Earlier this year, Mt. Gox, once the most prominent Bitcoin exchange on the planet, stopped allowing its users to make withdrawals. A few days later, the exchange shut down completely and its administrators pinned the blame on hackers who had exploited a flaw in Mt. Gox’s implementation of the Bitcoin protocol called transaction malleability to conduct the largest heist in cryptocurrency history.
A study released this week by a pair of researchers in Switzerland took a careful look at Mt. Gox’s claims, and the say claim the now-bankrupt company’s explanation of what happened couldn’t possibly be true. Based on their analysis of the record of Bitcoin transactions dating back nearly a year and a half, it’s only possible to explain the disappearance of 386 bitcoins (about $200,000 at the current exchange rate) through transaction malleability, not the 850,000 lost coins (roughly $440 million) claimed to have been stolen from Mt. Gox.
The study was conducted by Christian Decker, a doctoral student in the Distributed Computing Group at ETH Zurich (the Swiss Federal Institute of Technology), and his supervisor Roger Wattenhofer. The pair had been monitoring and recording transactions occurring over the Bitcoin network since the beginning of 2013 as part of a project looking at how information is disseminated across the network in an effort to determine if there were ways it could be improved.
As a part of this project, Decker and Wattenhofer started collecting information about transactions as they happened, which is precisely what allowed the pair to determine the frequency of transaction malleability attacks across the network. Once a transaction malleability attack has been completed successfully, all evidence that it ever occurred is effectively erased from the blockchain (the name of the public ledger in which all Bitcoin transactions are recorded), making it impossible to do this sort of forensic work by simply looking at the blockchain as it exists today. Instead, anyone investigating transaction malleability needs to have been monitoring every transaction request as it was initially sent through the network and then independently saved that information to their own system.
At the most basic level, transaction malleability allows someone to artificially modify the data associated with a given Bitcoin transaction to make it appear as if the transaction failed to go through even though it actually did. When used against a Bitcoin exchange like Mt. Gox, the technique allowed users to withdraw money from accounts held by the exchange, fraudulently claim that the money was never received, and then have the exchange send them the specified amount a second time. If an exchange’s operators independently verified these transactions against the official blockchain record, they wouldn’t have been fooled. Since Mt. Gox didn’t take this precaution, it was allegedly possible for thieves to do this thousands of times over a multi-year span and clean out all of Mt. Gox’s reserves.
In the process of conducting a transaction malleability attack, the attacker produces a pair of very similar transactions that are both sent through the network at approximately the same time. Only one of the two transactions will ultimately be confirmed by the network and the other will be rejected. Because the other transaction never went through, it was never officially recorded into blockchain. If the one modified by the attacker is accepted, then the attack could be successful if the exchange then re-sends money to the attacker. But, if the unmodified transaction is accepted, the attacker won’t be able to make it seem as if their withdrawal had failed.
Since the study’s authors were collecting information as it was initially sent over the network, they were able to count the number of occurrences of these dual transaction requests and determine the actual frequency of attempted transaction malleability attacks. They found that, since last January, a total of just over 303,000 bitcoins were involved in attempted malleability attacks across the entire Bitcoin network—a number far short of the 850,000 supposedly stolen from Mt. Gox alone.
However, according to Decker, the vast majority of the malleability attacks occurred after Mt. Gox stopped allowing users to withdraw money from the site, meaning that only a small fraction of the total number of attacks could have conceivably been directed against Mt. Gox.
The following chart shows the number of attempted transaction malleability attacks on the Bitcoin network over time. The red line on the left marks the date MtGox stopped processing withdrawals and the red line on the right shows when the exchange’s managers sent out a press release blaming transaction malleability for the missing bitcoins:
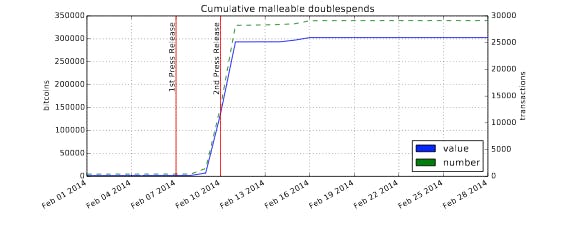
The study’s authors write:
“Assuming MtGox had disabled withdrawals like they stated in the first press release, these attacks can not have been aimed at MtGox. The attacks therefore [were] either attempts to investigate transaction malleability or they were aimed at other businesses attempting to imitate the purveyed attack for personal gain. The sheer amount of bitcoins involved in malleability attacks would suggest that the latter motive was prevalent.”
According to this analysis, only 1,811 bitcoins were involved in attacks prior to Mt. Gox disabling withdrawals. Additionally, since the bitcoin network has a tendency to favor legitimate transactions over modified ones, only 386 of those 1,811 bitcoins could have been in a malleability attack against the formerly Tokyo-based exchange. ?Even if all of these attacks were targeted against MtGox, MtGox needs to explain the whereabouts of 849,600 bitcoins,” the study’s authors charge.
?I prefer not to speculate about the motives behind the press releases [blaming transaction malleability] by MtGox. If transaction malleability was in fact chosen as a scapegoat it is a poorly chosen one,” Decker wrote in an email to the Daily Dot. ?Right from the beginning a majority of users were skeptical and we now provided the proof that it was not the cause. It is true that once a transaction is confirmed all contradicting transactions will be dropped by the clients, however we can still find traces of the attacks in the blockchain as they’d use non-standard encodings of the signatures.”
Decker admitted that the study has yet to undergo peer review, so it may be best to hold off on calling these results conclusive until they’ve been independently verified. However, Decker said he decided to make his findings public at this early stage because people might find this information useful well before the peer review process, which can take months, slowly grinds to completion.
On online cryptocurrency forums like the influential Bitcointalk bulletin board, the study’s results have been received with a muted credulity, largely due to a widespread distrust of Mt. Gox’s leadership—particularly CEO Mark Karpeles, who many believe has been less than truthful in his description of what happened to prior to Mt. Gox’s demise.
Even so, some users did express a few reservations:
There’s already been some indication that transaction malleability wasn’t the root cause of all of the missing coins. Last week, Mt. Gox announced it had discovered an old wallet from 2011 that was previously believed to be empty but actually contained nearly 200,000 coins—about a quarter for the money supposedly lost for good.
Mt. Gox representatives have confirmed that they are working with law enforcement officials in an effort to locate the stolen coins.
Photo by Zach Copley/Wikimedia Commons



