Sitting inside a medium-security federal prison in Kentucky, Jeremy Hammond looks defiant and frustrated.
“[The FBI] could’ve stopped me,” he told the Daily Dot last month at the Federal Correctional Institution, Manchester. “They could’ve. They knew about it. They could’ve stopped dozens of sites I was breaking into.”
Hammond is currently serving the remainder of a 10-year prison sentence in part for his role in one of the most high-profile cyberattacks of the early 21st century. His 2011 breach of Strategic Forecasting, Inc. (Stratfor) left tens of thousands of Americans vulnerable to identity theft and irrevocably damaged the Texas-based intelligence firm’s global reputation. He was also indicted for his role in the June 2011 hack of an Arizona state law enforcement agency’s computer servers.
 There’s no question of his guilt: Hammond, 29, admittedly hacked into Stratfor’s network and exfiltrated an estimated 60,000 credit card numbers and associated data and millions of emails, information that was later shared with the whistleblower organization WikiLeaks and the hacker collective Anonymous.
There’s no question of his guilt: Hammond, 29, admittedly hacked into Stratfor’s network and exfiltrated an estimated 60,000 credit card numbers and associated data and millions of emails, information that was later shared with the whistleblower organization WikiLeaks and the hacker collective Anonymous.
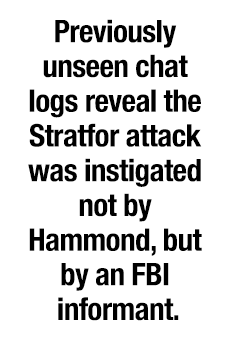
Sealed court documents obtained by the Daily Dot and Motherboard, however, reveal that the attack was instigated and orchestrated not by Hammond, but by an informant, with the full knowledge of the Federal Bureau of Investigation (FBI).
In addition to directly facilitating the breach, the FBI left Stratfor and its customers—which included defense contractors, police chiefs, and National Security Agency employees—vulnerable to future attacks and fraud, and it requested knowledge of the data theft to be withheld from affected customers. This decision would ultimately allow for millions of dollars in damages.
The documents also confirm the integral role of a shadowy hacker, operating under the handle “Hyrriiya,” who provided key access for the now-infamous attack.
FROM MOTHERBOARD:
How an FBI informant helped Anonymous hack Brazil
The FBI’s official version of the Stratfor hack, as reported by the New York Times, is that the bureau was made aware of the breach on Dec. 6, 2011, after hackers were already “knee-deep” in confidential files. The FBI claims Hammond informed hacker-turned-informant Hector Xavier Monsegur—also known by the online alias Sabu—of the vulnerability at Stratfor. In turn, the FBI immediately notified the intelligence company, though at that point it was already “too late.”
During his trial, Hammond claimed that the roles were actually reversed: It was Monsegur—released last week on time served—who first introduced him to an anonymous hacker, now known as Hyrriiya, who “supplied download links to the full credit card database as well as the initial vulnerability access point to Stratfor’s systems.”
“I had never even heard of Stratfor until Sabu brought it to my attention,” Hammond said.
His statement echoed a May 2012 letter ostensibly written by Hyrriiya and provided to Hammond’s legal defense team. “I am stating and admitting, AS FACT, that I was the person who hacked Stratfor,” wrote Hyrriiya, a skilled hacker, who’s known primarily for his involvement in hacks of Syrian government websites for Anonymous, two months after Hammond was charged.
Previously, however, no public records have substantiated Hammond’s and Hyrriiya’s claims.
New information, obtained by the Daily Dot and Motherboard in April, not only affirms Hammond’s version of events, but also longstanding accusations that federal investigators allowed an informant to repeatedly break computer-crime laws while in pursuit of Hammond and other Anonymous figures. Further, contrary to its prior statements, the FBI, through its surveillance of Monsegur, was aware of a security breach in the network of the private intelligence company well before it was “too late.”
The evidence on which the Daily Dot-Motherboard investigation is based was collected by Monsegur and his FBI monitors during his time as an informant from June 2011 to March 2012. The cache of court documents includes thousands of previously unseen chat logs, surveillance photos, and government documents, all currently sealed under a protective order upheld by a federal judge in the Southern District of New York.
