The fall of Silk Road has thrust Tor into the national spotlight.
On Tuesday, the front page of USA Today detailed the arrest of Ross William Ulbricht, the alleged owner of the most successful online black market, and included a primer on how the Deep Web works.
But Tor, the powerful browser service, is even more popular than you think. And despite what you may read in your morning paper, it’s not just notorious drug slingers, hitmen, and child pornographers making use of the anonymous Web.
Both Julian Assange and Edward Snowden used anonymizing technology to leak tens of thousands of pages of sensitive information, while militaries, governments, journalists, global businesses, and everyday people are increasingly turning to Tor for private dialogue.
In the shadow of revelations about the National Security Agency’s surveillance efforts, anonymity networks have become more popular than ever. Tor, I2P, and Freenet have combined to more than double in size in the last year, and approximately 1,050,000 total machines “legitimately” use the networks on a daily basis, amounting to an anonymous population that is about 0.011 percent of all machines currently connected to the Internet.
These tools are designed to hide their users, so many of the statistics presented here are only estimates. However, the Daily Dot spoke with developers on all three projects and consulted public statistics considered reliable by those developers and users. While it’s impossible for us to obtain exact metrics, it’s clear that the estimates are telling us something very loudly: Anonymity networks are growing fast.
Tor
By design, Tor is a powerful anonymous proxy service to the Internet. Originally known as the Onion Router, a nod to the numerous layers of encryption and routing of data that protect Tor and its users, first launched in 2002.
While it’s widely famous for its “hidden services,” such as the Silk Road black market, Roger Dingledine, Tor’s project leader, insists those are “just an experimental feature that we added to show how flexible the design is.”
Indeed, most Tor users are browsing the “normal Internet,” not the Deep Web. Tor allows users to access websites like Facebook, Dingledine continued, “without the local network learning where they’re going and without Facebook learning where they are today, or to browse news articles without letting advertising companies build a larger profile of their interests.”
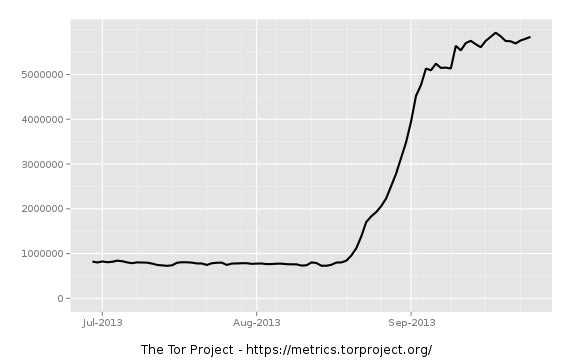
Tor’s utilized by 1 million legitimate machines daily. The true number of Tor machines is closer to 6 million, but about 5 million of those “are due to a recent botnet infecting a bunch of computers and running Tor clients on them,” Dingledine said.
Tor has experienced 100 percent real user growth since this time last year when the network’s population stood at about 500,000 users.
While Tor has played a major role in dissident movements in hotspots such as Iran, Egypt, Bahrain, and Syria, its largest base by far is in America, which accounts for about 13 percent of daily users. Adding up to about 2700 mebibytes per second, Tor represents an outsized amount of Internet traffic. It adds up to .014 percent of total Internet traffic, according to Tor’s public metrics, and it has the potential to handle up to .023 percent, or 4500 mebibytes per second.
I2p
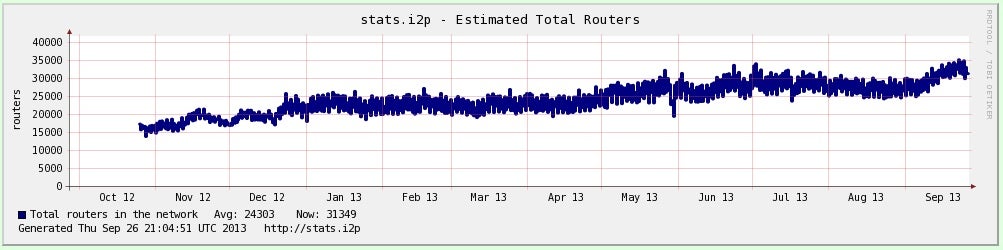
The Invisible Internet Project, more commonly known as I2P, is another popular anonymity network currently supporting an estimated 35,000 users daily, according to I2P statistics and Lars Schimmer, the project’s treasurer.
Although I2P is similar in many ways to Tor, there are a few key differences. Unlike Tor, I2P’s designed specifically for Deep Web hidden services and generally load them faster. For that reason, several popular Tor hidden services have I2P mirrors. I2P also handles encryption in a unique fashion called garlic routing.
Importantly, I2P is extremely peer-to-peer friendly. While Tor discourages heavy downloading, I2P users are BitTorrent aficionados, a fact made clear in the network’s relatively thriving piracy scene.
The project, which was initially released in 2003, has seen 111 percent growth since last year and a 25 percent jump in users in the last few weeks. Schimmer, known online as Echelon, credits the jump to increasingly strong censorship in Russia, as well as I2P’s Android app.
“From our point of view, the three [big anonymity networks] do not really fight against each other,” Schimmer wrote. “We work together, each in a separate field of specialized topics.”
Freenet
Freenet is unique among the big three in that it’s a highly decentralized peer-to-peer platform. In contrast to Tor and I2P, every Freenet user stores encrypted pieces of media on his or her hard drive without knowing the full contents of the file. The entire network is spread out across thousands of hard drives around the world.
Users can either connect to a wide variety of other users or, in the network’s most secure state, Freenet can be made to only connect to explicitly trusted friends of the user. This makes Freenet one of the most secure peer-to-peer networks in existence.
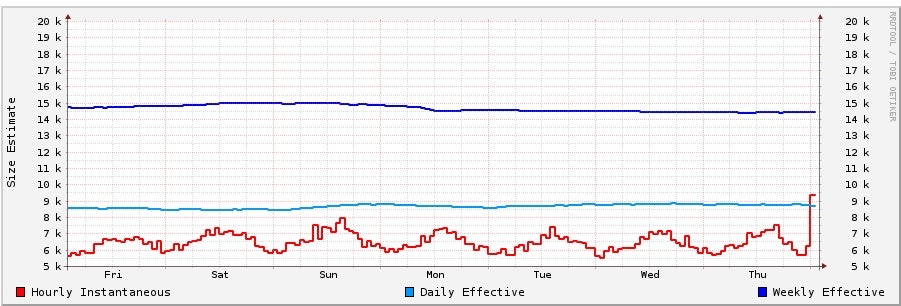
As the smallest and perhaps most unique anonymity network of the big three, Freenet boasts an estimated 15,000 users daily, according to developer Ian Clarke, who pointed us to these statistics.
Despite its relatively small size, Freenet is growing quickly. The network’s total storage capacity is just over 140 terabytes. The network has “grown by about 33 percent since late July,” according to Clarke.
“It’s hard to tell [why] for sure,” he said, “but looking at our website’s Google Analytics, there are a few recent traffic bursts from sites related to the Snowden revelations about NSA spying, such as http://prism-break.org/.”
Freenet has long played an important role in fighting Internet censorship. In a 2011 report by Freedom House, Freenet was rated as one of the most heavily used anti-censorship tools in China as well as the only tool to achieve perfect ratings from users in that country.
Illustration by Jason Reed