The accident happened right after Christmas. On a rainy, cold Texas morning in late December of last year, a driver going westbound on Interstate 20 drifted to the eastbound side of the road and hit the oncoming Nissan Rogue head on.
Michael and Beth Hamelin were inside the eastbound car. Both automobiles were destroyed.
Michael was a hacker and physicist. His career spanned two decades; he worked on CERN’s Large Hadron Collider and handled infrastructure security at IBM. Beth is a scientist with the Center for Disease Control.
The man driving the westbound car survived. Michael, who was driving, had no pulse. Beth, riding in the passenger seat, was awake, injured but alive after the devastating accident.
Laid out in a Fort Worth hospital bed, Beth soon found herself lost, trying to navigate the immensity of her husband’s death. She also found herself attempting to find her way through another maze, one she had not thought to consider: Michael’s digital afterlife.
Death—your death—means questions. What do you want done with your property? How do you want to be buried? What happens to your money?
These days, the questions inevitably turn to our digital selves: the laptops, phones, and social media profiles we rely on so heavily in the connected age. For a hacker like Michael, the complications here are even greater. Can your family access your computers to retrieve important files? Who needs to know your passwords? Can they get past the full disk encryption you enabled for protection from bad guys?
These are the questions that now burden Beth, whose tale serves as an important reminder to all of us.
Recovering from her broken bones and bruises in the hospital, one of the first questions Beth asked was simpler: How do I call anyone and tell them that Michael has died? The first responders who took Beth out of the crushed car didn’t grab her phone or purse, so she was alone in a hospital where she knew no one and no one knew her.
“We don’t remember phone numbers anymore. We are dependent on technology,” Andrew Kalat, a close family friend of the Hamelins who has received Beth’s blessing to reveal her story to the world, told the Daily Dot. No phone means no numbers. No numbers means no contact.
When the accident happened, the Hamelins were on their way to meet a friend named Gil Brice. It didn’t take long for Brice to notice that the couple was hours late and not answering any calls.
Brice and Michael, both iPhone users, shared their phone locations with one another through Apple‘s Find My Friends feature. After the third call with no answer, Brice checked out the location of Michael’s phone. Hours after Brice expected the Hamelins to arrive at his front door, the phone was sitting on the side of Interstate 20. Monitoring it over the next hour, Brice saw the phone wasn’t moving. He called the local police who told him about the crash. He learned that Beth had been transported to John Peter Smith Hospital in Fort Worth.
Brice hurried to the hospital with an iPad in tow. That’s how Beth was finally able to login to her Apple account to get the phone numbers she needed to call friends and family to tell them what happened. Social media then helped Beth inform Michael’s wide group of friends about a memorial service that would have been tragically empty without these tools to spread the word quickly and easily.
The hospital was only the beginning. Upon arriving home, Beth was confronted with her husband’s inaccessible mountain technology. Computers were a huge part of Michael’s life but, for reason’s we can’t know, he didn’t plan for death in his digital life.
Beth is not a professional hacker, so when she walked into the room where her husband hosted over a dozen well-secured Web and email servers, she had no idea what to do with them, how to shut them down, or even what they really were. Michael’s encrypted personal computers and safe-guarded personal Internet accounts seemed impenetrable.
Not knowing the passwords meant Beth didn’t know how to access the thousands of family photos Michael kept safe and secure on digital storage. As of publication, after months of searching, she still hasn’t found them.
The main challenge was Michael’s tech footprint: His Gmail, Twitter, personal domains, rented servers, hosting business, home servers, and a huge collection of Apple tech.
“It was tough for Beth because she got home and she had a brand new phone and couldn’t even get on the Wi-Fi,” Kalat said. “Michael had done everything. Beth is very smart—she’s a scientist—but Michael had handled everything. A friend had to come over to reset the Wi-Fi password.”
When Beth tried to retrieve Michael’s car from the Atlanta airport (the crashed car was rented for the vacation in Texas), Park ‘N Fly ignored them for hours. It took Kalat publicly calling them out on Twitter to finally get a response. That was the first sign that many companies, like human beings, don’t always plan well for death.
Hey @parknfly, what does it take to get a manager to call me back? My friend died with his car in your lot, and I’m trying to help get it.
— Andrew Kalat (@Lerg) December 29, 2014
Beth and several of Michael’s tech-savvy friends dove into his surprisingly large collection of paper records. Credit card statements in particular proved to be important first clues, and that’s how they found out he rented five servers at a data center.
Normally, no one but a server’s owner can physically touch it. That’s the rule Michael’s datacenter strictly stuck to. It took convincing and pleading to get a series of exceptions made to the data center’s security rules. From there, Michael’s friends broke into his servers by utilizing the physical access they had in order to reset the passwords and figure out what was on them. It was his hosting side-business, which they then began to shut down by letting all his customers known he had died.
“Death is a nuclear option,” Kalat said. Exceptions to important protocols are often made when a death takes place. A security expert himself, Kalat wondered if and how hackers and social engineers used that security weakness to their advantage.