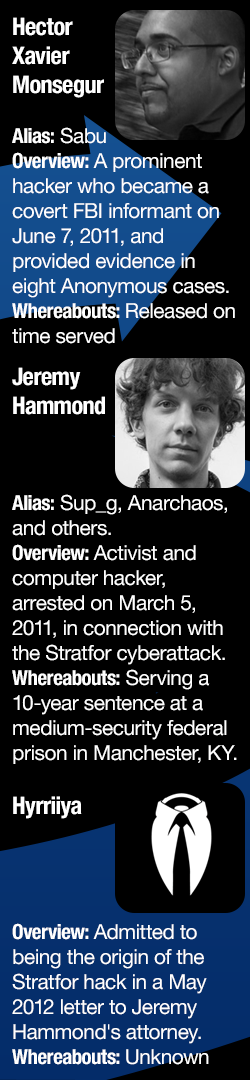
According to the chat logs, on Dec. 4, 2011, Hyrriiya informed Monsegur that he’d compromised the company’s systems. Monsegur responded, “That’s perfect for #antisec.” (“AntiSec” refers to hacking group that formed in the summer of 2011 as an offshoot of LulzSec, which was cofounded by Monsegur. The term itself comes from the Anti Security Movement of the early 2000s.)
Hammond was not present during this initial conversation about Stratfor, which took place in an Internet Relay Chat (IRC) room called “#Revolusec.” After Hyrriiya provided Monsegur with the names of several Stratfor clients—Cisco, Monsanto, Microsoft, and Oracle—Monsegur, as Sabu, told Hyrriiya to contact him through private messaging.
These time-stamped chat logs were retained by the FBI for the investigation of Hammond:
Monsegur first learns about the Stratfor breach from Hyrriiya on Dec. 4, in a chatroom called #RevoluSec.
In short order, Hyrriiya promised Monsegur access to Stratfor and delivered the details for eight credit cards from Stratfor’s database as further proof that he’d infiltrated its systems. The private data belonged to employees of the National Security Agency (NSA); the North Atlantic Treaty Organization (NATO); the International Association of Chiefs of Police (IACP); and Booz Allen Hamilton, the former employer of NSA whistleblower Edward Snowden; among others. The data included names, credit card numbers, expiration dates, credit card security codes, billing addresses, and other contact information. (Editors’ note: For the purpose of protecting the victims’ identities and financial information, that portion of the conversation has been intentionally withheld from this report.)
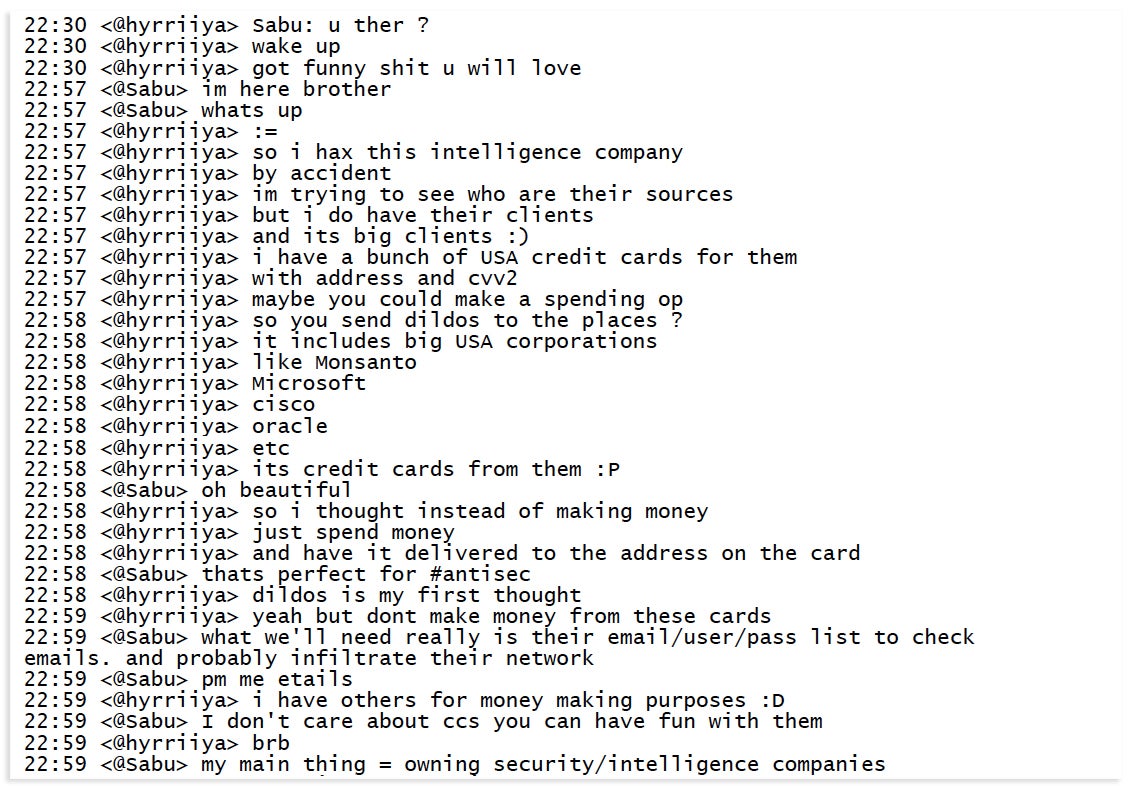
