Apple knew as early as March 2014 of a security hole that left the personal data of iCloud users vulnerable, according to leaked emails between the company and a noted security researcher.
The emails, obtained earlier this month by the Daily Dot and reviewed by multiple security experts, show Ibrahim Balic, a London-based software developer, informing Apple of a method he’d discovered for infiltrating iCloud accounts.
The strength of Apple’s security came under fire earlier this month after hundreds of celebrity nude photos, allegedly stolen from iCloud servers, flooded the Internet. While the exploit Balic says he reported to Apple shares a stark resemblance to the exploit allegedly used in the so-called “Celebgate” hack, it is currently unclear if they are the same vulnerability.
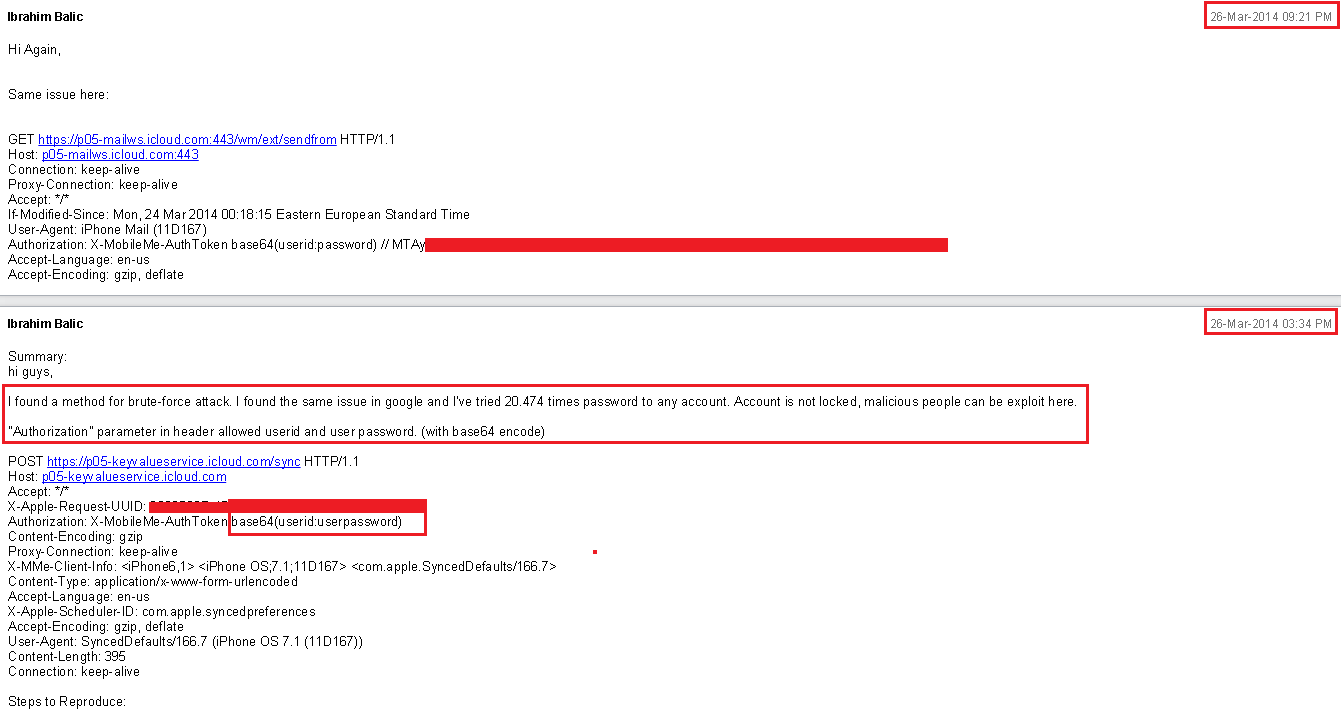
In a March 26 email, Balic tells an Apple official that he’s successfully bypassed a security feature designed to prevent “brute-force” attacks—a method used by hackers to crack passwords by exhaustively trying thousands of key combinations. Typically, this kind of attack is defeated by limiting the number of times users can try to log in.
