In the fallout of the massive databases of login credentials that have made their way online in recent months, public figures have continuously had their social media accounts compromised. The latest victim was Oculus CEO Brendan Iribe.
The head of the virtual reality company had his Twitter taken over by an enterprising hacker on Thursday. The person who found their way into Iribe’s account appeared to be Twitter user @Lid, who declared himself new CEO from Iribe’s account.
“[W]e here @Oculus are very excited to announce our CEO. @Lid ! :)” one tweet sent out to Iribe’s 16,000 followers. He also issued a demand: “If Brendan wants his twitter back i want a free oculus rift so i watch porn the cool way.”
https://twitter.com/Lucas_Matney/status/748410883651473408
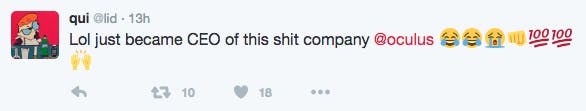
Lid replied from his own account acknowledging his newfound position of power with apathy. “Lol just became CEO of this shit company @oculus,” he tweeted.
Lid’s account has since been suspended from Twitter. Oculus confirmed to the Daily Dot that the account was indeed compromised and has since been secured. The tweets have since been deleted from Iribe’s feed.
At first glance, the incident appears to fall in line with the ongoing epidemic of technology company executives having their accounts cracked by third-party actors.
Earlier this week, Google CEO Sundar Pichai had his Quora account taken over. Mark Zuckerberg, the founder and CEO of Facebook, had his dormant Twitter account broken into last month. Amazon CTO Werner Vogels, Spotify CEO Daniel Ek, Uber CEO Travis Kalanick, and angel investor Mark Suster have all been caught in the crossfire as well.
Many of the high-profile hacks of top names in tech stem from the work of OurMine, a hacking collective that has begun branding itself as a security group that offers paid protection services. OurMine has taken to breaking into accounts owned by the tech elite and advertising their services.
While the Iribe hack would seem to fit into OurMine’s narrative, the tweets from the account don’t match the standard OurMine line. When contacted by the Daily Dot about Iribe’s account, a representative from OurMine said, “No, it’s [sic] wasn’t us.”
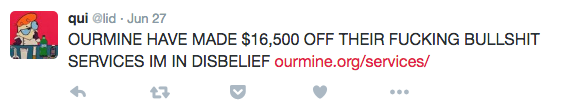
In fact, from Lid’s tweet history, which is now inaccessible, the apparent hacker seemed to have a grudge against OurMine. “OURMINE HAVE MADE $16,500 OFF THEIR FUCKING BULLSHIT SERVICES IM IN DISBELIEF,” he tweeted after a profile of the group was published by Business Insider.
The bad blood between Lid and OurMine stems from a prior relationship between the parties. “I actually used to be a part of the group OurMine, but they didn’t like that I was sharing their method of how they do things. So they kicked me,” Lid told the Daily Dot.
Lid said that the security scans that OurMine offers is little more than smoke and mirrors; what the group actually does is search common credentials in publicly available databases—often those maintained by LeakedSource, a subscription-based search engine that compiles stolen credentials.
While OurMine has maintained it gains access through security exploits, Lid alleges that the group is lying. “They seem to be embarrassed that they use LeakedSource to hack people like the rest of us,” he said, adding, “It’s also rather sad how they are actually making money off people by doing ‘security scans’ because they are just as talented as someone with a database.”
Lid—who is now offering free security searches for anyone concerned about their social media accounts—openly admits to using LeakedSource for his attacks on various accounts; it’s how he got into Iribe’s Twitter account after finding his password in the dump of stolen MySpace logins that surfaced in May 2016.
According to @Lid, he paid for a week of access to LeakedSource’s database—which contains credentials from massive leaks including MySpace, LinkedIn, dating site Badoo, and others. A subscription to LeakedSource’s database is rather inexpensive: a 24 hour trial costs $4 and a week of access $11, with prices rising as high as $320 for a full year, with discounted prices made available to those willing to pay in bitcoin.
