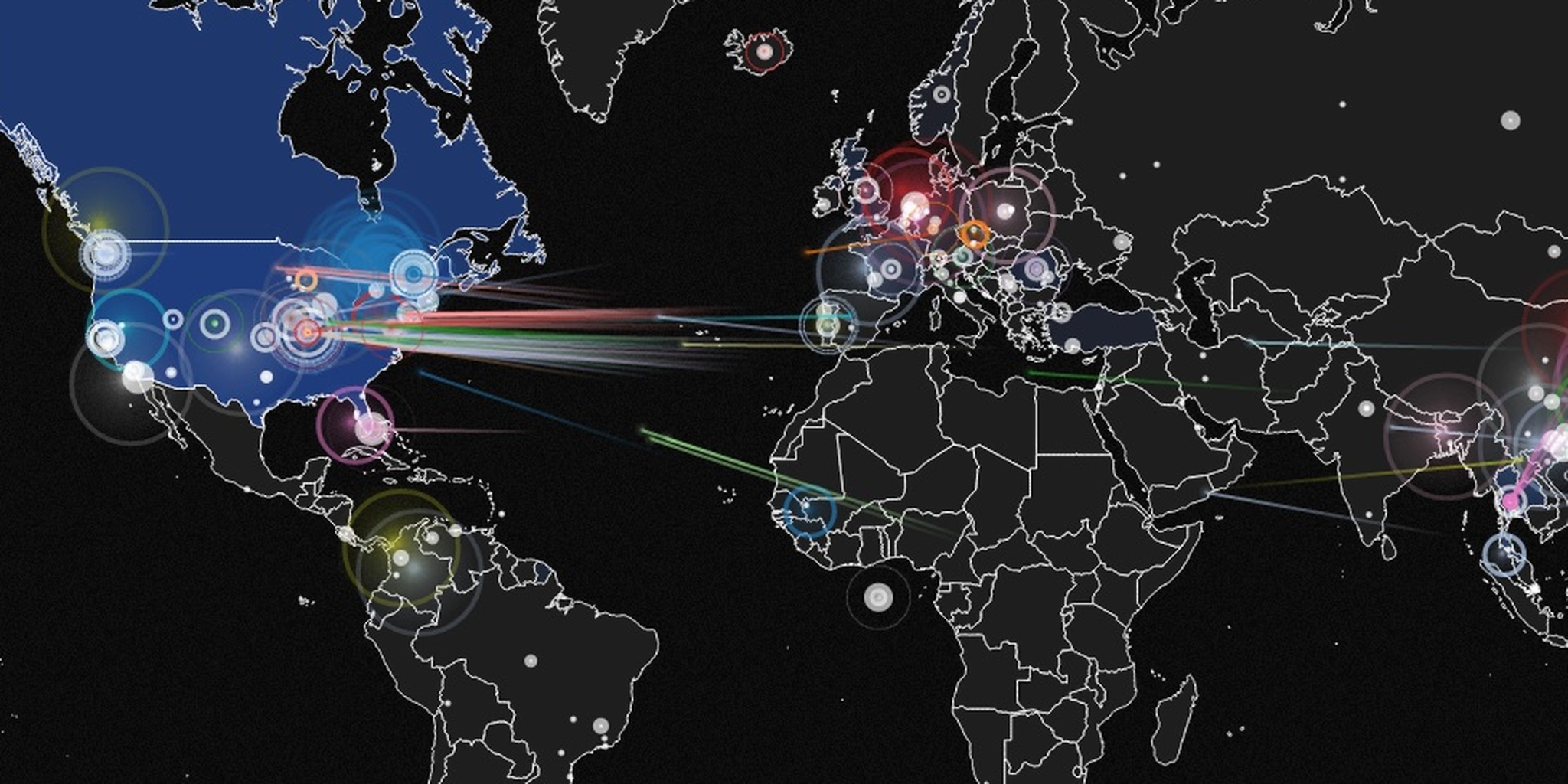
We hear about distributed denial-of-service (DDoS) attacks all the time. Now, thanks to a new map, we can see how often these attacks occur, who's getting targeted, and who's doing the attacks.
The map, called IPViking Live, comes from a company called Norse that specializes in monitoring malicious online activity. The map is not comprehensive; it shows “a small subset” of DDoS attacks aimed at servers that Norse has set up as dummy targets. These “honeypots” collect information about the automated attacks that stream in from countries like China, Thailand, and Russia. Hovering over a location will show you attacks originating from that site.

After leaving the map open in a browser for about ten minutes, we noticed some interesting things about the results. The majority of attacks originate in China, and the vast majority are targeted at the United States—as you might expect. But the U.S. and Canada are nearly as often the originating country of DDoS attacks.
Much of the activity from China can be attributed to organized professional operations, but the attacks coming from North America likely originate from computers that were sucked into botnets. These American and Canadian machines are being controlled remotely, probably from China or Russia, and aimed at other computers in North America in massive DDoS waves.
DDoS attacks essentially flood computer servers with far more traffic than they can handle, effecitvely knocking them offline so other people cannot access the websites or online services they power.
In addition to location, Norse’s IPViking map breaks down the attacks by type. We saw numerous attacks targeting the “db-lsp-disc” protocol, which is used by Dropbox’s LanSync Discovery feature. Other common targets were “microsoft-ds,” a.k.a. Port 445; “ha-cluster,” which refers to high-availability clusters meant to guard against DDos strikes; and “isakmp,” the Internet Security Association and Key Management Protocol.
Screenshot via IPViking Live