Balic goes on to explain to Apple that he was able to try over 20,000 passwords combinations on any account. “I would like to inform you for it to be fix,” he wrote. (Editor’s note: Balic’s emails were written in English, which is not his first language.)
The vulnerability was also reported by Balic using Apple’s online bug submission platform, as seen in the following screenshot:
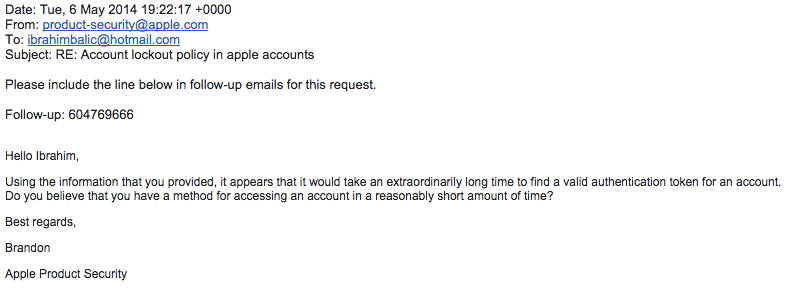
In an email dated May 6, 2014, the reported vulnerability apparently remains unfixed, as an Apple official continues to question Balic over the details of his discovery.
“I believe the issue was not completely solved. They kept asking me to show them more stuff,” Balic told the Daily Dot.
A security hole in Apple’s cloud storage service was initially blamed for the Celebgate hack. A malicious script was reportedly uploaded to the website GitHub late last month, according to The Next Web, which may have been used by hackers to compromise iCloud accounts:
“The vulnerability allegedly discovered in the Find My iPhone service appears to have let attackers use this method to guess passwords repeatedly without any sort of lockout or alert to the target. Once the password has been eventually matched, the attacker can then use it to access other iCloud functions freely.”
Soon after the Celebgate photos exploded across the Web, Apple reportedly patched the vulnerability identified in the GitHub post. The company denied, however, that it was in any way linked to the Celebgate event. The theft of the photographs, a statement from the company insisted, was not the result of “any breach in any of Apple’s systems including iCloud or Find my iPhone.”
Apple also expanded the use of two-step verification to further protect iCloud accounts. Users must opt-in to apply the additional security, which requires them to enter a four-digit code sent by text message each time they log in.
Stolen celebrity photos, likely obtained before Apple bolstered its security, continue to appear online. On Saturday, alleged nude photos of Jennifer Lawrence, Kim Kardashian, and others were posted on the website 4chan. The FBI is still investigating the hack, according to a recent statement from the law enforcement agency.
Balic’s brute-force iCloud attack is not his first vulnerability report to Apple. In June 2013, he identified a security flaw in the Apple Developer Center. According to Balic, the website was almost immediately taken down, but he says his report received no response from the company. In a press release issued a few days later, Apple described a “security threat” and claimed that “an intruder attempted to secure personal information of [registered developers.]”
Unhappy with how Apple handled his report and concerned that law enforcement was investigating their accusations, Balic went public in the form of a comment on a TechCrunch article. He later uploaded a YouTube video, which he says contains proof of his discovery.
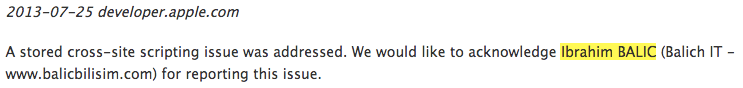
Apple later acknowledged Balic for reporting a cross-site scripting (XSS) vulnerability on its Web Server notification page.
Earlier this month, Apple CEO Tim Cook said his company should have done more to alert its customers of security issues.
“When I step back from this terrible scenario that happened and say what more could we have done, I think about the awareness piece,” he told the Wall Street Journal. “I think we have a responsibility to ratchet that up. That’s not really an engineering thing.”
Balic agreed. “If Apple had taken this issue more seriously, perhaps such a problem would not have arisen,” he said.
Apple did not respond to multiple requests for comment.
Illustration by Jason Reed