The Latest
See all posts“We bought this one for under $40K”: Woman who lives in a church teaches others how they can do the same
"I’d have to sage the hell out of it… But the stained glass could be nice."
“Let’s just make more jokes”: Zara Larsson doubles down after abortion joke backlash in viral TikTok
"It doesn’t have to be taboo."
How are fans reacting to the end of “Smiling Friends”? Not well.
"Check on your neurodivergent friends."
“I thought I was going insane…”: Shopper compares Costco Babybel to Kroger version—and pulls out a scale
"There's a HUGE difference."
Fans want Caleb McLaughlin to play Miles Morales after “Stranger Things”
It's definitely a hot topic.
“Whole missing puzzle piece”: Woman hears one comment from a stranger. Then everything about her symptoms starts to make sense
"I just, randomly, like, twitch and I thought it was just an anxious habit."
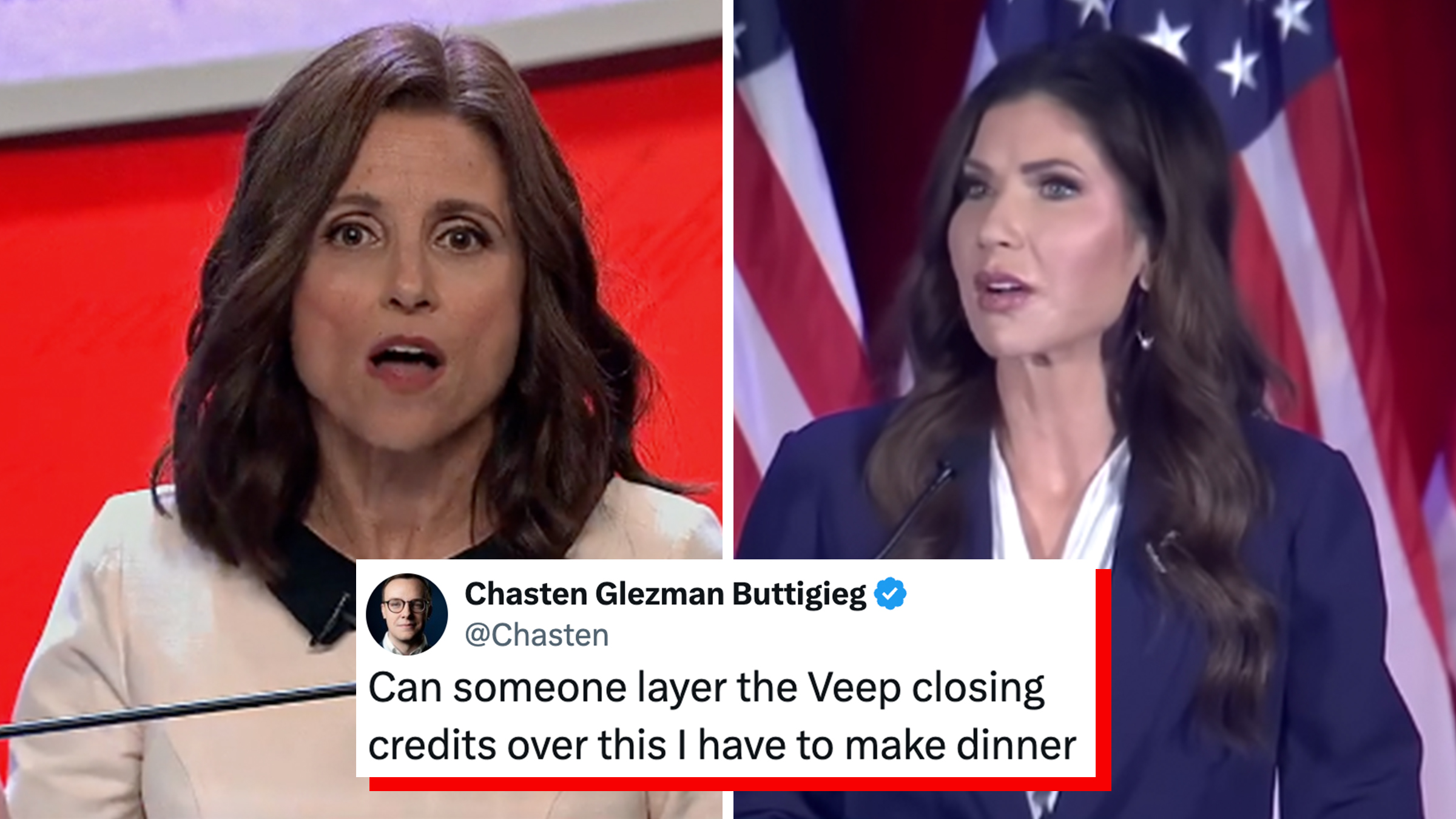
Kristi Noem’s final DHS speech gets the “Veep” end-credits treatment after Trump fires her
"I just spit out my Coke."