Prior to paying for an account on LeakedSource, Lid said he was sponsored by the search engine. “All I had to do was tweet out from my account ‘Go check out http://leakedsource.com to secure yourself today!’ whenever I hacked someone and was gaining attention and they rewarded me with months of subscription,” he said.
Lid claimed to have hacked a variety of popular YouTubers and gamers including Boogie2988, Phantom Squad, Calfreezy, Gunns4Hire, Dare Rising, and Markiplier. Once his account was suspended because of the actions and subsequently lost the audience he had built up from his exploits, he said his subscription to LeakedSource was revoked.
“We have never sponsored anyone with the intent for them to teach people how to ‘hack,’” a representative from LeakedSource said. “The only people we have given ‘sponsorship’ accounts to where [sic] people who helped promote the service for the sole purpose of teaching others self awareness,” adding “LeakedSource does not engage in, encourage, or condone unlawful entry (‘hacking’) into private systems.”
While anyone can use LeakedSource for free to find out if their information is included in any of the databases, paid subscribers are able to see the passwords associated with the logins (emails, usernames, IP addresses, etc.). The passwords are hidden by default, according to Lid, but from there a user can click to reveal the password and see it in full.
Troy Hunt, a Microsoft Regional Director who maintains Have I Been Pwned—a service similar to LeakedSource that compiles credentials stolen in breaches—told the Daily Dot storing credentials in a publicly accessible environment poses a serious risk.
“If credentials are stored in any sort of retrievable format then it’s what we’d class as ‘insufficient cryptographic storage’ which ironically, is precisely what we berate websites for doing after they’re hacked and their internal storage mechanism is disclosed,” he explained.
A representative of LeakedSource told the Daily Dot that a new layer of security has been added to its databases for verification. “We only show the first three to four characters of the password. The user has to input the password he believe[s] the partial to be.” If the input is correct, the full password is revealed.
There is currently no limit on how many guesses a person can take at a given password, though LeakedSource said after a certain number of failed attempts, a CAPTCHA is added.
Hunt suggested this is likely insufficient protection, as partial passwords often imply what the full version is.
LeakedSource’s intention does appear to be to help people secure their online presence, as evidenced by their free and automated removal process that allows users to delete their credentials from the database. However, the site is still subject to abuse by malicious individuals.
Lid said the change to the password protection in LeakedSource database would likely drive him to a different service. “I’m pretty sure everybody, or maybe 95 percent of their customers use the website the same way as I do,” he suggested, predicting sales for LeakedSource would drop dramatically because of it.
A LeakedSource representative said the site had doesn’t take misuse of its system lightly and had implemented methods of preventing malicious use, including flagging accounts suspected of abuse for removal, but couldn’t offer specifics.
For those using LeakedSource, the definition of malicious intent may vary. Lid acknowledged concern for abuse of LeakedSource, but said “there’s people out there like Mr. Iribe where they absolutely deserve to be hacked.”
Lid had been looking for executives at gaming-related company who have been vulnerable to attack and came across Iribe’s credentials from MySpace. “If you still have the same password from 2014… then it’s your own fault and you gotta learn the hard way,” he said.
Iribe assuredly learned the value of updating passwords, but if higher-ups in companies that are part of the tech sector aren’t actively exercising online security protocols, then the average person likely isn’t either. Best practices for passwords are well-known by many but often dismissed for the sake of convenience.
Because of this, and because of the minimal amount of verification required to access personal information housed in LeakedSource’s database, users caught in a breach may be more exposed than they realize.
Hunt noted that it doesn’t bother him to see other sites online facilitating data breach searches, particularly because the service he offers is free, but said he was wanted other services to take steps to ensure they “do no harm” to data breach victims.
“Clearly if a service is being used to discover sensitive information about an individual then that puts them at risk and I’d like to see a rethink on holding credentials and making membership of sensitive sites publicly discoverable,” he said.
Update 12:14pm CT, July 1: In an statement provided by OurMine, the group claims that Lid has no current or prior affiliation with the group, and also that LeakedSource has never been used by OurMine in its security efforts.
H/T CNet