleaning apps. Some of the apps had five-star ratings. Once these apps were installed on an Android device, they could go undetected by the user, operating in the background for extended periods.
The banking trojan first determines what apps are downloaded on the device, then, if it finds a match to a known banking app, downloads malicious applications from a web server. The trojan then tricks users into giving them admin rights by displaying a phony Play Store system update. After a two-hour wait to avoid Google’s checks, the trojan drops its malicious payload. Once the setup is complete, the BankBot can display a fake user interface on top of banking apps in a matter of milliseconds, tricking users to use their damaging software instead.
You can see it in action in the video below:
Unfortunately, two-factor authentication won’t protect you from the attack. The banking trojan includes software that can intercept text messages and use your credentials to transfer funds out of your account.
There are several things you can do to protect yourself from this devastating malware. For one, don’t download flashlight apps, especially if they have poor or few user ratings. If you notice anything weird about your banking apps, like if the font or images look off, then back out, uninstall them, and call your bank.
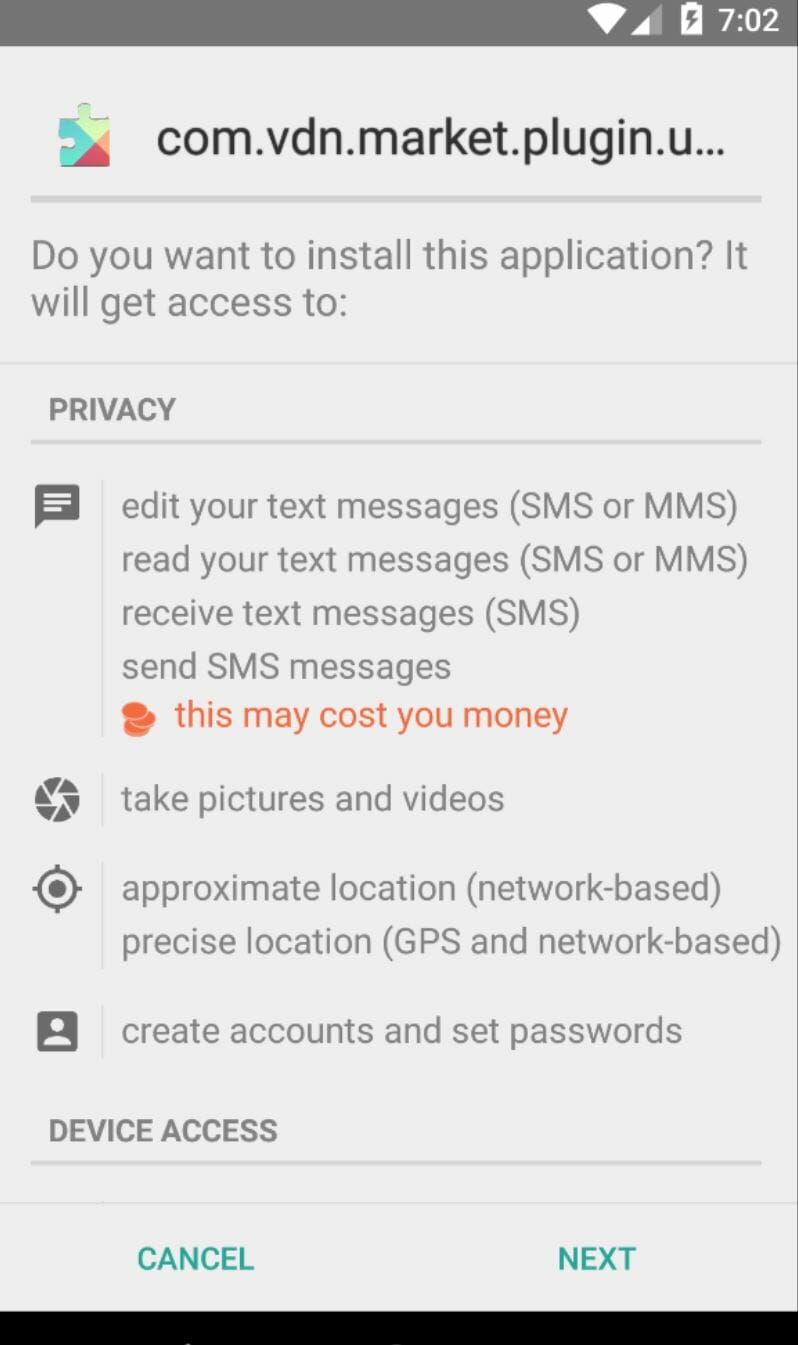
The best thing you can do is deselect the option to download apps from other sources. This is not allowed by default, but if you’d like to double-check, you can find it under “apps” in the “general” settings on your Android device. You should also enable two-factor authentication for your banking apps, which can protect you from other types of attacks. And finally, always look at the permissions an app requests before you download it. If a flashlight app is asking for access to your text messages, consider that a huge red flag.
The virus has, so far, been discovered in the U.S., Australia, Germany, Netherlands, France, Poland, Spain, Portugal, Turkey, Greece, Russia, Dominican Republic, Singapore, and the Philippines.
We have reached out to Google for comment and will update this article if we hear back.