Entertainment
“Everything just looked terrifying”: No, that’s not Bill Clinton in “Ted”— why Seth MacFarlane’s AI-infused impression is sparking controversy
There were better alternatives.
“This one’s for you”: The Met responds after Timothée Chalamet claims “no one cares” about ballet and opera
Timothée Chalamet didn't know what kind of pot he was stirring.
What is the “Adam Driver bar?” How the actor set a new standard in voiceovers
That's one way to set the bar...
Viral Politics
“Some people will die”: Trump says “I guess” when asked if Americans should fear Iranian attacks
"I’ve killed all their leaders," Trump said. "That room is gone."
“Lunatic behavior”: Marine vet protesting Iran war appears to snap a bone during struggle with GOP senator
"I'm here in D.C. trying to speak out against the Senate and ask them why they're going to send our men and women into harm's way."
New Englanders are ready for war after RFK Jr. threatens to take on Dunkin’: “The American Revolution started in Massachusetts”
"I'm joining the war on Dunkin on the side of Dunkin."
“What am I gonna do in a submarine?”: Young Americans joke about a potential draft with Village People’s “In The Navy”
"Modern propaganda is sneaky, don't let it win."
Trending
“Nintendo’s lawyers will love this”: The Pokémon Company responds to White House Pokopia meme
The timeline could hardly get weirder.
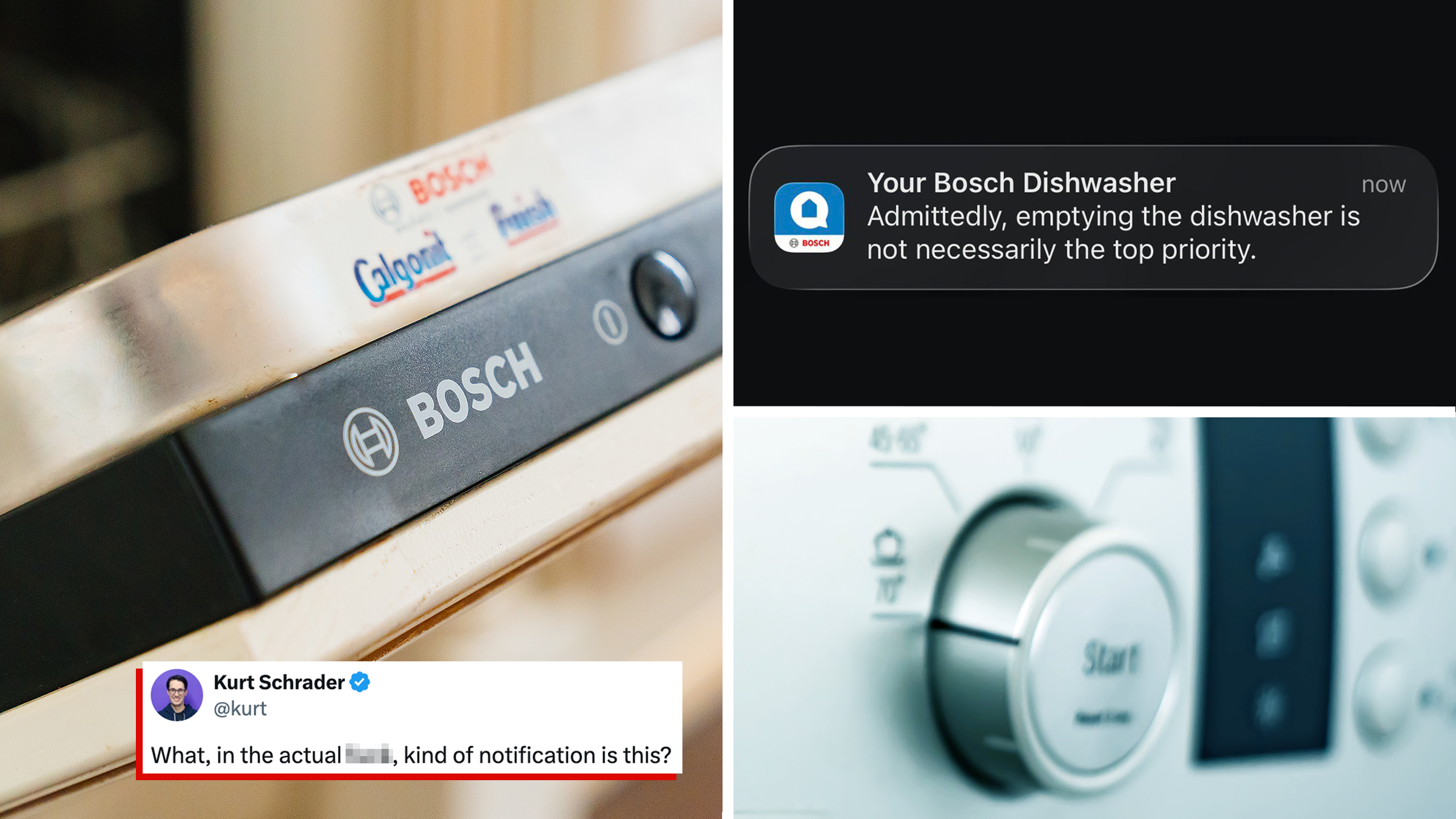
“Testing the limits of our patience”: Bosch 500 dishwasher’s “sassy” notification has the internet debating smart appliances
"The second my dishwasher sends me a push notification I’m unplugging it."