“I’ve been involved in social engineering. When I saw how willing companies with little or no planning for death were to bend the rules, I thought, ‘Wow, this is a powerful technique,’” Kalat said.
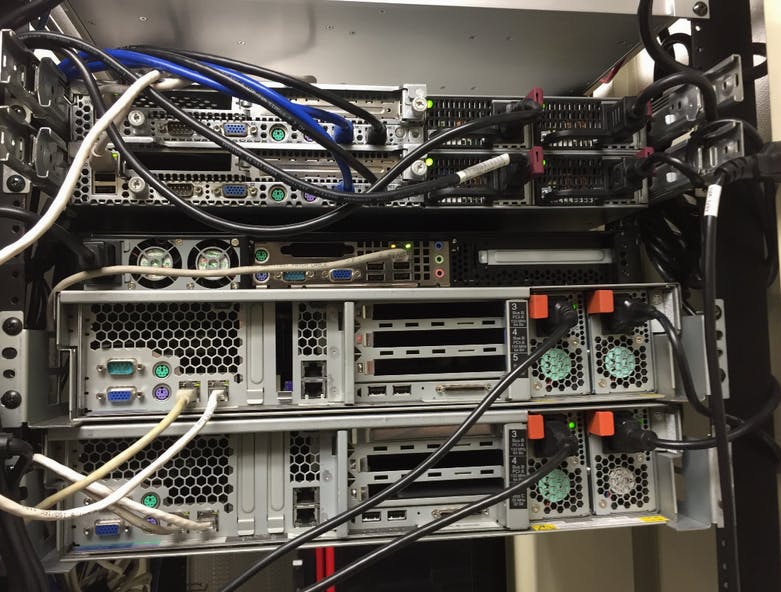
The five rented servers were a challenge to find and figure out, but Michael’s 18 servers running at home proved more difficult.
“We still don’t know what all of them are,” Kalat told me. Instead, a jungle of wires and LED lights have been plugged in and out over recent weeks in an attempt to map what piece of equipment is dependent on another. Understanding what’s inside all of them is another question entirely.
Michael’s personal machines are stubborn as well. His Macs were fully encrypted so that no one can view their contents or reset his passwords. The last hope, a recovery key that Apple gives a user in the event of a password change, is missing.
“In making his account so secure, he kept bad guys out,” Kalat said. “But he’s making it extremely difficult for his widow to have access to what he had.”
Next, Beth and Kalat tried to figure out how to reset Michael’s Apple.com password, which would allow them to reset his Mac password. Michael, ever the security-conscious hacker, had set up two factor authentication so that you need an Apple.com password, an Apple recovery key, or a trusted device. Beth has none of that, so the computers remain locked.
“Apple has no right of survivorship,” Kalat explained, “so there’s no automatic access for the next of kin. They feel that the data is personal and private, so access should die with the user.”
Michael’s Google account hasn’t been much better. Although Google does have a death policy, the company hasn’t responded in the more than two months since Michael died and the family submitted an application to access his data.
It’s not all bad, however. Facebook in particular has put a lot of thought into how to deal with death. They turn profile pages into memorials, forbid logins, and adjust the user so that they don’t show up in birthday notifications, suggested friends, or other features that would serve as painful reminders of loss.
Microsoft’s Outlook has another simple and straightforward process where, upon receiving proof of death, Microsoft will send a DVD with a user’s data to the next-of-kin. The account itself is shut down, and no one is able to login to it ever again.
Twitter will simply shut down a user’s account when notified of their death. Their data—public tweets and private messages alike—are gone.
It’s been three months since Michael died, and Beth has only been able to access and understand a sliver of what he left behind in the digital world. Kalat, who has been working closely with Beth to access Michael’s data, says this ought to be a wake up call to everyone who spends a significant amount of their life online—not just hackers.
“Our society hasn’t caught up to tech on next of kin issues,” he explained. “Very few companies have a policy to death with it.”
The experience drove Kalat to try to figure out what lessons can be learned from Michael’s death. His first piece of advice: Create a legacy drawer.
Most prominently advocated by author and radio host Dave Ramsey, a legacy drawer is a secure holding space for passwords, wills, estate plans, tax returns, contact information, and other important documents that allow families to more easily deal with the important practical matters that follow the death of a loved one. For you hackers or other security-focused people, it’s extremely useful to include things like network maps and gear labels so that your piles of computer don’t remain an unsolved mystery for the people you love.
In other words, planning begins before death. Anyone living with a significant other or family member ought to make sure that they not only understand one another but that they understand what each other do. Beth being unable to sign onto the Wi-Fi is the perfect example of a lack of that understanding.
“Switch roles for one month every year,” Kalat says. “If one person does the bills, handles the gas, does all the tech stuff, make sure the other person can do it too. Make sure they are equipped to survive without you.”
Photo via WikiArt/wikiart.org (PD) | Remix by Max Fleishman