In a private chat, Monsegur asks Hyrriiya to provide him with access to Stratfor’s systems.
Hyrriiya’s letter to Hammond’s defense counsel pinpointed the chat logs that contain this initial interaction with Monsegur. The hacker suggested that Hammond’s defense request these files during the discovery phase of his trial:
“I would advise you to request all logs of the #antisec main channel on irc.cryto.net… I also spoke with Sabu at length in Private Message on irc.cryto.net, and as such, the FBI should have complete logs of my PMs with Sabu regarding the Stratfor hack as well.”
Although the letter was provided to the court, it’s unknown what role, if any, this confession played in the court’s sentencing decision. Hammond received the maximum sentence for one count of violating the Computer Fraud and Abuse Act (CFAA).
On Dec. 5, 2011, nearly 24 hours after the FBI should’ve learned about Hyrriiya’s breach of Stratfor, Hammond was contacted by Monsegur to set up the attack. Hammond was told in a private message from Monsegur that AntiSec would receive “complete control” of a “big intelligence company,” soon after identified as Stratfor.
At the time, Hammond, a gifted hacker and “flawed revolutionary” from Chicago, was widely regarded as the FBI’s most-wanted cybercriminal.
Monsegur sent Hammond unsolicited stolen credit card numbers belonging to employees at the IACP and Raytheon, an American defense contractor, according to the chat logs reviewed by the Daily Dot. The cardholder information precisely matches the stolen financial data given to Monsegur by Hyrriiya.
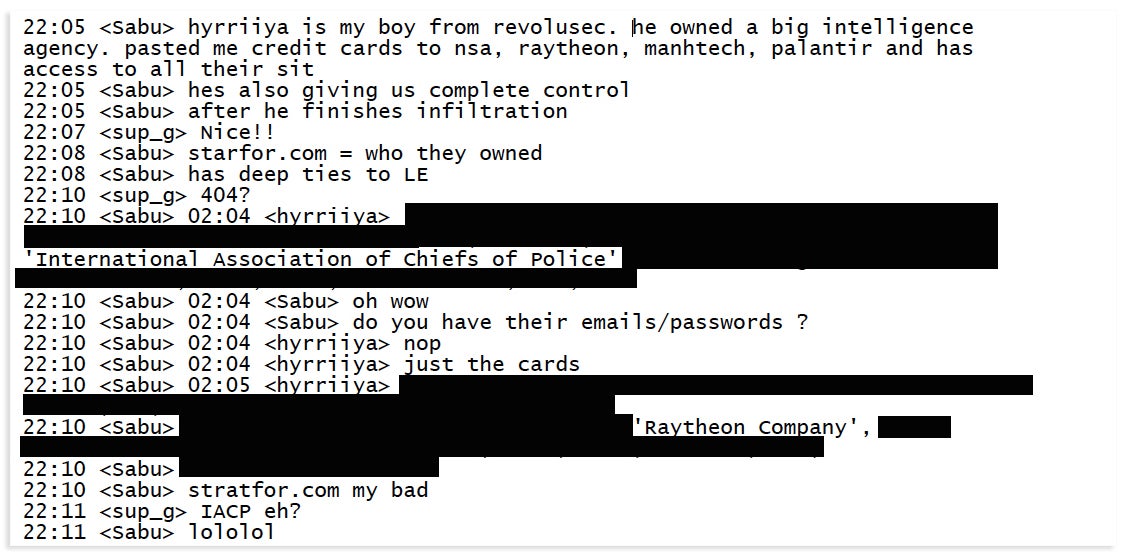
On Dec. 5, Hammond learns about Stratfor from Monsegur in a private message and is sent details for two stolen credit cards.
