Apple insisted for years that its Mac computers didn’t get viruses like Windows machines did. Mac users would sometimes claim that their computers were virtually immune to all malware. But as Mac OS X becomes more popular, security researchers are finding new ways to bypass core components of Apple’s security suite.
Patrick Wardle, a security researcher and former employee at NASA and the National Security Agency, has discovered a way to bypass the “Gatekeeper” function that OS X uses to verify the legitimacy of software. He presented his findings Sunday at the ShmooCon security conference in Washington, D.C.
By default, Gatekeeper only allows users to install software from the Mac App Store or programs with Apple-approved signatures. In theory, this protects users from accidentally downloading suspicious malware.
Wardle called Gatekeeper a tool to protect “naive” Mac users. Apple released a patch intended to fix the Gatekeeper flaws he found, but he was still able to bypass security tool. “The reality is Gatekeeper only protects Mac users from very lame attacks,” Wardle said. “Apple has definitely messed up some security patches recently.”
As Wardle discovered, Gatekeeper validates the signature of an application when it is first executed but doesn’t check code that is executed later on from within the application. Malicious code tucked away inside a program could thus slip past Gatekeeper undetected.
Wardle’s biggest fear is that an attack could take advantage of an encrypted connection to a website (HTTPS) and insert malicious code into a program as the victim downloads it onto their computer.
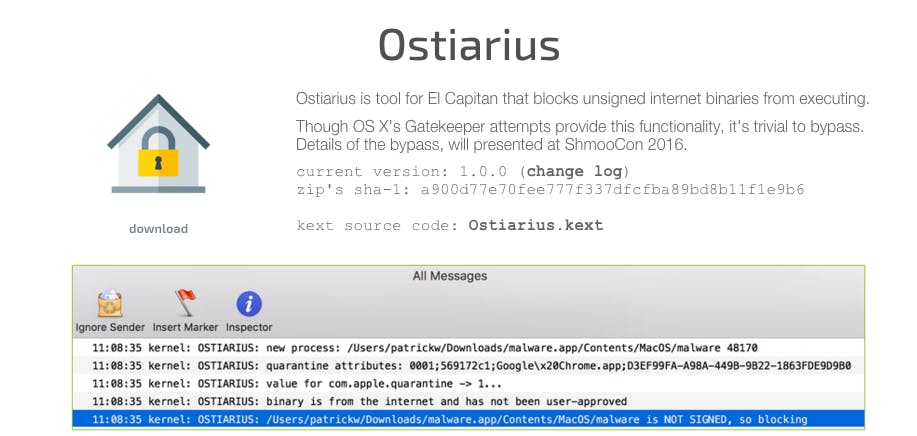
Apple released a patch to fix this issue but only blacklisted the specific apps the Wardle used to exploit Gatekeeper. He has since created an application, called Ostiarius, designed to protect users from his exploit.
Illustration by Tiffany Pai