“That’s not 3 cups”: Woman measures boxed mac and cheese. The numbers on the package don’t add up
"I'm so tired of being ripped off."
“You rich bro, stop this”: James Harden mocked after AI-generated career video gets his own name wrong
"You make millions and can't hire artists?"
Culture
Tucker Carlson’s anti-war merch is going viral among the very people who hate him
"He’s going to accidentally have a best seller on his hands."
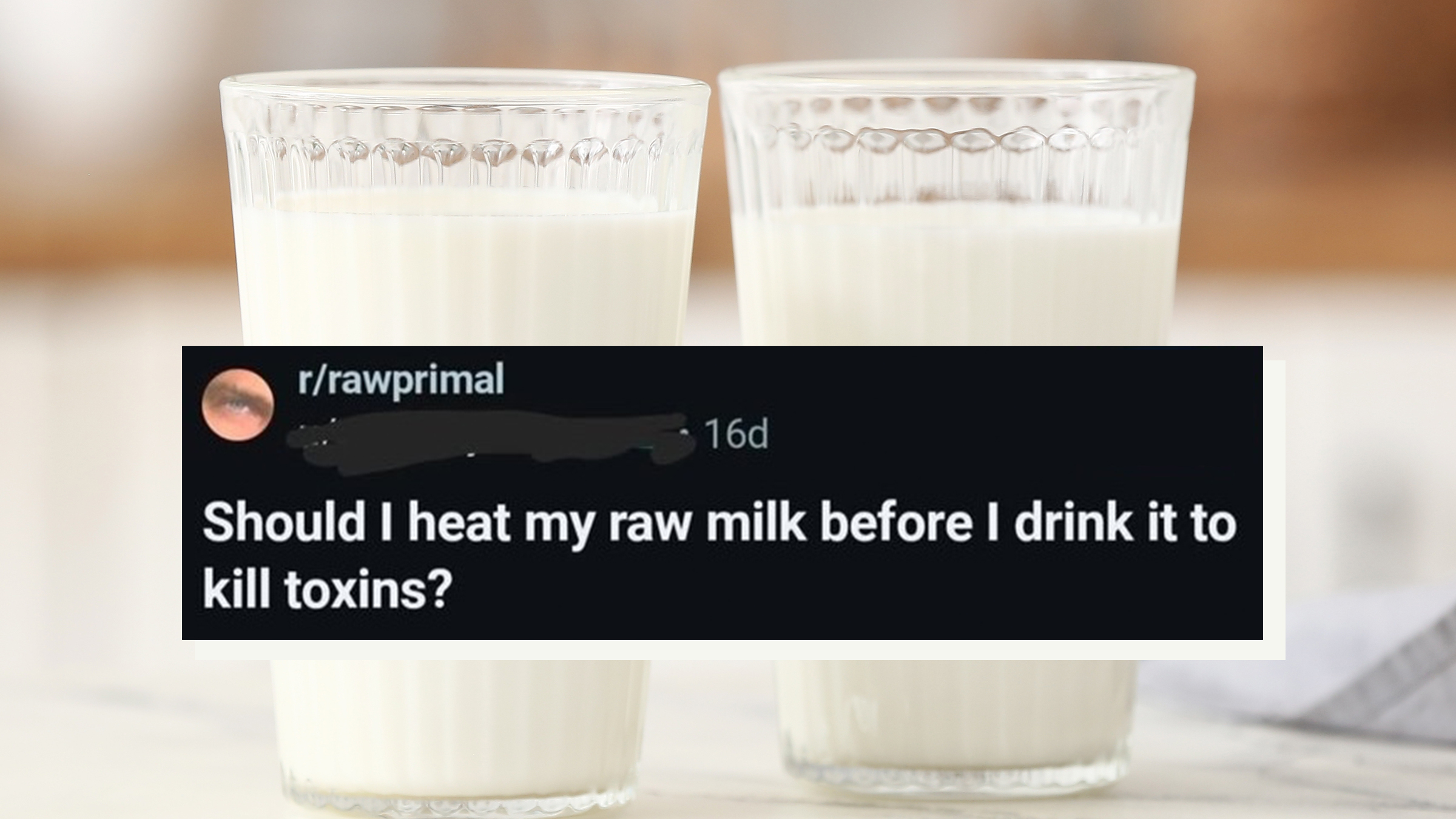
Raw milk Redditors keep accidentally rediscovering pasteurization
"Just buy milk from the grocery store then."
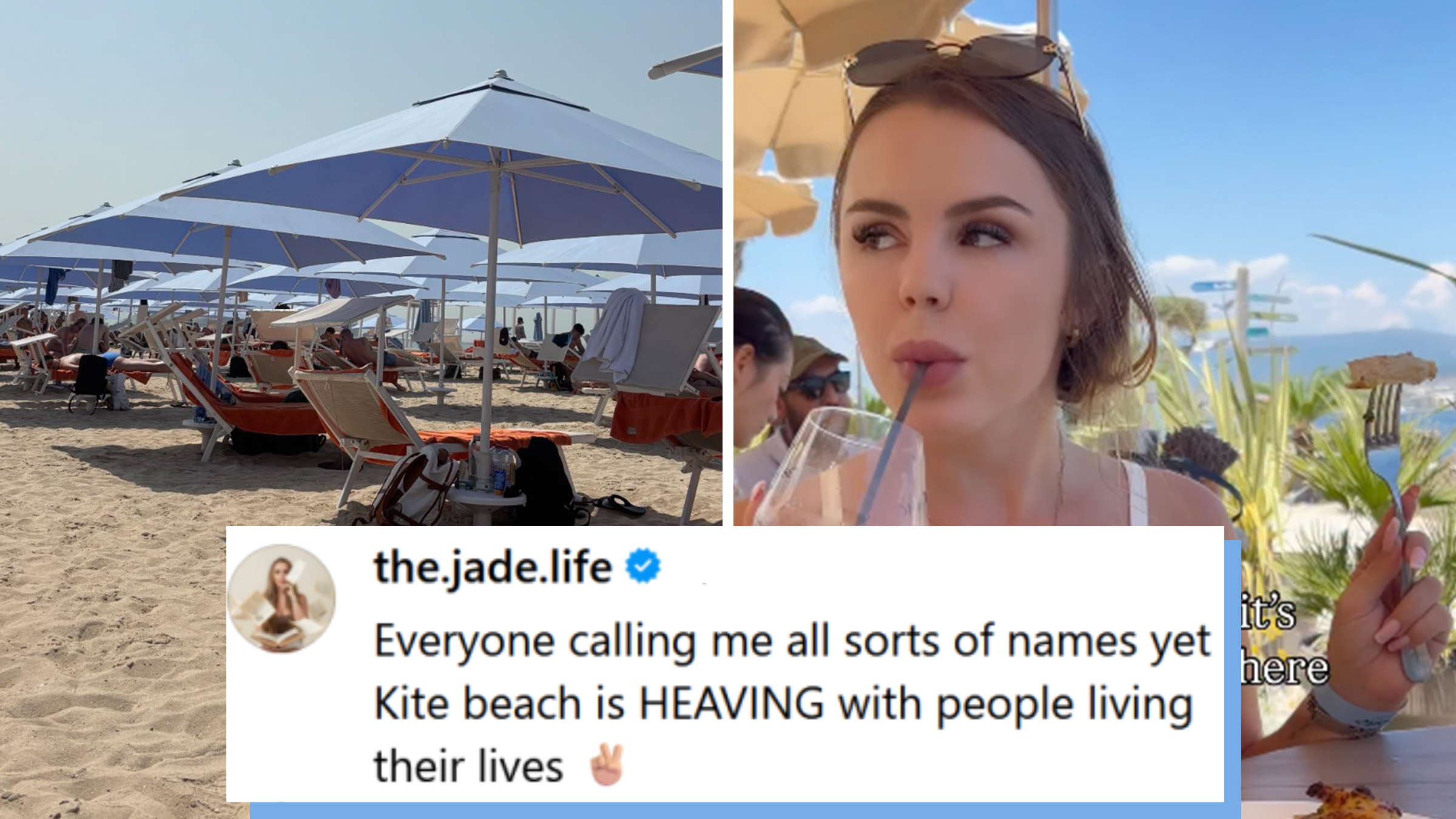
“No drama”: Influencer accused of “normalizing war” over post about “no fear” vacation in Dubai amid missile strikes
"Everyone is panicking about Dubai..."
Memes
New “Pokémon Winds and Waves” characters inspire memes and a “Republican” backstory
"Where was Boca Raton Pikachu on January 6th?"
Tyra Banks forcing models to pose with their trauma on “ANTM” inspires the “traumatic photo shoot” meme
"Reality Check: Inside America’s Next Top Model" is the newest meme-maker.
“Now I’m stressmaxxing”: Who is Androgenic? The viral wig snatch that’s dividing social media
"Now this looksmaxxing gymcel gets wig snatched?"
Woody’s “bald ass” is the obvious star of “Toy Story 5” so far. It’s already a meme
The OG fans are feeling old.
Tech
The next “Stardew Valley” update lets Clint get married, and the fandom is split over the “worst” character’s new upgrade
"I know he's a fixer-upper, but he has a job. And a beard. Which is more than I can say for a lot of these losers."