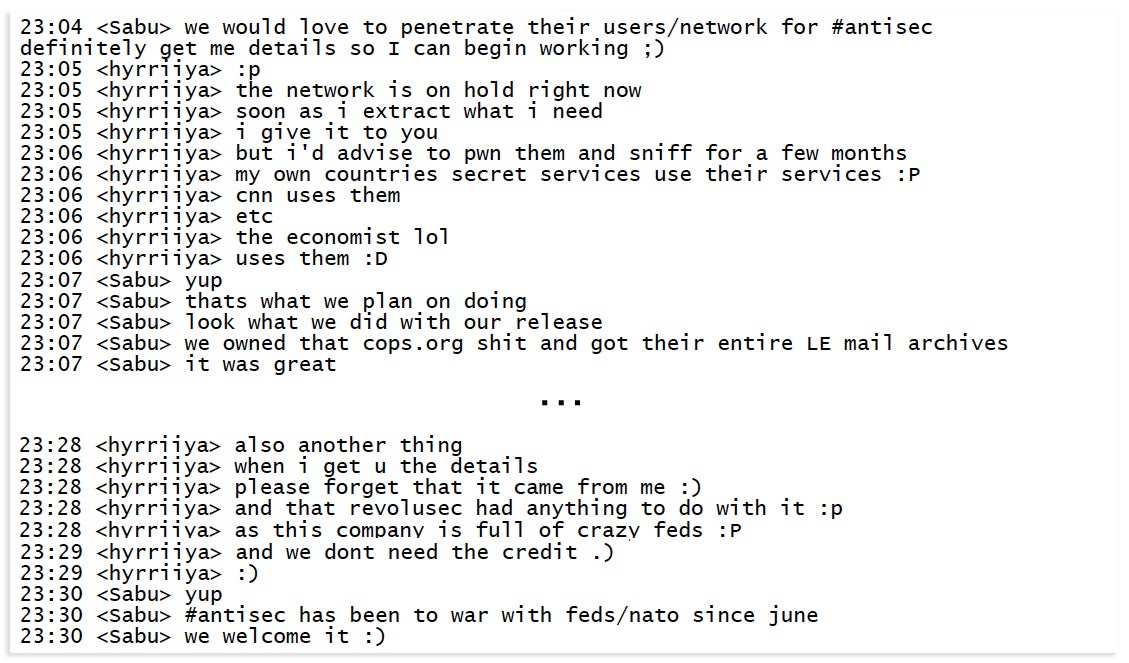
Approximately two hours later, Monsegur invited Hyrriiya into a private chatroom called “#!Sec,” then frequented by Hammond and other members of AntiSec. Immediately upon entering the room, Hyrriiya disclosed Stratfor’s vulnerability to the group. Monsegur instructed them to “keep sensitive conversations” contained to the #!Sec room.
