A coalition of security researchers studying the 2014 Sony Pictures hack has implicated a prominent hacker group with access to a powerful arsenal of digital intrusion tools.
The researchers, who spanned the globe from Silicon Valley to Moscow and worked under the title “Operation Blockbuster,” say the hacker collective, known as the “Lazarus Group,” is only getting started.
The security companies studying the landmark cyberattack—Novetta, AlienVault, Symantec, and Kaspersky Lab—revealed the results of a year of research on Wednesday.
In one of the largest data breaches in history, the hackers stole terabytes of data from the servers of Sony Pictures Entertainment (SPE) before wiping them clean, dealing the studio a crippling blow from which it took months to recover and alarming corporations and governments worldwide.
It was the act of “a single group, or potentially very closely linked groups sharing technical resources.”
In Washington, lawmakers urged President Obama to “respond in kind” to what Secretary of Homeland Security Jeh Johnson portrayed as “an attack on our freedom of expression and way of life.” The Federal Bureau of Investigation ultimately blamed the North Korean government for the attack, and the White House responded by imposing new sanctions on the already heavily ostracized regime of Supreme Leader Kim Jong-un.
Due to the amount of guesswork typically involved in attributing cyberattacks, the FBI’s call was greeted with skepticism. In February 2015, Jeffrey Carr, the head of U.S. security firm Taia Global, identified a Russian hacker allegedly working for the country’s Federal Security Service as culprit, saying he had been selling access to Sony’s network.
Wednesday’s report does not attempt to attribute the attack to any specific country or known individuals, beyond identifying the responsible party as a group called Lazarus.
“This group has been active since at least 2009, and potentially as early as 2007, and was responsible for the November 2014 destructive wiper attack against Sony Pictures Entertainment,” the report says.
The researchers stressed that their analysis “cannot support direct attribution of a nation-state” but added that the FBI’s claims “could be supported by our findings.”