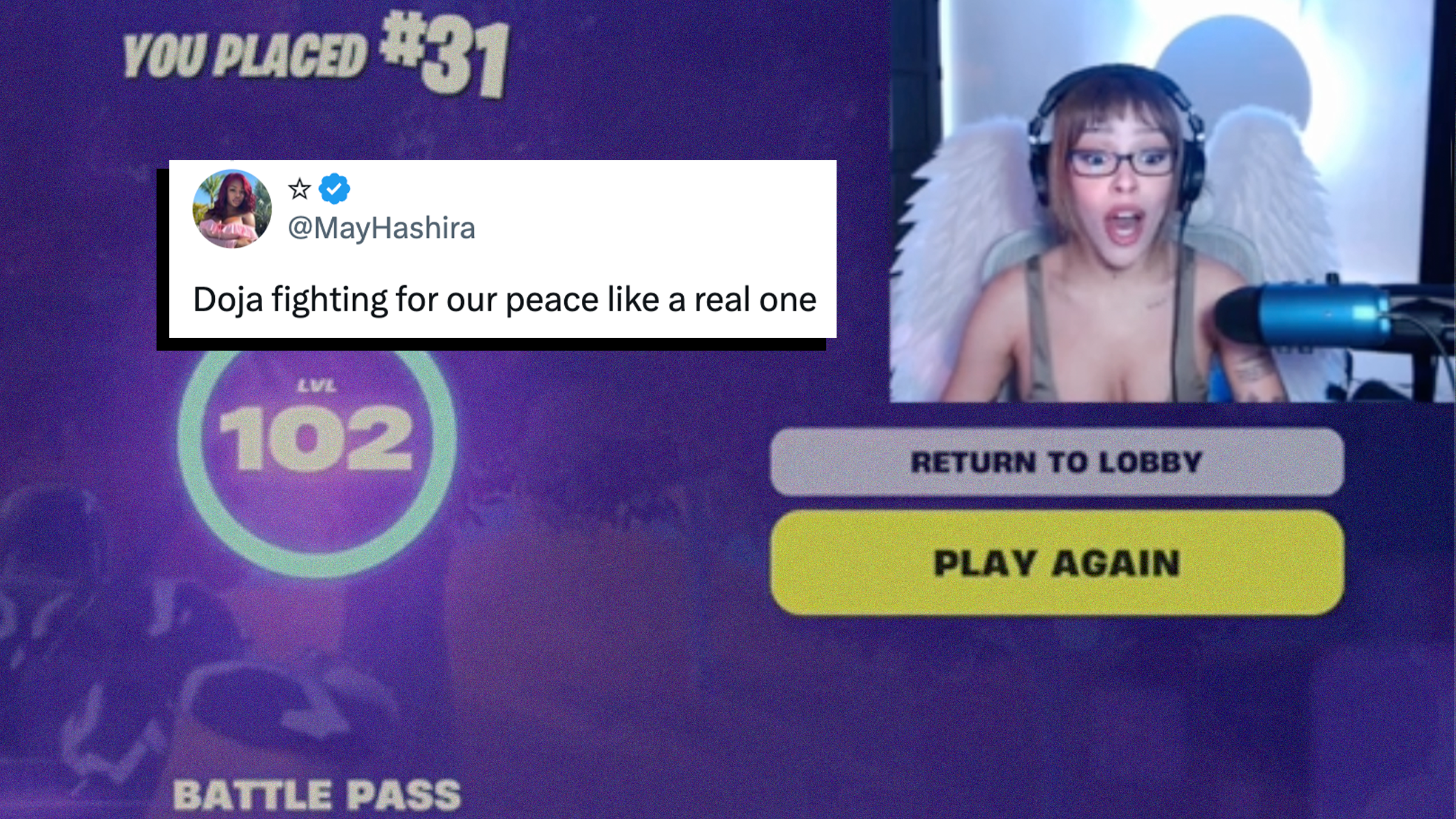
“Twitch really humbled her”: Doja Cat can’t figure out how to turn off livestream ads after new update
"You can win a Grammy, but you still can't skip the 30-second unskippable ad for insurance. Humbling for the ego!"
This startup says its $1,199 gadget can block listening devices. Skeptics are raising questions
"This would be extraordinary and would require equally extraordinary proof if true."
A new prank targeting Meta glasses wearers claims they’ll be banned if they look at a flag. It’s wrong.
"I just tried it, nothing happened."
TikTok
Influencer buys wedding dress while single. Now men are flooding her DMs
"Do I feel a little crazy being as single as I am? Yeah. But it was a great deal."