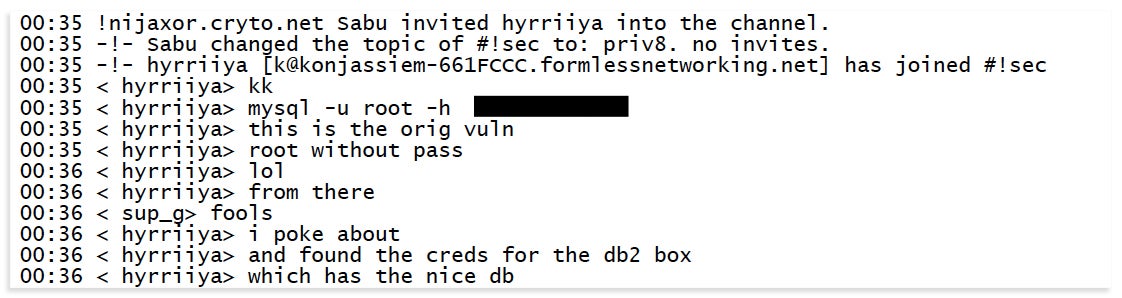
Shortly after midnight on Dec. 6, Hyrriiya is invited into a chatroom by Monsegur where he gives AntiSec access to Stratfor’s systems.
From here, the sequence of events is relatively undisputed. With Hammond equipped and as FBI agents reportedly watched on, AntiSec began plundering Stratfor’s financial information and personal records. Monsegur convinced Hammond and others to unknowingly transfer “multiple gigabytes of confidential data” to one of the FBI’s servers. That included the roughly 60,000 credit card numbers and records for Stratfor customers that Hammond was ultimately charged with stealing.
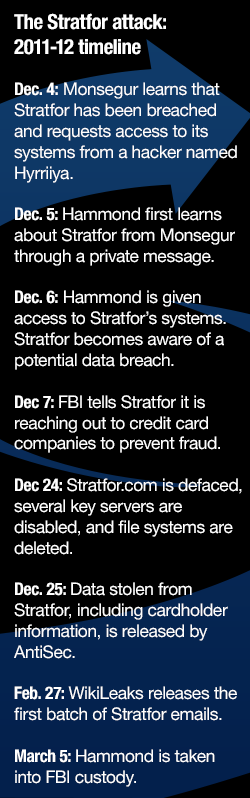
Matters escalated publicly on Dec. 24, the start of a two-day period referred to by the Anonymous community as LulzXmas. Hackers defaced Stratfor’s website and exploited Stratfor’s email addresses. Stratfor’s reputation suffered further later when some 5 million internal office emails were published by WikiLeaks as the Global Intelligence Files. Several of the company’s key databases were also deleted.
It is unclear whether the FBI—which had Monsegur under constant surveillance through keylogging programs, in-house cameras, and other methods—instructed him to coordinate the Stratfor hack, or if he acted on his own. According to legal experts, however, it is unlikely that Monsegur operated without the full knowledge, if not the actual direction, of the FBI.
“Anytime you’re dealing with an informant, the government is allowing someone to break the law,” says Hanni Fakhoury, staff attorney with the Electronic Frontier Foundation.
“But usually, it’s not, ‘Go do your own missions.’ It’s, ‘We’re going to tell you what to do.’”
At Monsegur’s sentencing late last month, his lawyer made clear the high level of supervision under which Monsegur operated.
“The government tracked everything he typed with a key-logging program,” attorney Peggy Cross-Goldenberg told the court. In addition to monitoring his Internet activity, the FBI installed a camera in his house to provide constant video surveillance. Judge Loretta Preska, who repeatedly praised Monsegur’s “extraordinary level of cooperation,” described the relationship as “virtual around-the-clock cooperation where Mr. Monsegur was sitting with agents.”
In retrospect, the connection between Monsegur and the federal authorities seems all-too obvious.
“[Monsegur] seemed to be encouraging members of Anonymous to take part in AntiSec, which raised questions about it being a honeypot, a form of entrapment for the feds,” recalls Parmy Olson, author of We Are Anonymous: Inside the Hacker World of LulzSec, Anonymous, and the Global Cyber Insurgency, considered by many to be the definitive overview of the hacktivist movement.