The attack was not, as some have speculated, the work of disgruntled studio employees or hacktivists, according to this report. Instead, researchers wrote, it was the act of “a single group, or potentially very closely linked groups sharing technical resources, infrastructure, and even tasking.”
Jaime Blasco, chief scientist at AlienVault, said in a statement that the Lazarus Group had “the necessary skills and determination to perform cyber espionage operations for the purpose of stealing data or causing damage.”
“By combining this with the use of sophisticated disinformation and deception techniques,” he said, “the attackers have been able to launch several successful operations over the last few years.”
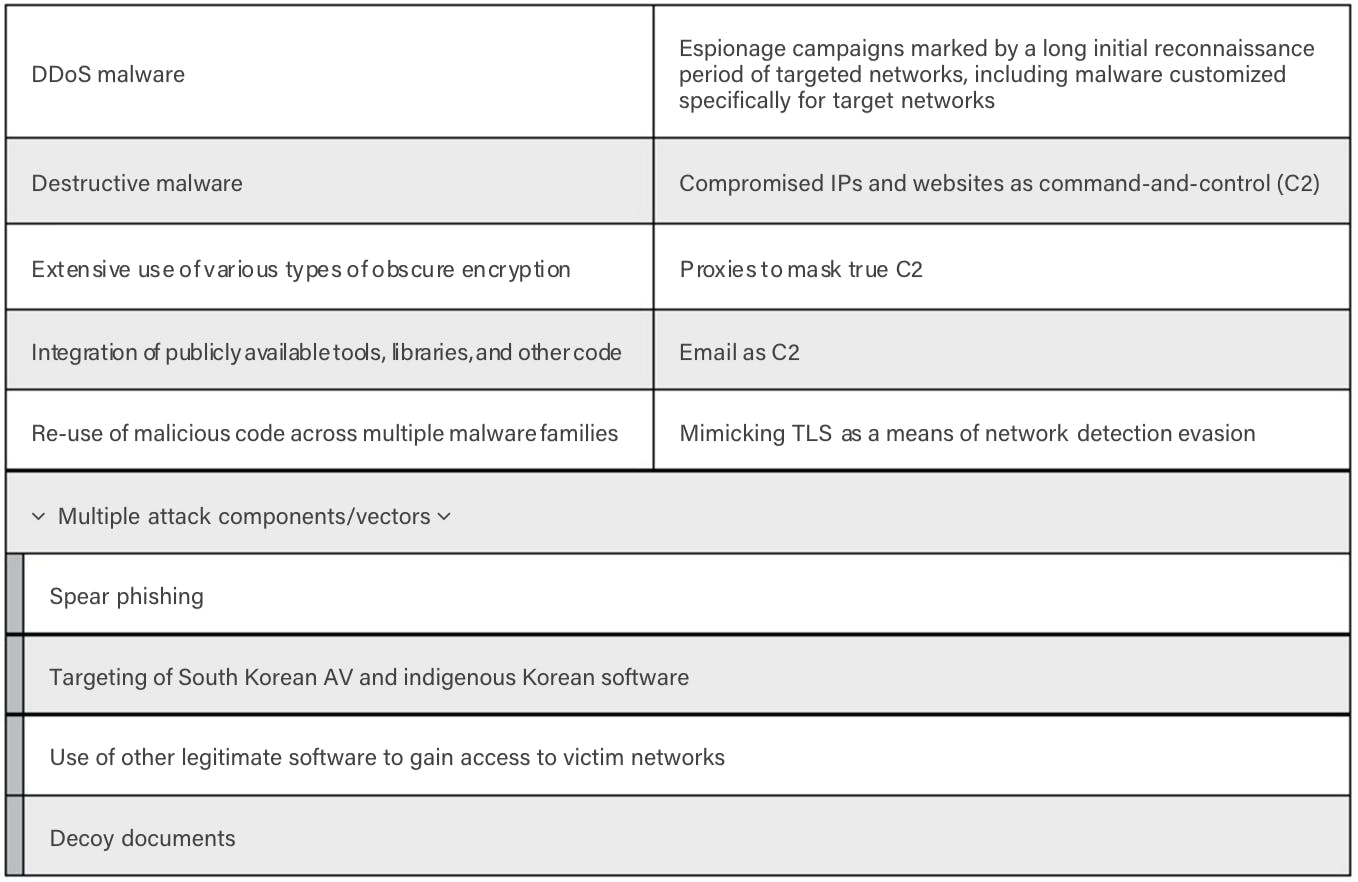
Operation Blockbuster’s analysis of the tactics, techniques, and procedures employed by the Lazarus Group unearthed evidence of cyber espionage, data theft, and destructive attacks primarily targeting government, media, and financial entities in South Korea and the United States.
Based on malware samples from the Sony attack, Novetta researchers identified commonalities in the code and libraries being used “across multiple malware families.”
In all, the investigators found more than 45 distinct malware families that fall under the Lazarus Group’s toolset, including the ones deployed to wipe Sony’s servers clean.
“By identifying the malware linked to the [Sony] attack and other related samples and capabilities, Novetta has been able to compile a picture of a group that has been active for nearly a decade,” the report said. “Based on analysis of the extensive malware set collected, as well as details found in public reporting from linked attacks, the Lazarus Group appears to have resources that allow for development of custom malware tools for extensive, targeted, and coordinated attacks, including long periods of reconnaissance.”
Cyberwar researchers at IssueMakersLab connected the Lazarus Group to the March 2013 DarkSeoul attack in South Korea, which in turn has been linked to malicious activity targeting the country as far back as 2007.
Likewise, the Lazarus Group has been tied to “Operation Troy,” a 2009-2012 cyber-espionage campaign targeting South Korea, according to Novetta, in addition to the March 2011 “Ten Days of Rain,” a series of crippling distributed denial-of-service attacks targeting the Seoul government.
Read the full Operation Blockbuster report:
Photo via Coolcaesar/Wikimedia Commons (CC BY SA 3.0)