The hidden websites on the Tor anonymity network are supposed to be concealed behind a strong veil of technology. But as with any technology, human mistakes can undo almost anything.
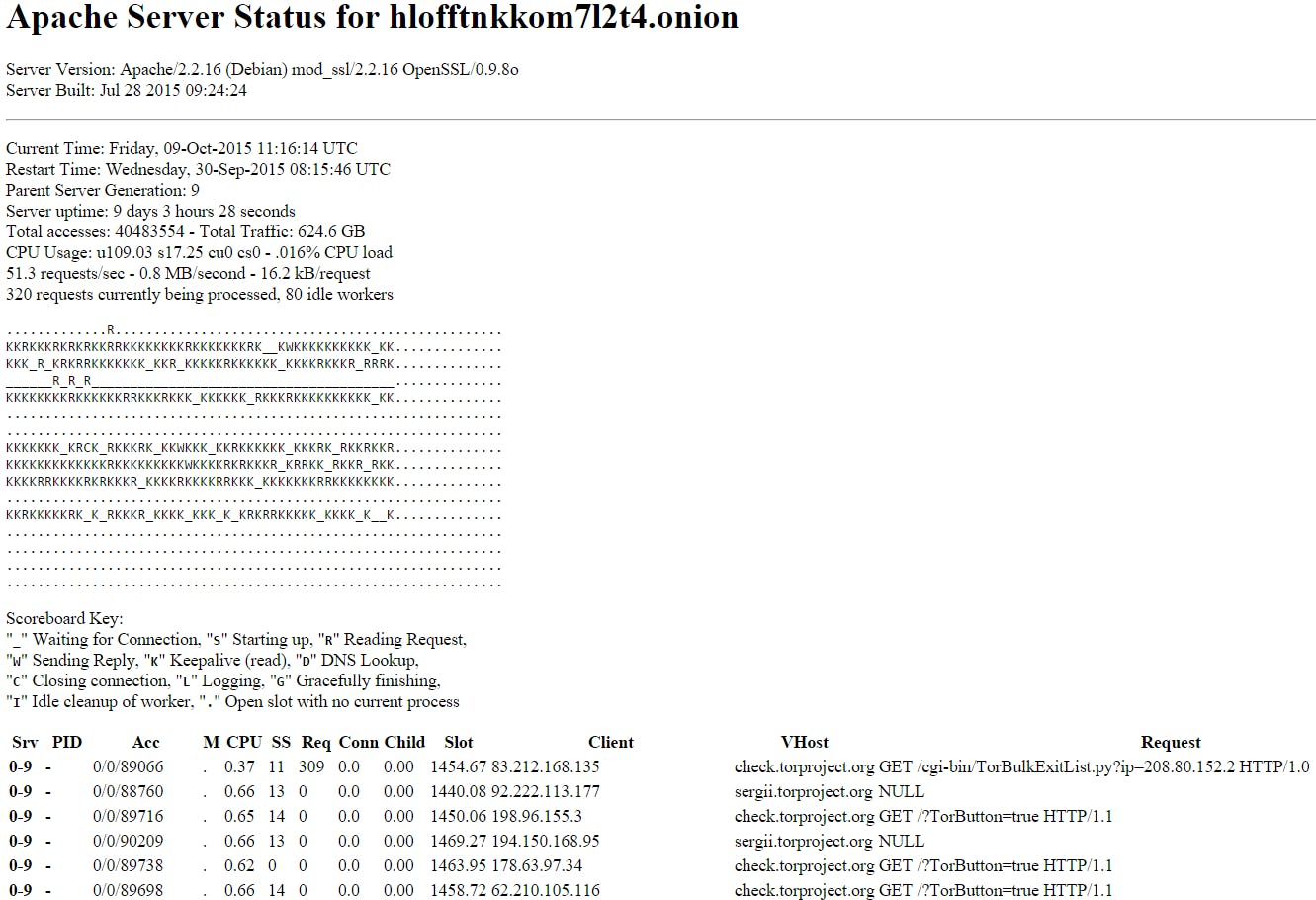
A common configuration mistake in Apache, the most popular Web server software in the world, can allow anyone to look behind the curtains on a hidden server to see everything from total traffic to active HTTP requests.
When an hidden service reveals the HTTP requests, it’s revealing every file—a Web page, picture, movie, .zip, anything at all—that’s fetched by the server.
Tor’s developers were aware of the issue as early as last year but decided against sending out an advisory.
The problem is common enough that even Tor’s own developers have made the exact same mistake. Until October 2015, the machine that welcomed new users to the Tor network and checked if they were running up-to-date software allowed anyone to look at total traffic and watch all the requests.
In the case of this particular Tor Project machine, it doesn’t appear that there’s much danger to the users. Instead, the status page reveals a lot of server information but not much sensitive user data.
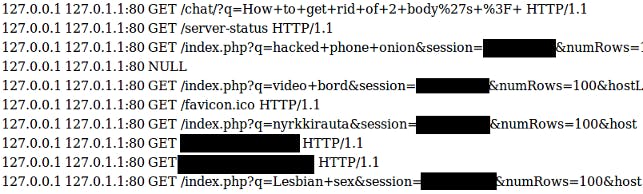
Alec Muffet from Facebook, which runs its own hidden service, said on Saturday that he’s been sounding the alarm on the problem for six months. Last year, he found a popular hidden service search engine with the same problem exposing active HTTP requests, meaning you could watch the searches being made in real time.
Muffet redacted the “most distasteful” results. Even so, the top search asks “How to get rid of 2 bodys.”
When alerted last year to the issue, Tor developers decided against sending out an advisory. In fact, Apache’s configuration problem has been known even longer than that.
To fix the issue on your own Apache-run hidden service, Muffet advises a one-liner from the shell of your server to disable the whole thing:
$ sudo a2dismod status
Photo via Andrew Stawarz/Flickr (CC BY ND 2.0)