“I do remember this sense from doing the research and the reporting that it seemed very strange that someone who was clearly an informant played such a huge role in the hack on Stratfor.”
Monsegur declined a request for comment.
 Much as it seems clear that the FBI had a larger role in the attack on Stratfor than previously reported, whether the FBI’s actions constitute entrapment depends, Fakhoury says, on if the law enforcement agency “tricked” Hammond into committing the attack on Stratfor. That does not appear to be the case.
Much as it seems clear that the FBI had a larger role in the attack on Stratfor than previously reported, whether the FBI’s actions constitute entrapment depends, Fakhoury says, on if the law enforcement agency “tricked” Hammond into committing the attack on Stratfor. That does not appear to be the case.
However, former FBI agent Michael German, who specialized in domestic terrorism and covert operations, expressed concern over the details of the Stratfor case.
“It is improper for the FBI to use informants to instigate and direct criminal activity, particularly where there are innocent victims involved,” said German, the policy counsel for national security and privacy for the American Civil Liberties Union Washington Legislative Office. “I am concerned in this case that the FBI seemed more interested in inflating the potential criminal charges rather than mitigating the harm to innocents.”
The FBI’s apparent knowledge of the operation conflicts with its stated timeline. Based on its informant’s activities, it appears the agency at least implicitly allowed Stratfor to suffer significant and unnecessary collateral damage.
On Jan. 11, 2012, George Friedman, Stratfor’s chairman, issued a public statement in which he revealed that an FBI special agent had requested “in early December” the company’s cooperation in its ongoing investigation into the attack against the company. Specifically, the FBI urged Stratfor not to alert its subscribers about the theft of their cardholder data.
“I felt bound to protect our customers, who quickly had to be informed about the compromise of their privacy,” Friedman wrote. “I also felt bound to protect the investigation. That immediate problem was solved when the FBI told us it had informed the various credit card companies and had provided those companies with a list of compromised cards while omitting that it had come from us. Our customers were therefore protected, as the credit card companies knew the credit cards and other information had been stolen and could act to protect the customers. We were not compelled to undermine the investigation.”
Despite the company’s cooperation, the FBI’s contact with credit card companies did not stop hundreds of thousands of dollars in fraudulent charges.
As part of LulzXMas, hackers reportedly charged at least $700,000—much of it in the form of donations to charities—to the compromised credit cards of Stratfor customers. The FBI claims the hackers had stored such data on personal servers outside its reach. Given the sequence of events detailed in this investigation, it appears the FBI at some point lost control of its own sting operation or allowed the charges to place.
Stratfor ultimately settled a class-action lawsuit in June 2012 with its customers for a reported $1.75 million. An internal Stratfor memo obtained by the Daily Dot, drafted prior to the settlement, calculated the total cost of the attack at roughly $3.78 million, due primarily to losses from its newsletter subscription service, which had been its primary source of revenue. Stratfor declined to comment for this story.
For his various efforts, Monsegur was sentenced late last month to time served and one-year probation—a drastic reduction from the maximum sentence of 124 years he faced for his involvement in LulzSec hacks that targeted U.S. and foreign computer servers, including those of Sony, HBGary, Fox Television, and the United States Senate.
“Sabu avoided a prison sentence, but the consequences of his actions will haunt him for the rest of his life,” Hammond wrote from prison in a personal post published June 2. “Not even halfway through my time, I would still rather be where I’m at: while they can take away your freedom temporarily, your honor lasts forever.”
The FBI did not respond to multiple requests for comment.
Update: An FBI spokesperson reached out to the Daily Dot and Motherboard on Thursday afternoon to say that it would not comment further on Hammond’s case. “Frankly, this case got adjudicated,” she said. The spokesperson noted, in a general way, that the handling of informants, whom she referred to as “sources,” is conducted in accordance with the Attorney General’s guidelines.
Correction: The original version of this story incorrectly stated the maximum sentenced faced by Hector Monsegur. He originally faced 124 years for his role in LulzSec’s 2011 hacks.
Additional reporting by Kevin Collier, Andrew Couts, and Austin Powell
Photo by Brian Knappenberger | Illustrations by Jason Reed