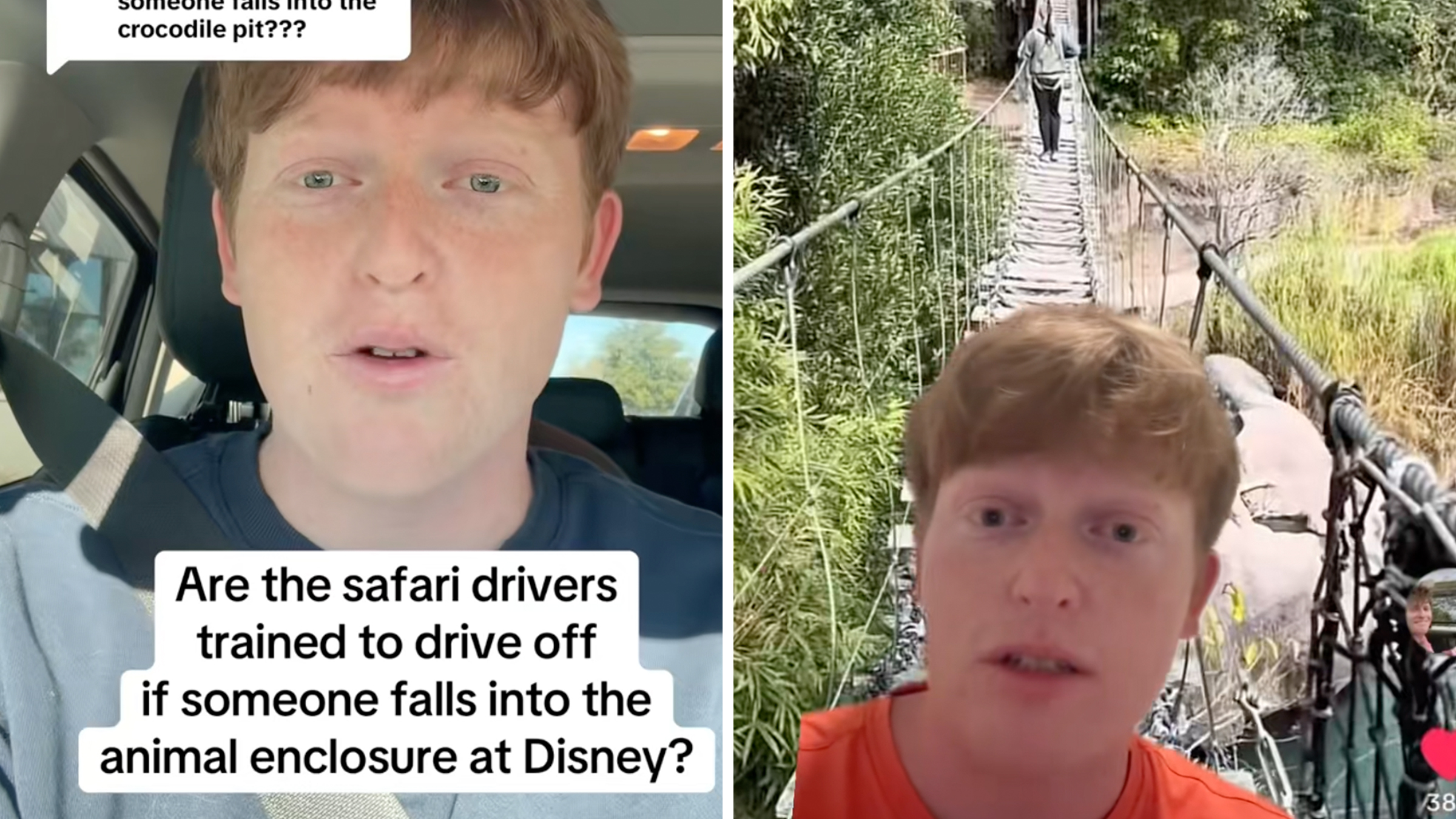
“They’re not saving that baby”: Former Disney World safari driver says staff are trained to drive away if someone falls into crocodile pit
No one’s fallen in yet, but you definitely don’t want to be the first.
“Why would you ever do this?”: TikTok psychic ordered to pay $10M to professor she defamed
"I would hope that this case makes them think before posting nonsense."
“I was dumbfounded”: Man breaks down after friend admits he’s not invited anywhere because he’s “poor”
A medical emergency landed him in the hospital, where his savings were wiped out.