Set up a proxy server. Copy. Paste. Change five numbers. Congratulations, you have just hacked an electric car.
Computer security researcher and hacker Troy Hunt demonstrated on his website a very simple method of hacking a Nissan Leaf—the company’s all-electric hatchback—from halfway around the world. Hunt was able to use the functionality of Nissan’s iPhone app on his computer instead of his phone. That might not seem so nefarious, but that was before he started controlling someone else’s car.
This security vulnerability allows hackers to control the car’s HVAC system, or heating, ventilation, and air-conditioning. It also gives hackers extensive trip information as well as power usage, drive state, and a username that could potentially contain personal information. To make matters worse, the identity of the hacker is kept completely anonymous.
What that anonymous user could do is run all the systems of someone’s car while they are away until the battery dies, effectively leaving them stranded.
In a video posted on Youtube, Hunt sat outside in sunny Australia and controlled the HVAC system of a car parked in dreary Northern England. He then picked apart the trip information of fellow security researcher Scott Helme.
As you can see from the video, the process is fairly straightforward and the wealth of trip information gathered is being recorded by the Carwings Remote Control App.
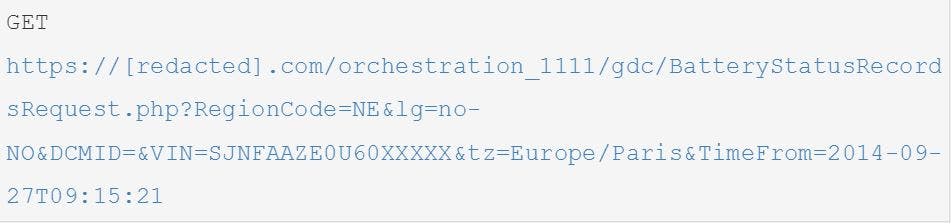
The anonymous researcher who first found out about the Leaf’s vulnerabilities turned his computer into a proxy between the mobile app and Nissan’s servers, then intercepted requests made between the two. It’s called a man-in-the-middle attack and without authentication it allows the user to step in-between two servers and eavesdrop on their conversation. Here is what was heard:
See that section with five Xs toward the end? That’s the VIN, or vehicle identification number, and it’s the only unique identifier between one Leaf and another. Change that VIN from your car to someone else’s and you are now in control of their vehicle. Don’t know someone’s VIN? Just look at their windshield, where it is placed on almost every car.
Put bluntly, Nissan’s security measures are seriously lacking. Think about it this way: Every Leaf has a VIN number, like every house has an address. Find out the address, and you can easily get to the house. The problem? The doors of these houses don’t have locks. That is, there is no authentication in place to prevent the interception of these requests. No username or password.
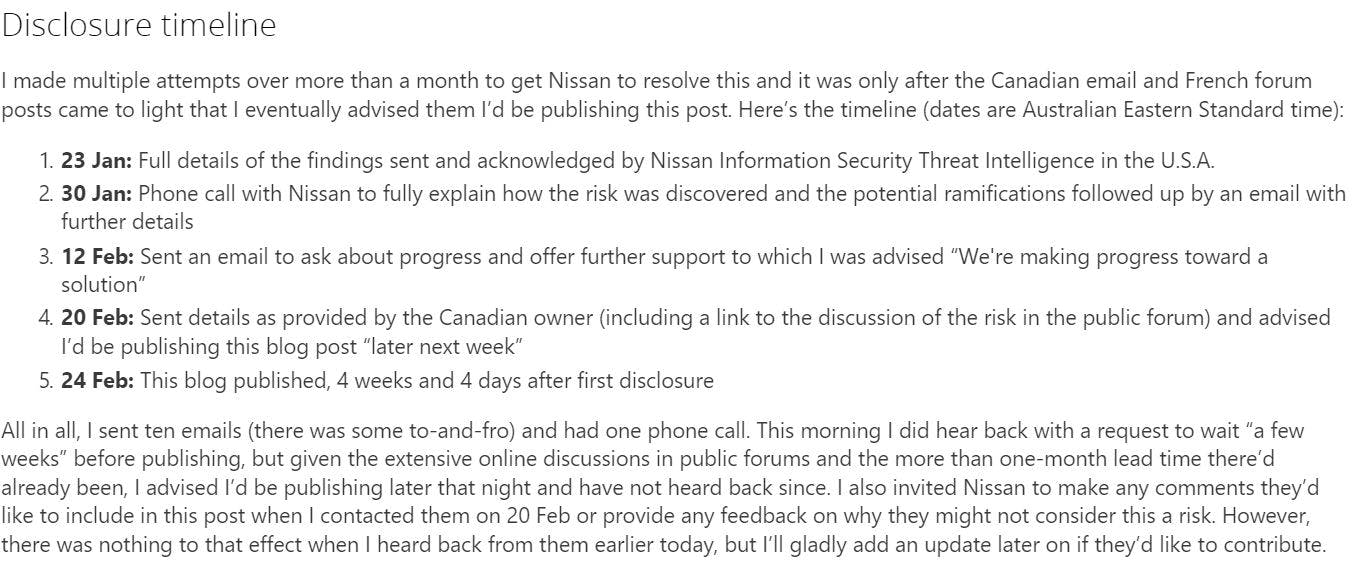
It’s been 33 days since Hunt discovered this security vulnerability and 32 since he told Nissan. So far, nothing has been resolved. Here is Hunt’s disclosure timeline:
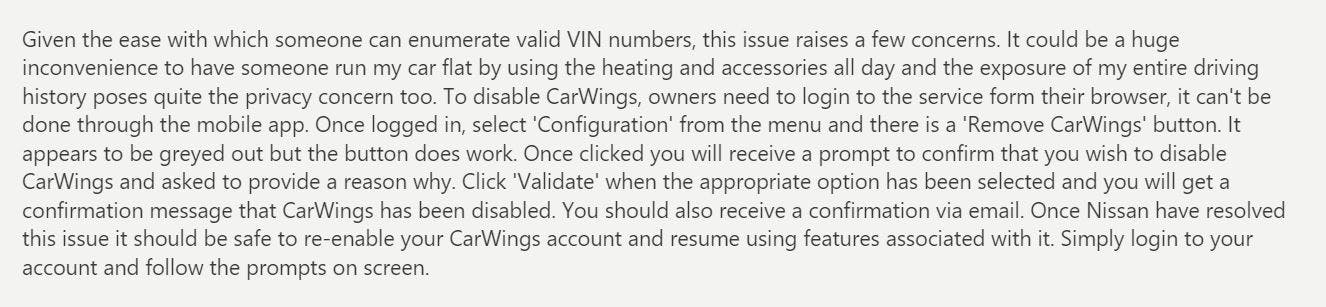
So what can you do right now if you own a Nissan leaf? Disable your CarWings account, according to Hunt who has also provided instructions on doing so:
And for everyone else, lets hope car companies recognize the potential dangers of security vulnerabilities in this trend toward electric vehicles and operating them remotely. Because, sadly, it can get a lot worse, and much more dangerous.
H/T Jalopnik | Screengrab via Auto Trader/Youtube